PayPal is among the most secure and trusted payment services. So how did fraudsters take over 34,942 customer accounts? The attack last month did not breach PayPal itself but instead took over individual accounts belonging to customers who had reused their passwords. It was a classic credential stuffing attack, which takes advantage of our lazy password habits.
According to Google, 65% of us reuse the same passwords across multiple accounts. And attackers know it. If they obtain the credentials for one account, they have excellent odds of finding another account that’s “protected” with the same username and password. To automate attacks, fraudsters use bots that run through lists of credentials and “stuff” them into logins on countless sites across the web.
It’s an elementary attack with a high degree of success. Even a company with strong security, like PayPal, can be exposed to account takeover (ATO) fraud. PayPal is certainly not the first or last. Norton Lifelock, an identity theft protection service, was also targeted by a credential stuffing attack in December. We take no pleasure in the irony, but I’m willing to bet the fraudsters do.
In this blog post, I’ll explain how credential stuffing works and why it’s becoming easier for cybercriminals. Most importantly, you’ll learn what you and your customers can do to mitigate this kind of attack and avoid the reputation damage that comes with it. But first, let’s take a closer look at the PayPal account takeovers.
PayPal damage control
PayPal first reported the security incident on January 18th and sent notification letters to their customers whose accounts had been taken over. PayPal says the credential stuffing attack occurred over three days in early December and exposed private customer data including names, addresses and Social Security numbers.
In the notification letter, PayPal states, “We have no information suggesting that any personal information was misused as a result of this incident, nor have there been unauthorized transactions on the affected accounts.”
The letter goes on to say, “PayPal took immediate steps to address and contain the incident upon its discovery, including masking the personal information so it is no longer visible; engaging outside counsel to assist in investigating this matter; resetting passwords for the affected PayPal accounts; and implementing enhanced security controls to prevent any further unauthorized access.”
In addition to enhanced security controls, Paypal is offering two years of free identity monitoring service from Equifax to affected users. Taking steps to retain customers — and their trust — is essential for any business.
What can consumers do to protect their accounts?
- Strengthen passwords – In the wake of this attack, PayPal is recommending unique and long-string passwords. A strong password is typically defined as having 11 to 15 alphanumeric characters and symbols, forming no patterns or words.
- Enable MFA – The company is also advising all customers to activate MFA protection in account settings. This simple step can prevent a fraudster from accessing an account, even if they have a valid username and password.
It’s worth noting that the number of accounts impacted by the credential stuffing attack is relatively small when you consider that 429 million people use PayPal. We can safely assume multi-factor authentication (MFA) and perhaps other security layers played a significant role in limiting the damage.
Most PayPal accounts, including my own, are protected by MFA. Every time I try to log in, PayPal sends me a 6-digit one-time passcode (OTP) via text so I can access my account. In this type of large-scale attack, fraudsters are unlikely to spend time trying to bypass the MFA mechanism, but instead target accounts that are not protected by MFA. - Use a password manager – There will always be cases when complex passwords plus a second authentication factor will not be enough. Until we phase out passwords completely, all consumers should also use a password manager. After all, credential stuffing is, in part, a consequence of massive breaches that swipe credentials stored in plain text. Even password hashing algorithms can be reversed.
While password managers aren’t hacker-proof, protecting and storing complex, unique passwords with a strong master password plus MFA is the industry standard for security, far exceeding a typical user’s ability to secure accounts and passwords on their own.
Much more can be done by service providers to prevent ATO fraud, and we’ll get to that in a subsequent section. But first, let’s get a refresher on the basics…
How does credential stuffing work?
Credential stuffing attacks exploit common human weaknesses, which include a fallible memory and a tendency to take the easy route. Why memorize unique complex passwords for every single account when it would be so much easier to remember the same and simple password for all accounts? The reason is plain to see: it’s not secure. Attackers profit off those who reuse passwords.
Before launching a credential stuffing attack, the fraudster must first obtain a treasure trove of usernames and passwords via a data breach or phishing attack. Alternatively, they can purchase dumps of credentials listed for sale on the dark web. It’s that easy.
Once an attacker has credentials, they simply try to log into other online accounts. For example, a password from a social media account may be used to access other social media, email or bank accounts. You name it, the attacker has endless possibilities.
