Biometric Authentication
The growth of facial and fingerprint recognition to authenticate to smartphones and other devices has brought biometric authentication into the mainstream. This form of authentication provides a secure and more user-friendly alternative to traditional, password-based authentication systems.
What is Authentication?
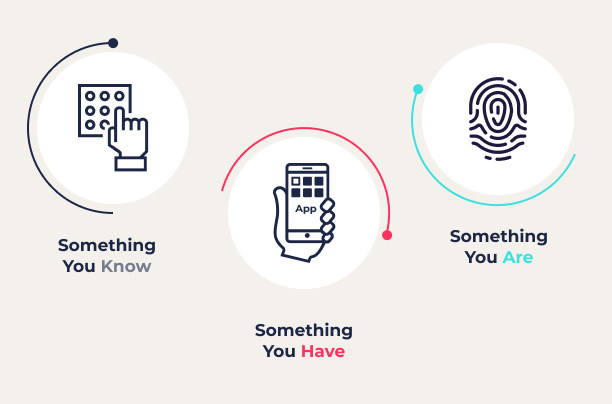
Authentication is the process of demonstrating the identity of a user or device to another system. Authentication methods fall into three main categories or types of “factors”, including “something you know”, “something you have”, and “something you are”.
All of these types of authentication factors are in common use today. Some of the popular authentication methods used today include:
- Passwords
- One-time codes
- Magic link authentication
- API keys
- Authentication tokens
- Smartcards
- Fingerprint scanner
- Facial recognition
What is Biometric Authentication?
Biometric authentication is designed to use a “something you are” factor for authentication. A sensor on a device collects data on a unique physical attribute. Some common examples of biometric authentication include fingerprint scanners, facial recognition, and retina scanners.
Biometric authentication has been around for millennia since people recognized that fingerprints are unique. In the second century B.C., Chinese emperor TS’In She authenticated seals using a fingerprint.
Since then, people have discovered other unique physical features that can be used for biometric authentication. In the 19th century, a French police officer named Bertillon started using body measurements to identify repeat offenders. This started with photographs and anthropometry and expanded to include fingerprints and other patterns.
Biometric Verification vs. Authentication
Biometric verification is the process of proving a person’s identity. For example, when applying for a government ID card, a person will likely need to verify that they are who they claim to be. Biometric data is a good choice for this because it is difficult to fake and provides a high level of assurance of a person’s identity.
Verification and authentication are similar but different concepts. Verification occurs only once with the goal of linking a person’s identity to some unique information about them (such as biometric data). Authentication occurs multiple times and uses this verified data to prove a user’s identity. Essentially, verification lays the groundwork for later authentication attempts.
Types of Biometrics
Fingerprints and photos are the most well-known form of biometric authentication, but they are not the only options. Some of the other common types of biometrics include:
Fingerprint Authentication
Fingerprint authentication is one of the most well-known and widely used forms of biometric authentication. Fingerprint scanners can collect up to 30 minutiae (specific points) in a fingerprint, and over 100 years of FBI data indicates that two individuals never share more than 8 minutiae. Fingerprint scanners have become a common alternative to PINs, passwords, and patterns for smartphone authentication and can be used for other authentication tasks as well.
Facial Recognition
Facial recognition converts a collection of unique measurements into a faceprint or template used for authentication. Facial recognition systems commonly use 80-90 of these nodal points such as measurements of the node, jawline, cheekbones, and eye sockets Modern facial recognition scanners perform analysis in 3D to protect against being fooled by a photograph.
Voice Recognition
A person’s voice is also unique and a good candidate for authentication. Features such as the tone, pitch, frequencies, and other characteristics of voice are commonly used for authentication in call centers but can also be collected and used for other applications.
Retina and Iris Scanning
Retina and iris recognition systems develop a unique signature for a person based upon the detailed patterns within the eye. However, this approach requires infrared lighting and cameras and low-light levels to function, making it an uncommon solution for biometric authentication.
DNA Matching
Everyone’s DNS is unique, making it an ideal candidate for biometric authentication. While this form of identification is used by law enforcement, paternity tests, etc., it is not in widespread use today due to the need to collect and analyze blood or tissue samples to extract DNA.
Other types of biometrics
Emerging biometric technologies include palm vein recognition and gait recognition, among others. Palm vein scanners can map an individual’s unique vein patterns in the palm by using infrared light. Gait recognition analyzes details in the way someone walks to identify them. These types of biometrics might be considered for verifying employee access to high-security facilities. Neither one would be a viable nor necessary option for customer authentication.
Is Biometrics Secure?
