From OTPs and two-factor authentication to registering users’ trusted devices, knowing your users’ mobile phone numbers is an indispensable component of keeping user accounts secure. But what happens when someone fraudulently gains access to a user’s phone number?
This is not a hypothetical scenario but a growing threat that many smartphone users are unaware of. Attacks on SIM cards, such as SIM swapping — which we introduced in a previous blog — are growing more prevalent and more sophisticated, resulting in a rise in fraud and severe consequences for end users’ online security and privacy.
In this blog, we will delve into some of the emerging SIM card attack methods, break down advanced evasion tactics for SIM swapping, introduce the concept of eSIM, and provide an overview of some of the techniques Transmit Security uses to detect SIM swapping attacks.
SIM card attacks: the next generation
There are several ways to use a SIM card to obtain a user’s private information, including Simjacker, SIM swapping, SIM cloning, and WIB (Wireless Internet Browser) attacks, which we’ll review in detail in this section.
Simjacker attack
Simjacker attacks use a simple SMS message to send spyware to end users’ phones that enables hackers to open a backdoor that allows them to take over the user’s phone. An SMS message is sent to the target’s smartphone. Concealed within it is a link to a browser or a specific code that instructs the SIM card to divulge critical data or facilitate remote control of the device.
This operation is executed through the utilization of the S@T Browser, an integral component of the SIM Application Toolkit (STK) deployed by numerous mobile operators. Importantly, this process transpires discreetly, without the user’s knowledge.
Crucially, the Simjacker attack is not confined to a specific operating system, rendering all types of phones susceptible, including both Android and iPhone devices. The information extracted from the compromised SIM card encompasses vital details such as the cell ID, enabling attackers to determine the user’s location, along with specific device information like the International Mobile Equipment Identity (IMEI) linked to the handset.
The pilfered data is then relayed to a separate device, distinct from the one used to initiate the SMS, thus establishing a covert channel for the attacker. This breach grants malevolent actors the ability to eavesdrop on phone conversations, take off with prepaid credits, or even seize control of bank accounts tethered to the victim’s phone number.
SIM swap attack
SIM swapping enables attackers to take over an end user’s phone number and, as a result, gives them unbridled access to the victim’s calls, messages, financial accounts, and other sensitive information. The attacker does this by calling the user’s service provider and impersonating the end user in order to manipulate technical support into issuing a new SIM card. Once the process is complete, the provider will cancel and suspend the real SIM card.
This not only locks the user out of their phone but enables the attacker to steal the user’s phone number and link it to their own devices.
Evading security measures: a tactical approach
To overcome protections designed to detect fraudsters using a registered phone number that has been altered, attackers must take a calculated approach. If a bank demands a one-time passcode sent to the cardholder’s phone, the attacker may assert that the primary phone on file is no longer accessible due to a recent change in carriers. They may then offer a burner number, retrieve the text, and provide the code, effectively circumventing the service provider’s first line of defense.
Should the bank’s fraud detection system disallow texts to the burner, the attacker may anticipate a transfer to the fraud department. At this juncture, they may make a strategic retreat and disconnect, as the fraud department may prove equally unyielding. This protocol often culminates in rendering the card unusable, promising a callback within 24-48 hours that is inevitably directed towards the cardholder.
Advanced evasion tactics
To overcome fraud detection systems that employ multiple lines of defense against SIM swapping, such as transferring suspicious calls to the fraud department, two alternative avenues present themselves. The first entails initiating a SIM swap on the victim’s phone number through a convincing call to their carrier, citing a damaged, lost, or stolen SIM card. This endeavor demands extensive knowledge, including the potential need to navigate knowledge-based security questions or alternative verification methods, some of which can be obtained or learned by purchasing services on the dark web, as shown in the examples below.
