In our last blog on private browsing, we broke down some of the use cases, risks, and indicators for private browsing mode features on modern web browsers, such as Chrome’s Incognito mode and Firefox’s Private Windows. Similar to these features, anti-detect browsers allow users to browse the internet without being tracked or profiled. However, anti-detect browsers go a step further by not only eliminating traces of user activity but changing identifying attributes — creating even greater potential for abuse.
In this post, we’ll provide an overview of some of the most popular anti-detect browsers, how fraudsters can abuse them, and some key detection methods Transmit Security uses to identify the misuse of anti-detect browsers without blocking legitimate users.
Anti-detect browser types and capabilities
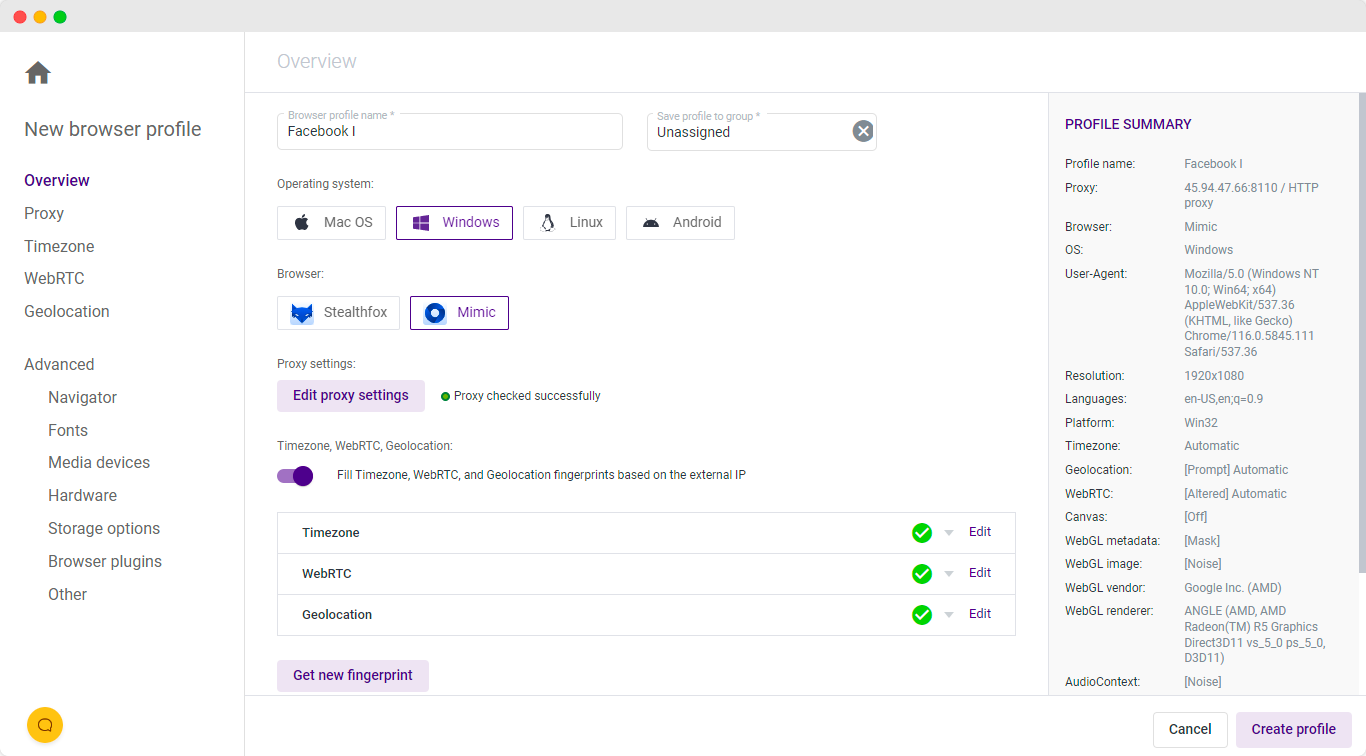
As key anti-detect browsers like Incogniton, Che Browser, GhostBrowse, and Indigo become increasingly relevant, it’s crucial that businesses understand why they’re used and what they’re capable of — both by legitimate users and fraudulent ones.
