Looking back on my career in Customer Identity and Access Management (CIAM), I’ve seen a lot of change, especially over the past few years. From cloud-native services and privacy regulations to cryptography and secure messaging protocols, modern identity, done well, requires multiple layers of security design, architecture and process to get it right.
By necessity, CIAM has evolved to confront the ever-changing nature of digital identity risk and fraud — now growing at a rapid clip. The cost of account takeovers (ATO) in the US has risen 500% since 2017, according to Juniper Research. Equally concerning, a 2022 Javelin study shows the volume of account opening fraud jumped 109% YoY.
It is easy to see why identity and cybersecurity investments are surpassing double-digit growth. In the same report, PWC reveals 75% of executives say too much organizational and systems complexity leads to cybersecurity and privacy risks. To manage it all, cyber professionals are in high demand but short supply, with a current shortfall of 3 million positions globally. When you couple this with the explosion of digital services and apps we all use today, hackers are enjoying expanded and ripe hunting grounds.
In this article, I’ll explain how fraudsters are defeating or bypassing existing CIAM methodologies and how modern approaches to identity can improve security outcomes. By the end, you’ll have a clear picture of what’s needed to prevent today’s complex ATO fraud and how to bring more effective CIAM technologies to bear. I’ll also link you to a recent webinar that covers this topic but with different proof points, so you’ll find both illuminating.
The gap between identity and cyber
Many would argue that identity and cybersecurity are two sides of the same coin, but the lines are blurring. After all, identity includes strong cryptographic trust, secure messaging protocols and a history of advanced data sharing and privacy influences. Does that mean identity should be perceived and implemented as a cyber function? It would appear so, but we can readily point to security gaps in identity that suggest we must rethink our approach to CIAM.
Let’s start with authentication, a core feature of CIAM. The most widely-used authentication modality is targeted by 61% of cyber breaches, according to Verizon’s 2021 DBIR. Of course, I speak of the humble password — phishable, leakable, interceptable, guessable and key-loggable. Isn’t it curious that such an ineffective access management function hasn’t met its demise, even though we have better, more secure alternatives?