Automations make it easy to strike fast, at scale
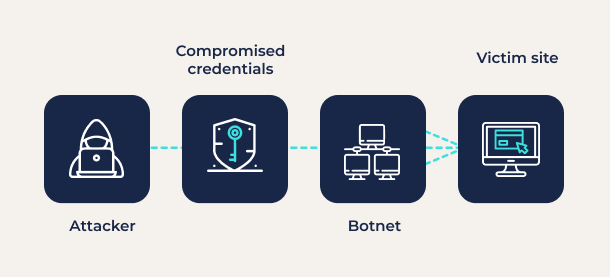
- Botnets – Credential stuffing attacks are typically automated using armies of bots. With a long list of compromised credentials, bots can cycle through thousands of credential combinations to target specific websites. If one login doesn’t work, they move on to the next until … Bingo! They simply log in and take over any and all accounts that were set up with reused passwords.
- Automation frameworks – As fraudsters continue to expand their tools and techniques, credential stuffing will only become harder to detect.
For example, the open source web-testing tool OpenBullet, designed for developers to simulate logins from different users with various configurations, makes it easy for attackers to test thousands of username and password combinations using IP proxies plus manipulated cookies and headers.
These cloaking techniques can make requests appear as if they are coming from a variety of distributed IPs and devices, allowing attackers to circumvent rate-limiting controls that would prevent the large number of requests needed for a successful credential stuffing attack.
6 ways companies can prevent ATOs
In the face of complex, evasive tactics, companies must implement layered protection that can gracefully transition customers away from passwords while detecting ATO fraud, including deceptive credential stuffing attacks, in real time.
- Passwordless MFA – As a first layer of defense, service providers need strong passwordless authentication that includes fingerprint or facial biometrics. Customers who choose to authenticate with biometrics attain complete immunity to credential stuffing attacks.
Transmit Security’s Passwordless & MFA service enables you to implement all forms of authentication with a single service — so you can phase out passwords or eliminate them completely. Customers who choose to authenticate with fingerprint or face ID achieve the strongest form of MFA that’s also easiest to use. - Other forms of MFA – For customers who aren’t ready or able to use biometrics, you should enable them to use email magic links, SMS OTP and/or social logins — MFA methods anyone can use.
- Device fingerprinting – You can strengthen these weaker forms of MFA with strong device fingerprints based on multiple device characteristics. This can be used as an anchor of trust, which links users’ trusted devices to their individual profiles.
- Passkeys – Our Passwordless & MFA service supports and further strengthens passkeys, so it’s worth calling it out specifically. As an early adopter of passkeys, PayPal is clearly embracing this approach. In fact, PayPal may have limited the scope of the credential stuffing attack, to some degree, by preventing attackers from targeting customers who are now using passkeys, not passwords.
- Continuous assessments of risk, trust, fraud, bots and behavior (RTFBB) – As the next layer of account protection, you need a solution that can assess all that’s happening, all signals, in real time — throughout the identity journey.
Protecting accounts without hurting the customer experience requires accurate, dynamic fraud detection. It must be smart enough to distinguish between good and bad activity — even when fraudsters use evasive tactics or when trusted customers switch to a new device or change their behavior.
To detect fraud with accuracy, you need a context-aware solution that examines a broad range of telemetry and combines multiple detection methods, such as advanced device fingerprinting, bot detection and behavioral analysis. Transmit Security’s Risk, Trust, Fraud, Bots & Behavior Detection service delivers actionable recommendations that can be used to trigger the right action, at the right time. You can also automate protection against new threats when they first emerge. - Added passkey security – By implementing Passwordless & MFA + RTFBB Detection services together, you gain an added layer of protection to secure passkeys. Prior to enrolling new customers and devices, you can assess the user’s identity or device to establish preliminary trust. After enrollment, the passkey user and their accounts will then be continuously protected — across the full identity journey.
See how our Risk, Trust, Fraud, Bots & Behavior Detection Service can help your business prevent and mitigate credential stuffing and other ATO attacks. We can all rally behind PayPal and do what it takes to beat fraudsters at their own devious game.