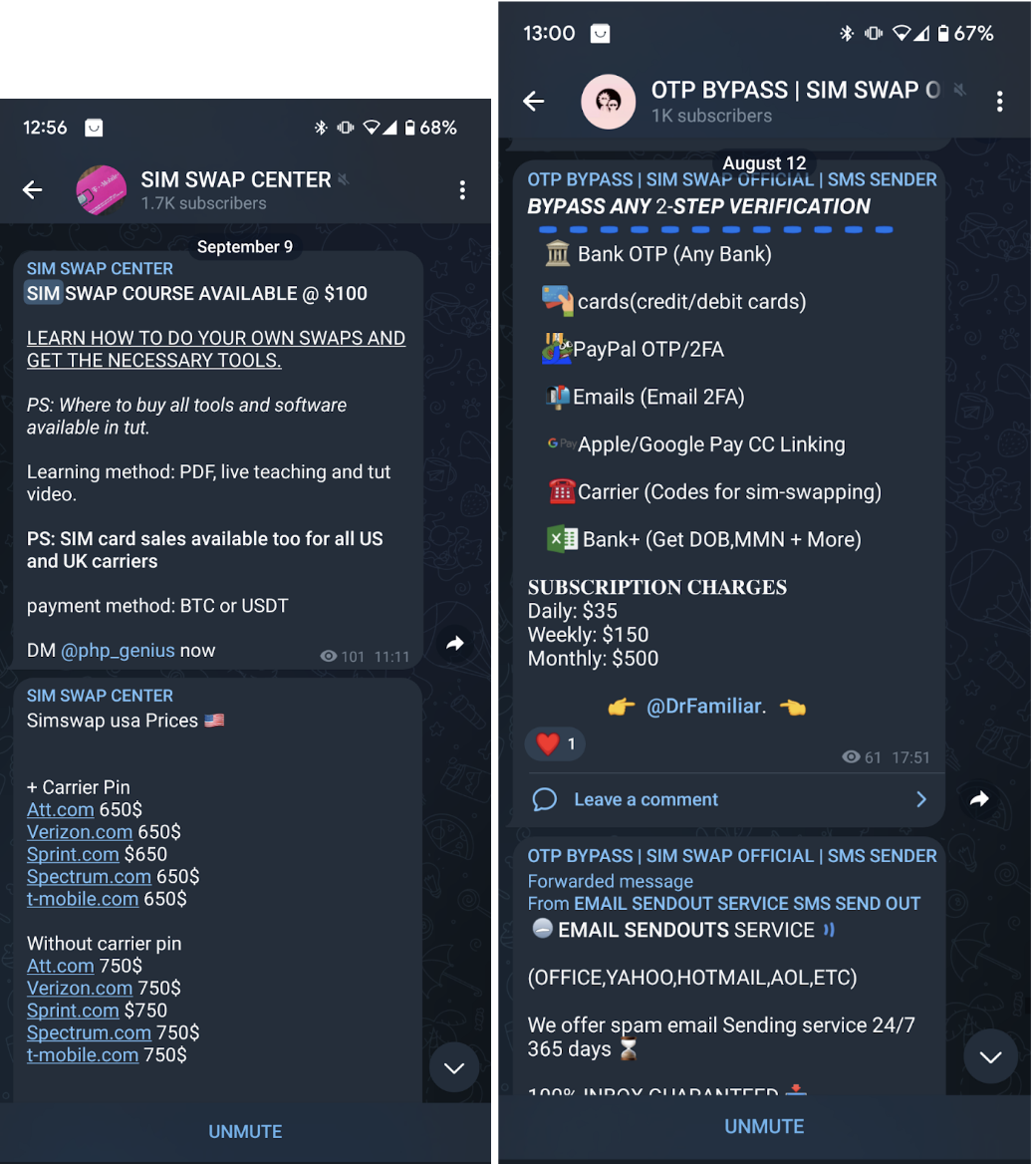
Figure 1 – Telegram channels found on the dark web offer SIM swapping tools
The second option requires a dual-burner approach. In this approach, the attacker engages the bank with the first burner, invoking a brief hold while ostensibly retrieving their cell phone. During this interval, the attacker employs the second burner, cleverly spoofing the phone number of the bank’s official toll-free support line.