If implemented correctly, biometric authentication is the most secure form of authentication available. While some biometric scanners have been fooled by photographs or using gummy bears, these scanners are growing increasingly sophisticated and harder to fool.
Unlike other means of authentication, biometric authentication does not use factors that can be copied, lost, or forgotten. This makes it a highly usable and secure authentication option.
What is Multimodal Biometric Authentication?
For increased security, a system or application can use multimodal biometric authentication. This combines multiple forms of authentication such as requiring both facial and fingerprint scanning. By adding additional modes of authentication, multimodal authentication makes it more difficult for an attacker to fool the system.
What is FIDO2?
Fast Identity Online 2 (FIDO2) is a standard that uses public-key cryptography for fast and secure user authentication. Biometric authentication systems that are FIDO2 certified have been proven to provide strong authentication while protecting user privacy. Learn more about FIDO2 passwordless authentication.
Pros and Cons of Biometric Authentication
Biometric authentication has significant promise, which is why it is the go-to choice for science fiction and spy movies. However, in addition to significant benefits, modern biometric authentication systems also have their disadvantages.
Pros of Biometric Authentication
Some of the main advantages of biometric authentication include:
- Improved Security: Biometric authentication provides much better security than other forms, such as passwords. Biometric authentication doesn’t have the problems of weak and reused passwords, and they are much harder to obtain or copy than a password or a physical token.
- Better User Experience: Most other forms of authentication require a user to memorize and enter something into a computer or keep a physical device with them. Biometric factors are part of your body and authentication only requires touching a scanner or looking into a camera.
Cons of Biometric Authentication
Biometrics is the best form of user authentication, but they aren’t perfect. Some of the challenges associated with them include:
- Biased Training Data: White males are disproportionately represented in the training data sets used to develop biometric authentication systems. As a result, these systems can have difficulty recognizing women and people of color.
- Data Storage: The data used in biometric authentication systems is personally identifiable information (PII) and cannot be changed if breached. As a result, this data must be carefully and securely stored.
- Failed Authentication: To avoid false positives, biometric authentication systems may only allow small variations for recognition. As a result, a system may not recognize a legitimate user if, for example, they have cold or dirty hands and try to authenticate via a fingerprint.
Biometric Authentication Use Cases
Biometrics is the strongest and most secure form of user authentication with applications in many different sectors.
Travel and Hospitality
Biometric authentication is increasingly being used in the travel and hospitality industries to authenticate the identities of travelers. For example, airports are increasingly implementing facial recognition to identify passengers as part of the check-in process for flights. Also, electronic passports commonly use a mix of biometric factors for authentication such as two fingerprints and a photograph.
Banking and Financial Services
One of the major advantages of biometric authentication is that it provides stronger security than other forms of user authentication. This is ideal for high-risk services such as those in the banking and financial services sector. For example, an online banking site might require multi-factor authentication (MFA) with biometric factors to authorize financial transactions.
Healthcare
Countries with national healthcare programs, such as some European and Middle Eastern countries, use biometric ID cards for healthcare services. These ID cards enable healthcare providers to verify the identity of patients and ensure that they are eligible for national healthcare services.
Retail
Biometric authentication can be used to simplify and streamline the authentication process for online and in-person commercial transactions. With fingerprint or facial recognition, a user can rapidly and securely prove their identity to pay for goods and services.
Government
The use of biometric ID cards is also commonly applied to user authentication for government services. For example, governments may use these ID cards to strongly authenticate the identity of voters and for law enforcement.
Common Uses of Biometric Authentication
Mobile fingerprint authentication is the most widely used form of biometric authentication. The primary reason for this is that Android and iOS have introduced it as a means to quickly and securely authenticate to their smartphones.
However, mobile fingerprint authentication is not the only way that biometric authentication is in common use today. Some physical tokens, such as the Yubikey Bio will use a fingerprint scan to authenticate a user for multi-actor authentication.
Fingerprints, facial recognition, and other forms of biometric authentication may be more common in corporate settings than for user authentication. For example, fingerprint scanning may be used to authenticate an employee before permitting access to a secure area.
Biometrics and Data Protection
Biometrics data is one of the most widely protected types of data in the US and EU. By definition, the features used in biometric authentication are personally identifiable information (PII). This type of data is strongly protected under laws such as the EU’s General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and other state-level data privacy laws. These regulations restrict the collection and use of certain types of data, include consent requirements, and mandate certain security controls to protect customers’ data.
Improving Authentication Security with Biometrics
Biometric authentication is the most user-friendly and secure form of user authentication. Replacing insecure and high-friction password-based authentication improves the user experience and the security of the authentication process.