Some of the main anti-detect browsers in use today include:
- Incogniton: This anti-detect browser is used for managing multiple accounts with unique digital fingerprints. It offers features like automated operations and cookies management.
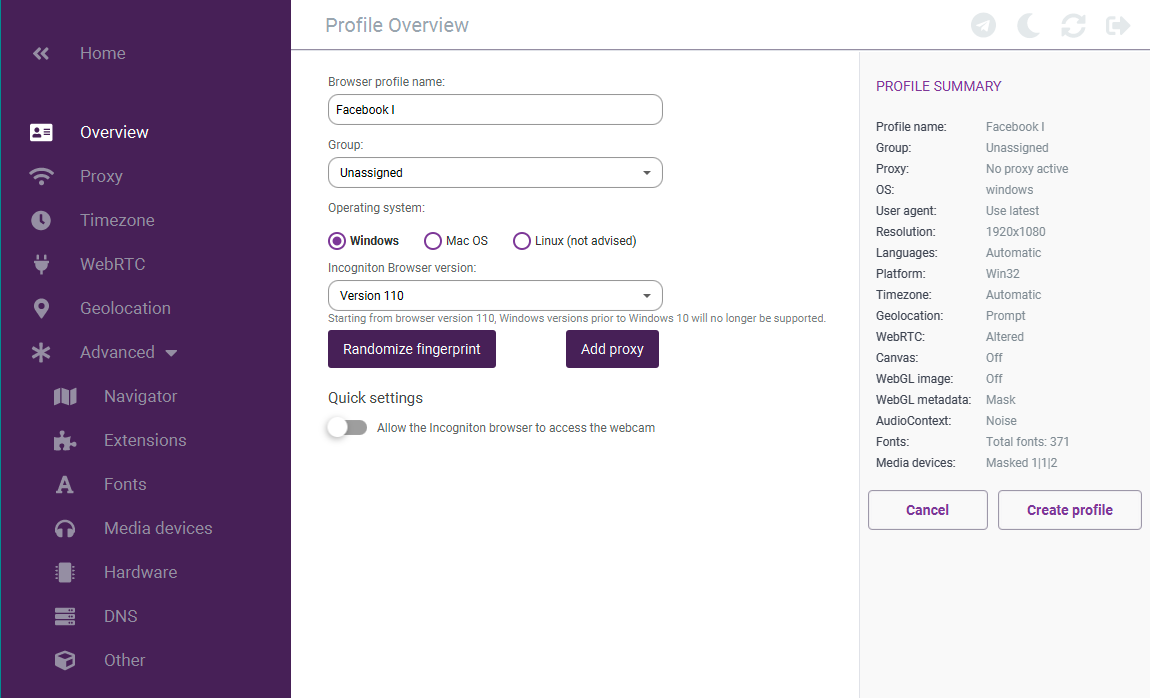
- Che Browser: With the ability to change browser and hardware fingerprints, Che Browser facilitates the creation of diverse accounts on the same device without triggering account bans designed to block new account fraud. It also enables users to alter the time between their actions to prevent being flagged by security mechanisms.
- Ghost Browser: Designed for a streamlined browsing experience, Ghost Browser allows simultaneous logins to websites with multiple accounts with dedicated workspaces and protects against canvas fingerprinting, font fingerprinting, WebRTC leaks and WebGL tracking.
- GoLogin: A tool for controlling digital fingerprints, GoLogin spoofs web parameters to avoid triggering anti-fraud systems and provides free proxies and shared proxy servers to mask IP addresses.