Once the cardholder is on the line, the attacker can swiftly engage them, employing social engineering techniques to extract the elusive one-time passcode.
SIM cloning attack
Like SIM swapping, SIM cloning allows attackers to transfer the victim’s inbound calls and messages to the attacker’s phone and gives the attacker the ability to impersonate the user’s phone number while making calls, sending messages, and using the Internet — all without the legitimate user’s knowledge.
However, SIM cloning differs from SIM swapping in that attackers do not trick mobile operators into transferring SIM cards but use software to clone the target user’s SIM card, compromising the user’s legitimate card and redirecting control of the phone number to a device controlled by the attacker.
To do this, the hacker needs to gain access to their victim’s Ki code, a 128-bit value used in authenticating and protecting the SIMs on a GSM mobile network. If the hacker decodes the Ki code, they will be able to alter his victim’s chip and take over ownership of it, making it possible to clone the SIM card.
In the cloning process, the chip’s data is transposed onto a writable, programmable card that is not supplied by telecom companies but readily available in underground online markets. Accomplishing this feat necessitates specialized programs and applications, downloadable by attackers, to decrypt and duplicate the SIM data.
Wireless internet browser attack
The Wireless Internet Browser (WIB) toolkit was created by SmartTrust, a company that provides SIM toolkit-based browsing solutions to hundreds of mobile operators worldwide, including AT&T, Etisalat, KPN, TMobile, Telenor, and Vodafone.
The WIB toolkit was also designed to allow mobile carriers to provide essential services, subscriptions, and value-added services over-the-air (OTA) to their customers. OTA revolutionizes SIM card management by enabling remote communication, updates, and services. This client-server architecture encompasses an operator’s backend system, OTA Gateway, SMSC, wireless network, mobile equipment, and the SIM card itself. OTA SMS, while a powerful tool for swift SIM updates, can also be leveraged nefariously in peer-to-peer transmissions.
OTA allows remote configuration and management of SIM cards through specially crafted SMS messages. These SMS messages can exploit vulnerabilities in the SIM card’s WIB functionality, potentially providing unauthorized access to the victim’s mobile device.
Once compromised, attackers can execute various malicious actions, such as sending SMS, making phone calls, obtaining the victim’s location, launching browsers, and extracting the victim’s IMEI, all without the victim’s knowledge or consent, making OTA SMS services a vector for initiating and facilitating WIB attacks.
Unraveling wireless internet browser attack scenarios
In the WIB attack scenario, the assailant dispatches a malicious OTA SMS to the victim’s phone number, embedding WIB commands such as SETUP CALL, SEND SMS, PROVIDE LOCATION INFO, and more.
For example, when a victim’s device receives an OTA SMS with the “SETUP CALL” command, it instructs the device to initiate a phone call to a specified number without the victim’s knowledge or consent using the baseband operating system, which is responsible for interpreting and executing voice calls, SMS messages, and data connections.
It does this by utilizing an ENVELOP COMMAND to relay the OTA SMS’s Transport Protocol Data Unit (TPDU) to the WIB browser within the victim’s SIM card. Unlike standard text SMS procedures, the OTA SMS maneuver transpires silently, evading detection by application operating systems.
The WIB browser then executes the enclosed WIB commands, initiating corresponding PROACTIVE COMMANDS on the victim’s mobile phone, like setting up calls, sending SMS messages, or providing location information.
What is eSIM and what are its security advantages for SIM-based attacks?
An eSIM, or embedded SIM, is a new SIM card built into mobile devices that does not require a physical card slot. Unlike a traditional SIM card, which can only store one phone number and network profile, an eSIM can store multiple profiles and switch between them without changing the card.
An eSIM has many advantages over a physical SIM card, such as:
- It saves space and allows for smaller and thinner devices.
