Smash Security Threats Like Pro!
Transmit Security is serving up unbeatable protection – and custom pickleball paddles at RSA 2025. Book a meeting to grab yours and take your security game to the next level!
Transmit Security is serving up unbeatable protection – and custom pickleball paddles at RSA 2025. Book a meeting to grab yours and take your security game to the next level!
For the first time, a unified enterprise-grade platform that includes best-of-breed identity management, fraud prevention and identity verification. Stop toggling between and normalize data from various sources. Focus on visible, tangible value for your organization.
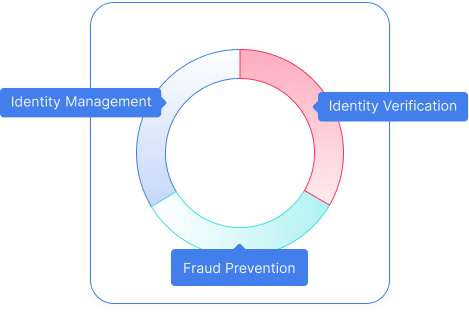
One platform for best-of-breed identity management, fraud prevention, identity verification
One platform to serve identities across the entire user lifecycle
One platform across all your user facing channels
Mosaic by Transmit Security is the only identity platform built from the ground up for orchestration and AI. Use drag-and-drop tools and natural language prompts to design any customer journey—like registration, login, or payments—while AI handles security, integrations, deployment, testing, and more.
Mosaic by Transmit Security is a microservices-based CIAM platform designed for both B2C and B2B use cases. Easily manage customer onboarding, lifecycle journeys, progressive profiling, consent, self-service experiences, and more—from one unified solution.
Mosaic by Transmit Security supports a full range of Multifactor Authentication (MFA) options—including OTP, passkeys, mobile biometrics, magic links, and social login. Design the ideal MFA experience for your applications and users—tailored to your UX goals, security needs, and compliance requirements.
Stop chasing rules. Stop chasing false positives. Mosaic by Transmit Security is the only fraud prevention engine built on modern AI technologies—delivering massive scale and unmatched accuracy. With built-in workflows, automation, and AI-driven investigations, your fraud operations become radically simpler, faster, and smarter.
Stop synthetic and stolen identities at the source. Mosaic by Transmit Security is the only identity verification solution built to detect advanced account opening and onboarding fraud. Scan and validate government-issued IDs, confirm true document ownership, and streamline secure onboarding—all in one seamless flow.
Powered by GenAI experiences for advanced data analytics, user journey creation, fraud investigation, and platform administration.
Business workflows automation for streamlining identity and fraud operations across your entire ecosystem and organization, powered by a rich integration hub.
A variety of deployment options to best fit your identity infrastructure and architecture as well as your security considerations and policies.
The only platform to offer active-active multi-cloud global presence that runs simultaneously in GCP and AWS. Operate in our cloud or at your cloud provider. Gold standard at the largest orgs, some serving over 100 million+ customers each.
Operating in silos is severely impacting your velocity, preventing you from delivering an excellent customer experience and effectively combating fraud. Identity Fusion provides a unified development and operational environment for all stakeholders.
Participate in designing new customer journeys, Configure automated business workflows to improve your day to day. Use Al-analytics to quickly explore why a user was blocked or failed. Explore trends and present to the business with the help of Al.
Participate in designing new customer journeys, Configure automated business workflows to improve your day to day. Use Al-analytics to quickly explore why a user was blocked or failed. Explore trends and present to the business with the help of Al.
Participate in designing new customer journeys, Configure automated business workflows to improve your day to day. Use Al-analytics to quickly explore why a user was blocked or failed. Explore trends and present to the business with the help of Al.
Participate in designing new customer journeys, Configure automated business workflows to improve your day to day. Use Al-analytics to quickly explore why a user was blocked or failed. Explore trends and present to the business with the help of Al.
Participate in designing new customer journeys, Configure automated business workflows to improve your day to day. Use Al-analytics to quickly explore why a user was blocked or failed. Explore trends and present to the business with the help of Al.
Participate in designing new customer journeys, Configure automated business workflows to improve your day to day. Use Al-analytics to quickly explore why a user was blocked or failed. Explore trends and present to the business with the help of Al.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.