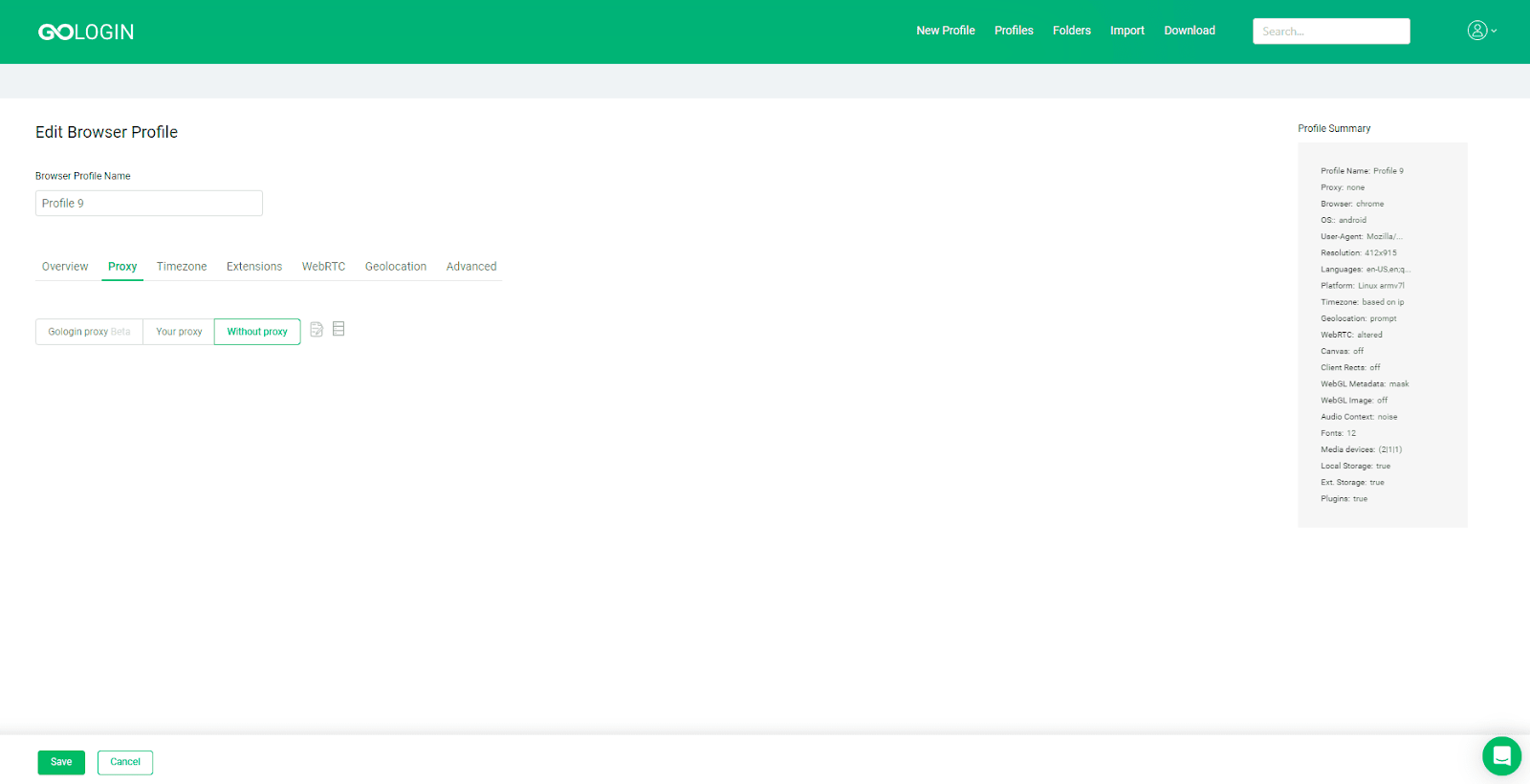
- Indigo Browser: Useful for online affiliates, Indigo Browser has an extensive database of user fingerprints that can be continuously adapted and lets its users work from an unlimited number of computers.
Use cases and risks of anti-detect browsers
Whereas anti-detect browsers have legitimate use cases such as social media management, affiliate marketing, safeguarding user data and boosting productivity, they also have significant potential for abuse, putting businesses at risk of:
- Device emulation
- New account fraud
- Credential stuffing
- Web scraping
- Inventory hoarding
As a result, it’s crucial that enterprises are able to detect the use of these browsers to prevent fraud losses and protect their users.