- It makes switching between networks and plans easier and faster without visiting a store or waiting for a new SIM card to arrive.
- It enables you to use multiple phone numbers on the same device, such as a personal number and a work number or a local number and an international number.
- It reduces the environmental impact of producing and disposing of plastic SIM cards.
Embracing eSIM technology can be a pivotal strategy for businesses to improve their defenses against SIM swapping attacks, and it also offers some security advantages over traditional physical SIM cards that can help mitigate other types of attacks like SIM cloning and SIMjacking.
Unlike traditional SIM cards, which can be physically swapped or stolen, eSIMs render physical removal and unauthorized access significantly more challenging. Moreover, eSIM activation typically involves QR code scanning or the input of a confirmation code, introducing an additional layer of security to safeguard user accounts.
However, businesses should be aware that the adoption of eSIM technology varies among device models and mobile carriers, and availability may vary by region. To ensure seamless implementation and compatibility with your user base, we recommend verifying device and carrier support for eSIM technology, which is essential for effectively bolstering your SIM swapping detection measures.
How Transmit Security can protect you from SIM attacks?
Detecting SIM attacks is a challenging job. To protect businesses from fraudsters who may attempt to bypass identity security protections through the use of compromised SIM cards, Transmit Security Research Labs has identified, created, and researched multiple ways to detect them.
One key indicator of a compromised SIM card is a suspicious change in the device’s MNC (Mobile Network Code). Transmit Security can detect device anomalies when the device has one or more MNCs. While a legitimate device should have no more than two or three MNCs, cases when we see devices with four or more MNCs could be a good indication of SIM swapping.
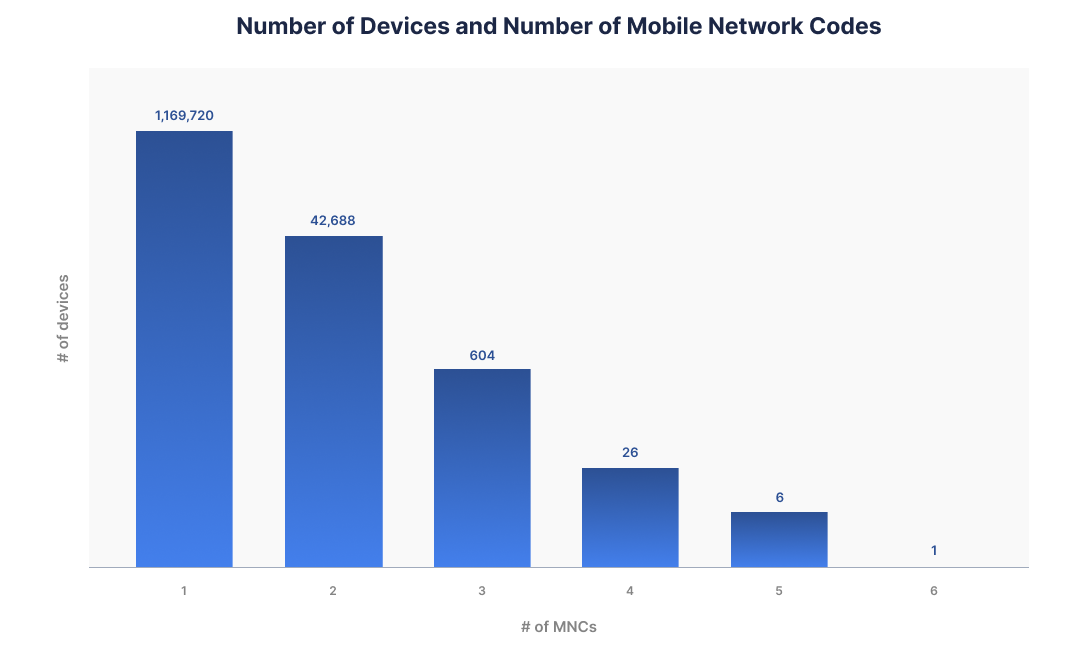
Figure 2
In the image above, we can see how Transmit Security detects the number of MNCs per device, based on data from an American financial institute that leverages Transmit Security. This data also allows us to track multiple changes in the number of MNCs per device in a short period, which may suggest a compromised SIM card.
