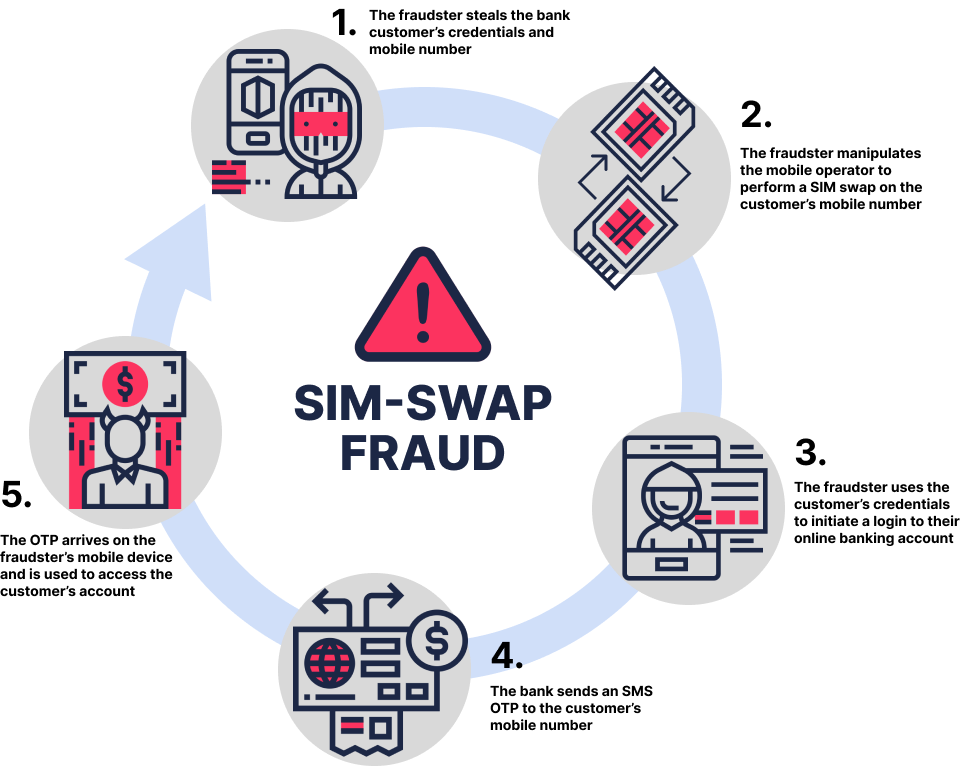
Think of the breadth of information stored on your phone and the activities that could be performed simply by unlocking it. With complete control over your phone number and PIN, a fraudster could make and receive calls, texts and emails, send and receive cryptocurrency and access the many additional accounts that are protected by one-time passwords (OTPs).
This is what’s at risk with SIM swapping attacks — an increasingly popular scam that allows cybercriminals to transfer your phone number, contacts, texts and PIN number to their device. According to the FBI, reported cases of SIM swapping grew 500% from 2021 to 2022, and the alarming increase has led to growing scrutiny over how mobile carriers register new SIM cards. This blog post will explain how SIM swapping works, how enterprises can prevent losses related to SIM swapping and how identity verification can help mobile operators easily and securely register new SIM cards.
What is SIM swapping?
A Subscriber Identity Module (SIM) card is a small, portable memory card used by a mobile cellular device as a portable key to identify and authenticate its user to a mobile network. A SIM card allows users to make and receive calls, send text messages and use mobile data services on the network. If the SIM card is damaged or the device is lost, they can request to transfer their phone number to a new device by calling their mobile operator, who will typically validate their identity with knowledge-based questions, such as the device PIN or the last four digits of their social security number (SSN).
In a SIM swapping attack, fraudsters use leaked or stolen SSNs and personal data about a user to masquerade as the device owner and convince the user’s mobile operator to transfer the SIM card to a device owned by the attacker. With full control over the user’s device, fraudsters can intercept OTPs to gain access to accounts protected by multi-factor authentication (MFA) or obtain information that could be used to access the user’s other accounts. This broad access enables fraudsters to steal users’ identities in a way that is difficult to recover from.
New regulations to protect end users from SIM swapping
Although much of the media attention on preventing SIM swapping centers on how end users can protect themselves, the gateway fraud enabled by SIM swapping also puts banks and other businesses that guard sensitive information about their users at risk.
However, putting the onus of protecting accounts on users presents a high risk for businesses that could experience fraud losses if users do not follow best practices. In addition, as mobile network providers begin to offer customers financial services as part of their offerings, they will need to comply with the same KYC and AML regulations that apply to banks and other financial institutions, which requires proof of identity for secure account opening.