Detection using abstract fingerprints
Although anti-detect browsers are designed to alter device fingerprints and other identifiers, they may still be detected through examining their abstract fingerprints: a unique set of characteristics or identifiers that these browsers leave behind when interacting with websites.
Abstract fingerprints can include details about the browser version, operating system, screen resolution, installed plugins and more. Each of these elements contributes to creating a unique “fingerprint” that can be used to track or identify users across different websites.
Our research team uses the following process to identify and understand abstract fingerprints from anti-detect browsers:
- Browser inspection: By using popular anti-detect browsers and observing the information they send to websites, we can gain insights into the types of fingerprints these browsers are designed to mask or alter.
- Reverse engineering: This involves deconstructing the browser software to understand its inner workings. By examining the source code and functionality, we can identify the techniques used to manipulate or hide browser fingerprints.
- Behavioral analysis: Analyzing the behavior of these browsers under different conditions and configurations can reveal patterns or anomalies in the fingerprints they produce.
Leveraging browser research to improve detection
Applying their research into the patterns and anomalies anti-detect browsers leave behind, the Transmit Security Research Lab uses advanced techniques like anomaly detection and advanced fingerprinting analysis to identify these browsers in action. This includes:
- Monitoring irregular web traffic: Anti-detect browsers often modify certain browser characteristics to avoid detection. This can result in unusual user-agent strings or erratic browser behaviors. For example, a browser might exhibit behaviors that are inconsistent with its reported type. By monitoring for these irregularities, the research team can identify potential use of anti-detect browsers.
- Canvas fingerprinting with anomaly detection: Canvas fingerprinting is a technique that analyzes the unique way each browser renders graphic content on a web page. Anti-detect browsers often provide features to alter their canvas fingerprints to avoid detection, but this alteration can create anomalies in the rendering process, such as rendering graphic content differently than expected for its reported type.
- Browser plugin enumeration: Anti-detect browsers might have an unusual combination of plugins that deviate from the expected plugin profile of regular browsers. For example, a browser might lack certain common plugins or have plugins that are uncommon for its reported type. By enumerating the plugins of a browser and comparing them to the expected profile, the research team can detect the potential use of anti-detect browsers.
These anomalies serve as key indicators for our Security Research Lab for the use of anti-detect browsers, enabling businesses to better determine when their users are not who they claim to be.
Distinguishing fraudulent from legitimate usage
While spotting anti-detect browsers is crucial for businesses to remain secure, businesses may require flexibility in their security controls that help to distinguish legitimate from fraudulent use of these browsers and customize risk decisioning based on these signals rather than blocking all anti-detect browser users.
Transmit Security provides this flexibility through the use of multiple detection frameworks to calculate risk scores, with explainability into the top reasons that requests are flagged as suspicious and build profiles of users’ behavior over time. This allows businesses to determine if an individual’s anti-detect browser usage is accompanied by other risk signals or patterns of legitimate usage, such as typical data usage or activity that is consistently within normal hours.
Risk and trust decisioning can then be customized according to each business’s unique CX and security needs by decreasing or increasing the importance of anti-browser detection when calculating real-time recommendations for handling requests.
Ongoing protection through dynamic detection
To ensure their ongoing efficacy, anti-detect browser vendors continuously adapt their capabilities, requiring security teams to evolve their detection capabilities along with them. As a result, teams must invest in dynamic detection that is continuously updated to keep up with new anti-detect techniques and quickly adapt their controls to keep up with these changing tactics.
By continuously analyzing anti-detect browsers to improve detection and providing flexible options for blocking and challenging their usage, Transmit Security helps enterprises block fraud while reducing friction for trusted users and provides low-code tools that help teams quickly build and adjust security mechanisms.
For more information about how our Security Research Labs helps enterprises protect against evasive tactics, check out our previous blogs from security researchers on ML-based anomaly detection, or contact Sales to find out more about how Transmit Security can help secure your business.