A mismatch between the SIM country and the cellular network country can also indicate that a device’s SIM card has been compromised. While some users traveling abroad may change to a local SIM card, many others do not, especially users in the US, where we have detected the presence of US SIM cards in 28 different countries, as shown in the example data below from the same American financial institute.
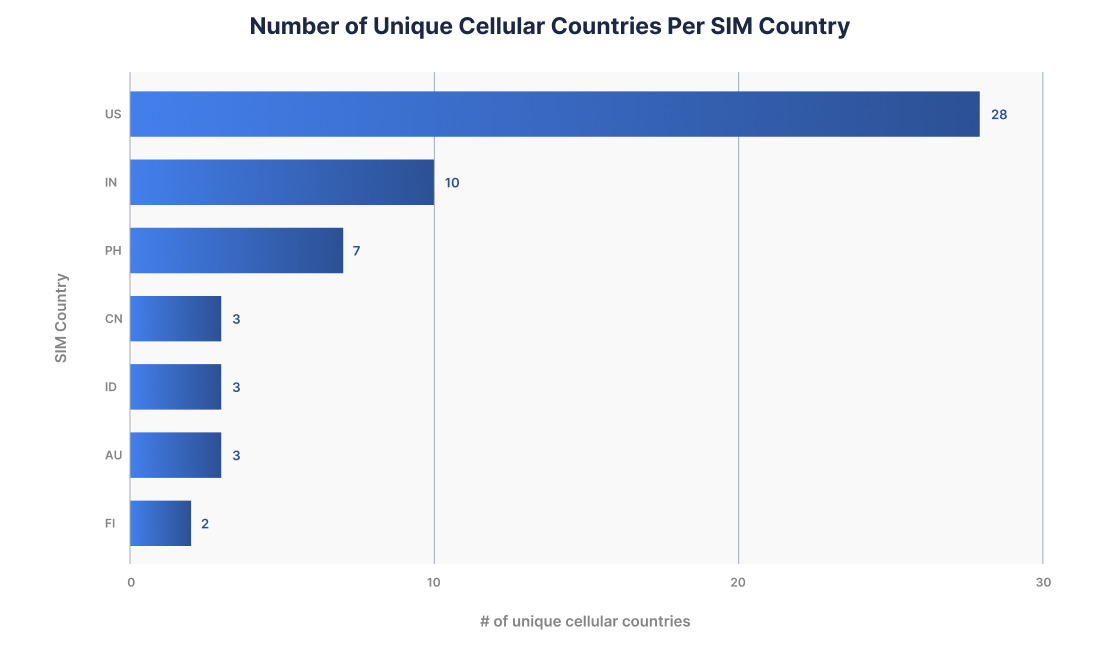
Figure 3
Thus, if a user with a US cellular network suddenly switches to a SIM card of another country, it could be combined with other risk signals as a potential indicator of a compromised SIM card.
Conclusion
SIM swapping is an identity theft threat that can compromise your end users’ online security and privacy. By stealing a user’s phone number, an attacker can gain the keys to the kingdom for their victim’s accounts, resulting in a high risk of account takeover (ATO), and pose as their victims to register new accounts. As a result, it’s crucial that businesses take action to detect SIM swapping and employ secure registration methods with Identity Verification Services and data validation capabilities to reduce the risk of new account fraud.
By understanding the types of SIM swapping attacks that are out there and how to detect them, businesses can help prevent ATO, unauthorized transactions, and other types of fraud on their platform. To find out more about how Transmit Security’s Detection and Response Services can help your business detect SIM swapping attacks, contact Sales for a free demo.