As a result, over 150 countries now require proof of ID for mobile SIM registration, including the registration of eSIMs — digital SIMs that give customers the flexibility to activate a plan or switch between networks from anywhere, without waiting for a physical SIM card to arrive.
For eSIMs, validating IDs to comply with these regulations provides a special challenge for mobile operators, as one of the key benefits of eSIMs is the fast, automated provisioning of new SIM cards from anywhere. Without a solution that quickly verifies the validity of customers’ IDs online, customers will be unable to enjoy the convenience of eSIMs and businesses will lose a key competitive advantage — especially as eSIMs become more popular and newer phones begin to phase out trays for physical SIM cards.
How Identity Verification prevents SIM swaps
If traditional methods of verifying the identities of users who request transferring SIM cards to new devices are not enough to provide protection against SIM swapping, what measures can businesses and mobile operators take to prevent this increasingly popular attack? As Forbes recently noted, the answer may lie in identity verification — a service that can provide secure onboarding, account recovery and step-ups for high risk events that could enable identity theft.
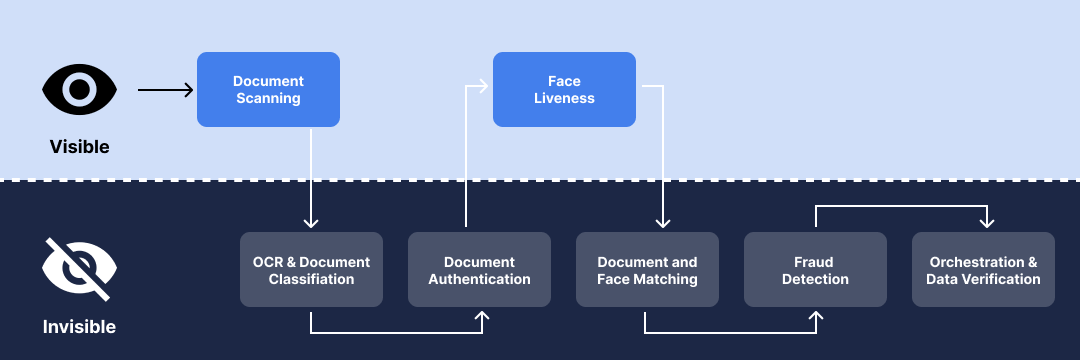
On the Transmit Security Platform, Identity Verification simplifies this process by providing users with step-by-step instructions to complete three simple steps:
- Gathering any documents required for verification
- Scanning the documents with their mobile device
- Taking a selfie of their face
Behind the scenes, a range of capabilities enable Identity Verification to quickly and thoroughly check for signs of fraud. With a large database of supported documents from around the world, Transmit Security leverages deep knowledge of document formats, fields and security features to inspect documents for signs of tampering or forgery. Selfies are then examined to not only verify that the document photo matches the user’s selfie, but also detect any signs of spoofing, such as the use of cutouts, masks or screen printouts.
This process is the same for both physical SIMs and eSIMs, providing mobile operators with a solution to comply with KYC and AML online and enabling them to improve customer service without introducing compliance or security risks.
Identity Verification also benefits from native integration with Detection and Response and Identity Decisioning, as well as Data Validation, another crucial aspect of KYC. These additional security checks afford businesses better protection via passive checks for bot activity, IP spoofing or other risk signals, enables background checks with third-party databases and allows businesses to easily implement custom rules, such as blocking users who do not meet minimum age requirements or challenging users with expired IDs.
This process is fully automated and can scale for enterprises, saving the cost and time of performing manual ID checks. In addition to helping mobile operators validate users’ identities during SIM registration, it can be used to help banks and other businesses step-up users who have recently changed devices and are enacting multiple activities, such as changing passwords, making large withdrawals or applying for loans, that could be used to drain user accounts, lock users out of their accounts or both.
It may also provide a better experience for end users in these scenarios, as knowledge-based questions or mobile PINs can be easily forgotten. Rather than relying on answers that may change or codes that can be lost over time — locking users out of their accounts — users can easily produce identity documents that attackers would not have access to.
Identity Verification supports a wide range of documents worldwide, which are checked for numerous security features to prevent fraudsters from using forged or altered documents or circumventing liveness checks with innovative new techniques.
Identity Verification on the Transmit Security Platform
As the only identity security platform that provides a full suite of natively integrated services for identity verification, detection and response, robust user management, orchestration and a wide range of authentication methods, Transmit Security enables businesses to not only implement industry-leading identity verification services, but centralize and consolidate identity security and management. To find out more about Identity Verification, check out the service webpage or read more in this blog post on secure, frictionless onboarding.