Of course, we add extra defense layers to bolster the insecure password. Initially, two-factor authentication (2FA) was a formidable antidote, but this is no longer the case. Classic 2FA, SMS OTPs, hardware-based OTPs and authenticator apps all suffer from advanced, but highly commoditized, intercept and phishing attacks. Automated crimeware-as-a-service platforms are now an industry unto itself. The ease with which 2FA can be wholly neutered makes for sobering reading.
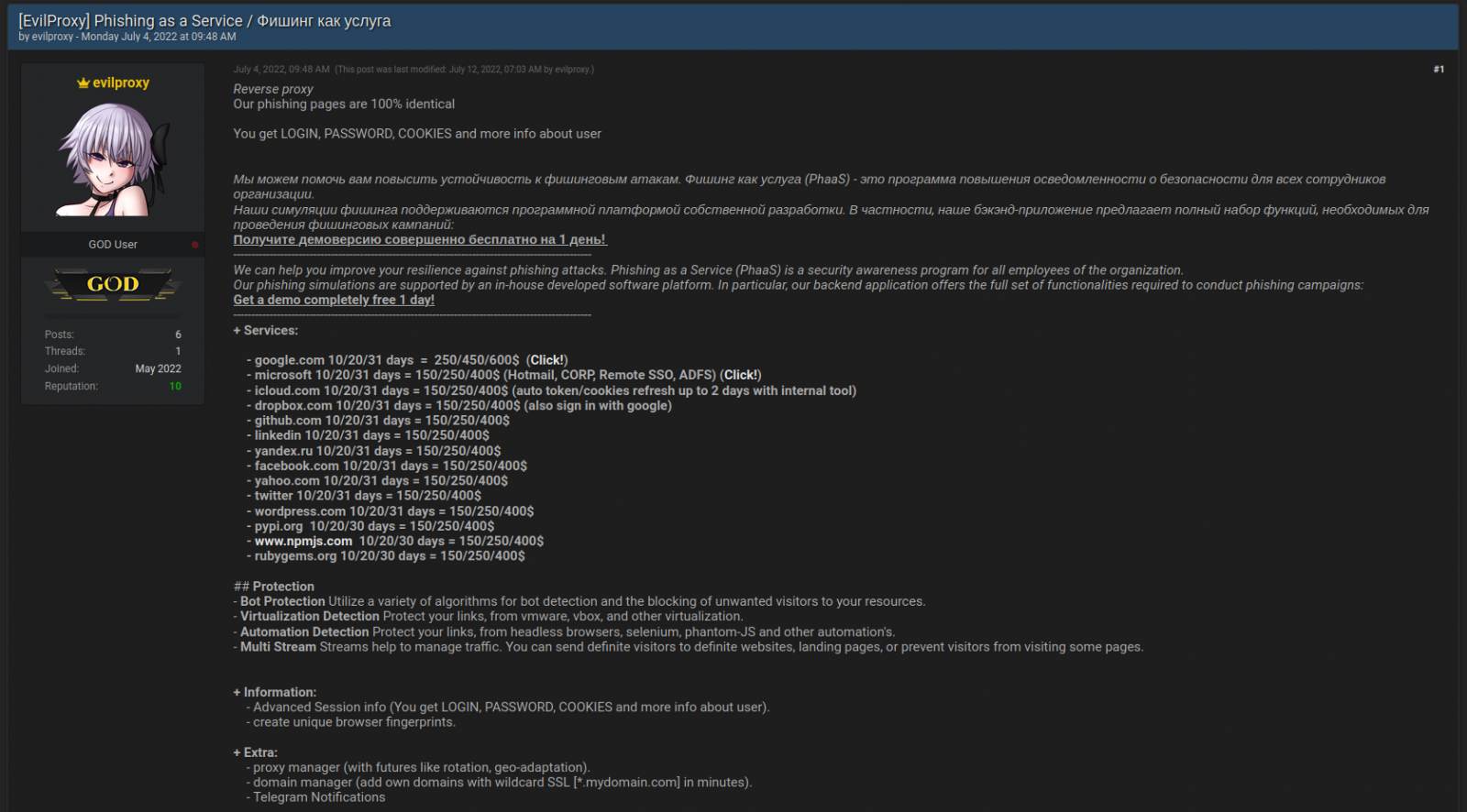
Case in point: EvilProxy, a phishing-as-a-service platform, is currently making its rounds in the media. Most notably, this turnkey reverse proxy service makes sophisticated ATO fraud incredibly easy for low-skill hackers who don’t know how to set up a reverse proxy. With little effort, they can intercept the session cookies containing authentication tokens, bypass 2FA and log into accounts appearing to be a legitimate customer.
Passwordless is just the start
Passwordless MFA, with its phishing-resistant attributes and ease of use, makes this burgeoning modality the new gold standard in authentication. On-device biometric authentication based on the FIDO2 protocol obliterates the vast majority of attacks that target shared secrets like passwords and OTPs. But even the strongest form of authentication won’t stop session hijacking, for example.
So let’s go beyond the act of authentication and look at the broader perspective of application access. What role can CIAM play in protecting customer accounts across the full identity lifecycle? Consider the moments after a customer logs in and starts using an application. Every application is built differently, and this is the moment when many CIAM systems become clueless.
Risk & trust in the post-authentication vacuum
To start, let’s call out the fact that authentication is a point-in-time event. Post authentication, users operate in an extended time-bound session that has been imbued with the context of this singular trust event, at the time the user logged in. So what happens with session trust from this moment onwards? Naturally, the level of trust declines because there’s a potential for risk to enter the equation with every passing second.
As evidenced by EvilProxy, fraudsters can invade customer accounts during an active session, not just at login. This is the very reason we need modern CIAM systems with wired-in account protection that provides real-time risk assessments and interdiction to stop digital identity fraud at any point in time — throughout the identity journey.
