Privacy has become a paramount concern for Internet users in today’s digital world. As a result, web browsers have introduced features like private browsing mode to offer individuals a sense of security and anonymity while browsing the Internet.
However, as with any technology, there are potential misuse cases associated with private browsing mode that enable fraudsters to evade detection. This blog post explores the private browsing mode detection concept and sheds light on potential fraudulent use cases.
Understanding private browsing mode
Private browsing mode — also known by various names like Incognito mode (Chrome), Private Window (Firefox), or InPrivate browsing (Edge) — is a feature offered by most modern web browsers.
In addition to these mainstream browsers, dedicated private browsers such as Brave, Tor, and Avast Secure Browser focus on providing users with enhanced privacy features. Private browsing allows users to browse the Internet without leaving traces of their online activities on the local device, as it prevents the browser from storing cookies and saving browsing history or other temporary files.
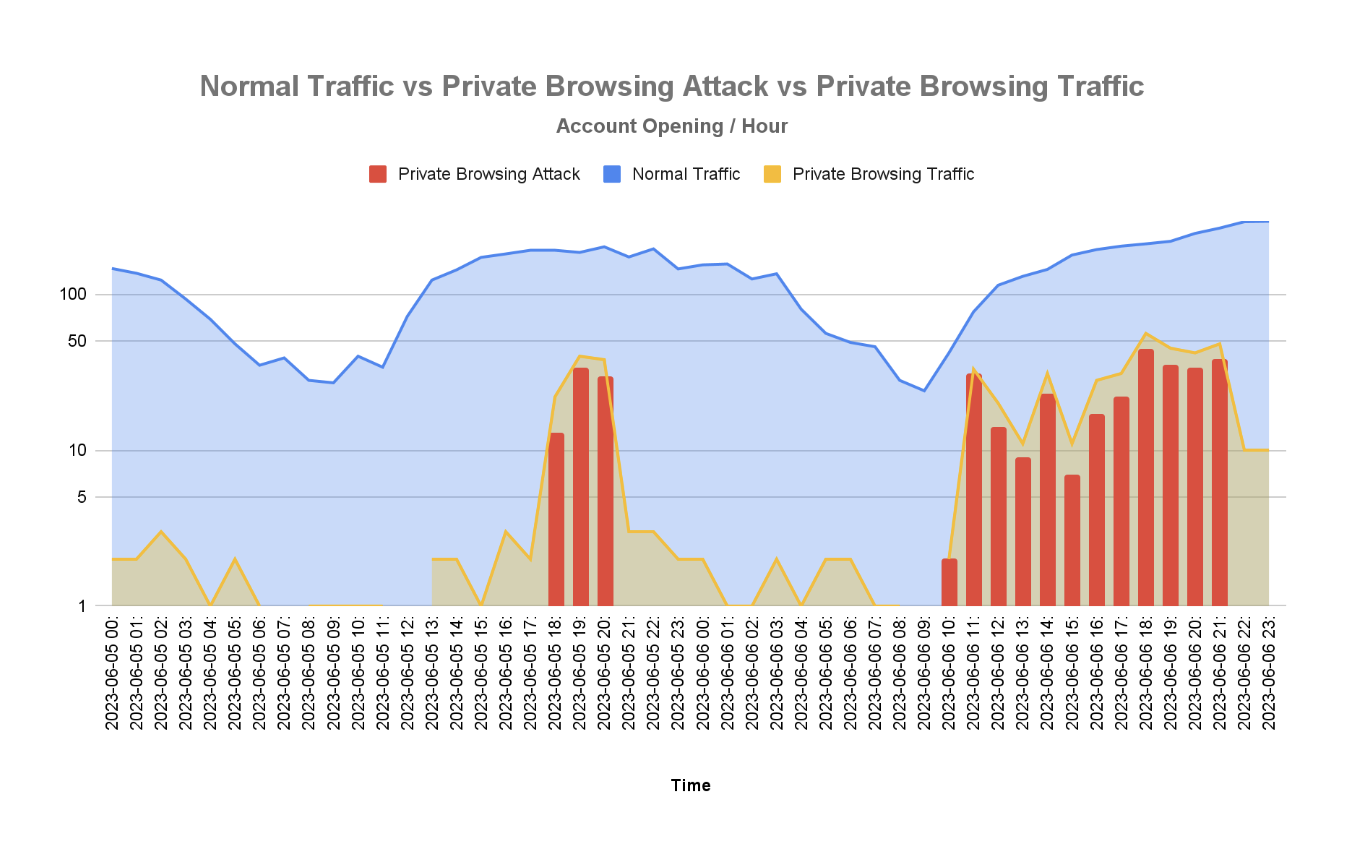
Although this is an advantage for users who wish to opt out of targeted ads and user tracking for marketing purposes, it also weakens the efficacy of device fingerprinting by randomizing browser attributes. This makes it harder for security teams to detect trusted devices as well as known malicious ones — two key signals used to secure accounts.
Data points and techniques used to detect private browsers
There are several methods that websites can use to detect if a user is browsing in private mode. As shown below, browsers differ in data points, reinforcing the suspicion that the end user is using private browsing. Chromium-based browsers send unique data for private browsing, such as navigatorStorageEstimate and performanceMemory, while Firefox browsers send ServiceWorker data.
Researchers can also use other techniques and data points. For example, by looking at a browser’s plugins, they can determine whether the end user is using one of the private browsers on the market.
Another method for detecting private browsing is a CSS history sniffing attack, which detects when sites are not added to the user’s browsing history. Researchers can also check if the browser’s IndexedDB throws an InvalidStateError, which happens when private browsing mode is enabled.
In addition to the techniques mentioned above, our Security Research Labs are continuously researching and developing other detection methods. As technology evolves, so do the methods for detecting private browsing.
Detecting private browsers with security research and threat intelligence
Although websites can potentially identify and prevent fraudulent activities by detecting if a user is browsing in private mode, it is essential to note that this is not in itself an indicator of fraud, as private browsers may also be used by legitimate customers. In addition, private browsing detection is not foolproof, and there may be ways for users to bypass these detection methods.
Ongoing security research and threat intelligence are essential for staying up-to-date with the latest techniques and methods for detecting private browsing. By continually studying and analyzing the behaviors and characteristics of private browsing modes in different browsers, examining browser and device attributes and conducting extensive testing, researchers can identify patterns and indicators of private browsing.
Conclusion
Private browsing mode has its pros and cons. While it empowers users with increased privacy and anonymity, it can also be exploited for fraud. Being aware of the data points that can indicate private browsing and the importance of security research and threat intelligence in this field can help businesses identify and prevent fraudulent activities.
By striking a balance between privacy and security, we can ensure that private browsing mode continues to serve its intended purpose without being used as a tool for fraudulent activities. This can involve evaluating patterns related to cookie handling, local storage, cache usage and file system access.
Additionally, continuously researching and refining detection methods based on evolving privacy expectations and technological advancements can help ensure that private browsing mode continues to serve its intended purpose without compromising security measures.
To find out more about the research Transmit Security’s in-house Security Research Labs are conducting on private browsing detection, emerging attacks, and other risk and fraud detection methods, check out our blogs on how Detection and Response detects user anomalies with advanced machine learning or read our case study on how a leading U.S. bank gained a 1300% return on investment by reducing fraud losses and consolidating cybersecurity with Detection and Response.



