In both real life and in online business, first impressions count.
With steep competition for new users, providing a frictionless experience during the first moments of user interaction plays a key role in enabling rapid growth. Customer surveys from leading analysts have revealed that over 70% of consumers buy on customer experiences alone, and for over two-thirds of consumers, customer experience is more important to brand loyalty than price and brand combined.
But as new account fraud and registration bots become increasingly prevalent, verifying and validating the identity information provided by new users is crucial for enterprises to prevent promo abuse, spam, scams, platform abuse and other threats. And while traditional approaches to identity security suggest that protecting against these vulnerabilities requires a tradeoff in customer experience, it doesn’t have to be this way. Rather than introducing friction in the first, most valuable moments of customer interaction, businesses can leverage the data collected from end users during these moments in order to determine user identities without requiring any additional action from those users — a process known as passive validation.
This blog will compare two key services for determining customer identity, how to contextualize them through the lens of active versus passive validation, and the use cases for passive validation to help businesses determine when and how to use it for their business needs.
Understanding and comparing identity proofing vs. identity affirmation
Two key capabilities are crucial for evaluating account fraud and other risks from new users: verifying a user’s identity and validating the authenticity of the data they provide. The services that provide these capabilities are described by Gartner, respectively, as identity proofing and identity affirmation, as we explain below.
- Identity proofing ensures that the user is the true owner of the identity and present when making requests, and is document-centric, often consisting of a scan or photo of an ID and a selfie from the user to match their identity and provide a liveness check. On the Transmit Security platform, this service is known as Identity Verification.
- Identity affirmation is more data-centric, and simply verifies whether the user’s real-world identity exists or provides risk and trust signals to help support an identity claim and determine if data points are strongly correlated with the identity a customer has provided. It may consist of a range of signals, as shown in the graph below, which are provided on the Transmit Security platform by our data validation capabilities and Detection and Response services.
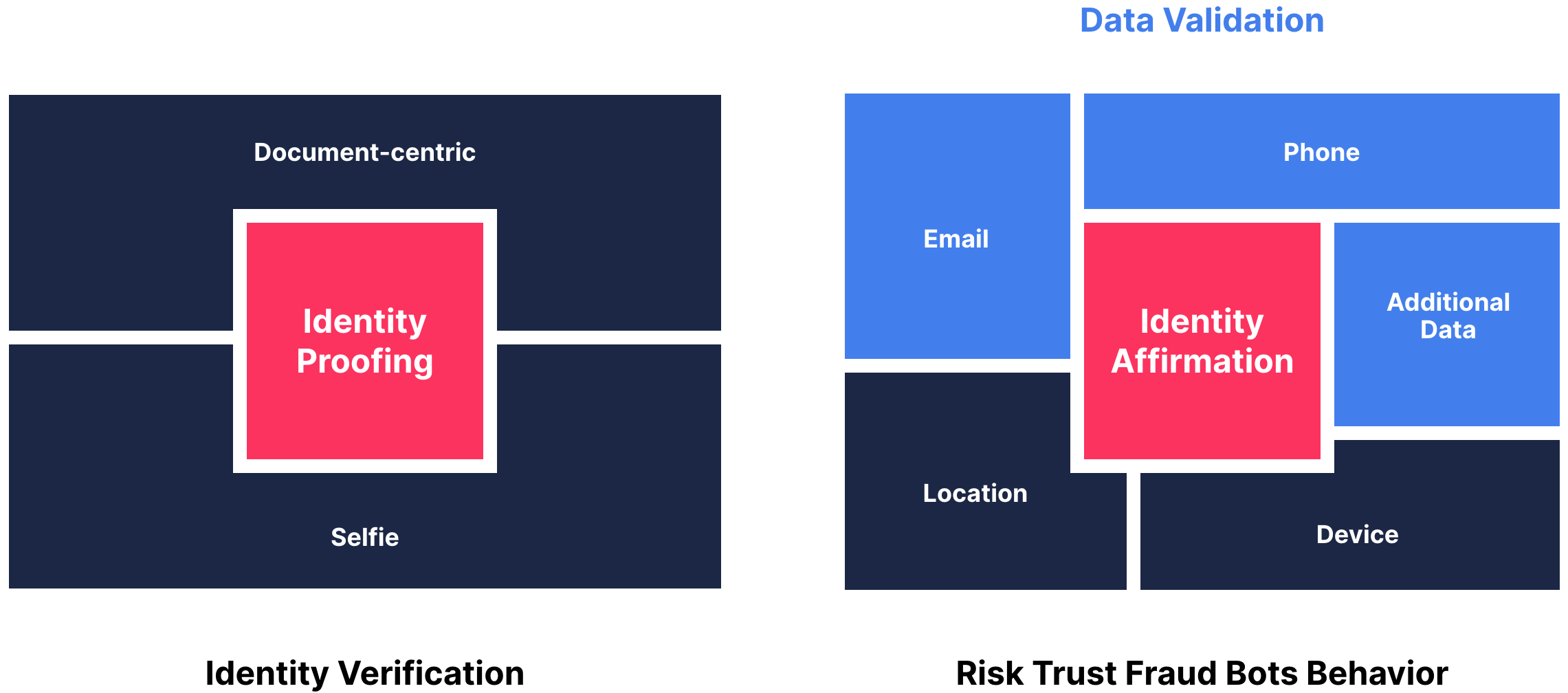
Crucially, although both services evaluate risk and trust signals for the information users provide about their identity, the two services have different levels of friction for the customer as identity proofing requires customers to have identity documents nearby and take action so that companies can ensure the user is both present and matches the identity on that document. As such, certain regulatory requirements in industries like finance may require identity proofing instead of — or in addition to — identity affirmation.