Be careful, however. This is where the lines are blurred between cyber and identity. You may already have security in place that looks for risk and trust signals, detects malware, trojans and injected payloads. But most likely, these tools are designed to protect your applications, not your identity profiles and customer accounts. Sure, you could try to integrate multi-vendor solutions, but it’s unlikely to work. Disparate technologies lack the interoperability and visibility you need to secure the full identity lifecycle.
Context matters at every point in time
CIAM can solve this problem but only if context-aware security is built into the fabric of an end-to-end identity platform. You must be able to see and respond to risk if, for example, the user changes their account details, exhibits bot behavior, appears with a new IP address, a new device, a different browser or initiates account recovery.
To achieve this, you need a powerful orchestration engine that can correlate hundreds of signals, evaluate the data along with the latest threat intelligence, apply machine learning and score the level of risk and trust — all to make accurate access decisions in runtime.
Stepping back to the academic view, this concept falls broadly under the umbrella of Continuous Adaptive Trust (CAT), an approach recommended by Gartner. CAT requires real-time risk and trust assessments to discern known good behavior versus bad behavior in the context of the full user session and all that we know about the customer. The idea being, trusted users can be rewarded with low friction access, while suspicious behavior or risk signals trigger difficult-to-defeat authentication challenges or denial of access. The ultimate goal is better customer experiences (CX) and stronger security.
Adaptive trust: easier said than done
This all sounds good on paper; the theory is certainly sound. Unfortunately, this concept has barely gained traction in the real world simply because the capacity to weave threat and fraud intelligence systems within the fabric of identity and access management has been complex and disconnected. A sliver of intel over here and a user action over there; this data is of little use without a holistic solution that can pull all of the pieces together.
In order to dynamically respond to all that’s happening within the full context of the user session, CIAM functionality must work in concert. If you try to stitch together cyber and identity solutions from different vendors, it won’t be easy and there’s no guarantee of success. It takes design, engineering, time and money to bring these concepts together and continually make improvements as the threat landscape changes. Recognizing this marks a key inflection point for CIAM.
So you may want to ask yourself the question: does my identity and access management system have any capacity to detect in-flight security breaches out of the box? Does it offer any cyber defense capabilities at all? If you feel compelled to purchase more security solutions to fill exposed gaps or employ more cyber professionals and developers to wire it all together, it’s time to evaluate modern CIAM solutions that deliver it all.
The new defense in depth
The merging of cybersecurity and identity heralds the dawn of a new epoch in customer identity and access management. The capacity to have security breach detection, coupled with active interdiction, all in a holistic and singular CIAM context, takes the fight to fraudsters.
At Transmit Security, we’ve focused on cyber defense from day one, and security is the foundation, deeply ingrained within our CIAM platform. As the inventors of modern identity orchestration, we’ve embedded a powerful risk and trust engine into the very fabric of identity, delivering on the promise of CAT-powered CIAM. We take the concepts of cybersecurity and CIAM, and make that pairing a reality.
When you then couple risk-aware security with best-practice orchestration and micro user journeys, you have formidable CIAM capabilities that cover the entire identity lifecycle — from onboarding and authentication to account recovery and ongoing account protection. Contextual security countermeasures are automatic, out-of-the-box and ready to deploy. But it doesn’t end there. Our cloud-native services are continually strengthened and fine-tuned by a team of leading cybersecurity experts.
This brings us back to the earlier discussion regarding the industry shortfall of cybersecurity professionals. Automated account protection speeds response time and reduces the need for manual handling. With an end-to-end CIAM platform, you can stop fraud before it occurs, minimize brand damage, prevent financial loss for both customers and your business — all while reducing the need to hire additional cybersecurity professionals.
Learn more on this topic by watching my on-demand webinar, “How Modern CIAM Defeats Complex ATOs.”