In addition, we can go a step further and extend the definitions of these services with additional examples of supporting data types to provide a stronger, more robust risk evaluation for account opening attempts — as is done with Transmit Security’s Identity Verification, Data Validation and Detection and Response services.
- Identity proofing can be extended with additional verifications of data such as emails or phone numbers.
- Identity affirmation can be extended by collecting data on interactions throughout the user journey that provide a broader context for determining the overall risk posed during the user flow.
Passive vs. active user validation
There are two approaches to validating user information: active and passive.
- Active validation requires not only validating the information provided or collected from users by a service, but active participation from users, such as providing an ID or completing additional steps like entering OTPs — resulting in added friction that comes at the price of user experience.
- Passive validation lets users focus on the task at hand without being asked to provide any further information or take any additional actions in order to create an account. So whether validations are performed on a phone number, physical address or other data, the user only needs to type the information in.
On Transmit Security’s platform, validation of customer data can be done both actively, using our Identity Verification service for identity proofing, or passively, via data validation or our Detection and Response services. This can be used to either strengthen the efficacy of identity proofing or enable a wider range of businesses to meet their security and compliance needs without the need for customers to take any additional action.
These services evaluate a range of data, as shown below.
Data validation connects to a range of services to automate background checks behind the scenes, resulting in a fast, simple and frictionless validation of:
- Email address reputation, age, domain
- Phone number reputation, age, provider
- Physical address
- Social security number
- Date of birth
- Association between user’s name and email address or phone number
Detection and Response collects and correlates a broad range of telemetry, which is analyzed to provide added assurance for user identities through a range of detection methods, including:
- Device reputation
- Network reputation
- Behavioral biometrics scoring
Sometimes, passive validation is all that you need. For example, active validation is rarely needed to establish verified emails and phone numbers, which are primarily used for account recovery purposes. OTPs and other added friction introduced in this process can be eliminated by passively collecting telemetry on devices, networks and behavioral biometrics in order to make sure missing information has no impact on future user experiences.
Use cases for passive validation on the Transmit Security platform
Identity service providers must provide a 360-degree view of end users to support the wide range of use cases covered by the collection of popular risk signals and intelligence that are out there.
Although identity proofing can — and should — be performed in the most frictionless way possible, passive validation of identity information can also provide a high level of assurance in customer identity while reducing or even eliminating this friction altogether. This enables businesses to meet a broad range of use cases including:
- Regulatory compliance: Meeting relevant geographic compliance needs, adapting to shifting global regulatory requirements and managing customer’s end-to-end journeys to satisfy location and industry-specific guidelines.
- Fraud reduction: Blocking malicious bots and bad actors from signing up for new accounts to prevent direct and indirect losses associated with fraud.
- Increased profitability: Reducing the time and complexity required for account opening or onboarding new customers while eliminating fraud and gaining more valid customers with greater lifetime value.
- Smooth onboarding: Improving user flow on websites and reducing the time and complexity required to ensure a secure account opening and onboarding process.
Diverse business needs require a range of services that can evaluate risk and trust in new account opening and beyond. Ultimately, experienced business owners must decide if these additional steps are needed in order to securely onboard new users. To evaluate the right level of assurance for your business, read more about our data validation capabilities, Detection and Response Services and Identity Verification Services, or schedule a demo with one of our experts.



