What is an identity provider? An identity provider (IdP) is a system that creates, manages and stores digital identities. The capabilities and features of different IdPs can vary, but they’re typically made of three main components: a repository of user identities, an authentication system and security protocols that defend against intrusion. An IdP verifies user identities using one or more authentication factors, such as a password or fingerprint scan.
At the core of every company’s IT infrastructure, you’ll find a system for provisioning, verifying and managing user identities. However, as enterprises grow, the job of maintaining this system becomes more and more complicated — and costly. Ultimately, the difficult task of remembering authorized users can overwhelm organizations that haven’t prepared for expansion. Identity providers are essentially a very smart and adaptable guest list designed to tackle this problem.
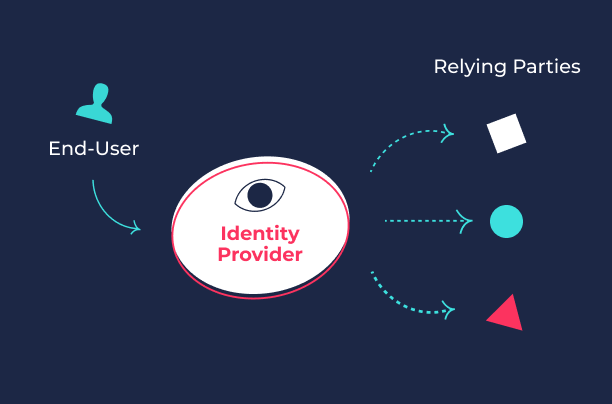
Are IdPs always third-party or IDaaS solutions?
It’s easy to get confused with so many IdPs putting out their own descriptions of what an identity provider actually does. Some say it’s always a third-party solution, and others make the case that it’s always Identity as a Service (IDaaS). While it can be both of those things, neither are requirements to fill the role of IdP. The confusion primarily stems from context and the fact that real-world applications often interweave third-party IdPs, IDaaS and other cloud-based IAM (identity access management) services.
The function an IdP provides can be achieved with an in-house solution. It’s simply rare in the age of cloud computing. For example, if you logged into Google Suite, Google would be the IdP. Because both the application and the authentication are handled by the same organization, it would be more accurate to just call this CIAM (customer identity access management) than to describe Google as the IdP.
Of course, this is an edge case. Most companies have neither the resources nor the technical expertise to achieve Google’s standalone authentication. Today, it’s relatively rare for an organization to meet all of their own identity and authentication needs. The complexity of the technology behind it and the sensitivity of the data being handled are simply too risky for anyone but specialists to implement.
What is an identity broker?
An identity broker connects identity providers with services that want to offer them to their users. Identity brokers bridge the gap between differing authentication protocols and architecture, and they allow services to integrate with the IdPs of their choosing. Not all IdPs require an identity broker to get up and running, but many brokers simplify the IdP integration process and ensure there are as few hiccups as possible.
IdPs as third-party authenticators
Some IdPs can be used across different platforms if they’re already an established and trusted entity. These kinds of IdPs can be used to quickly authenticate users on different apps, websites and digital services by providing the necessary information and establishing trust without re-registering. This action works a lot like SSO, only between different identity management systems.
An example of using a social network-based IdP would be logging in with your Google account on a service that is not operated by Google. You’ve probably seen a button stating “Log in using your Google account” when registering for an online service. That’s Google (the IdP) being used as a third-party authenticator. This practice has become increasingly common because it’s a highly effective way of offloading security and identity management burdens.
Identity Providers and SSO
In some circles, IdPs and SSO have become synonymous because remote SSO is explicitly impossible without a cloud-based identity provider. This type of SSO must draw on a repository of user identities, and cloud-based IdPs make that possible. Sometimes an IdP and an SSO provider might be the same organization, but this opens the door to attacks targeting the communication between the SSO and the requesting application. SSOs and IdPs are typically kept separate for this reason, and it’s rare for an organization to implement SSO using only offline or non-cloud identity provision.
Should I use an identity provider?
An identity provider can resolve many challenges that modern enterprises face when authenticating users. Here are just a few of the advantages:
- Improves the customer experience
The customer experience benefits from using IdPs enormously because of the decreased friction when creating a new account. Instead of creating a new username and password, an IdP leverages the information they already collected to authenticate the user. This allows a customer to get back to enjoying a service’s offerings faster and dramatically reduces the likelihood that they encounter account-related issues later on.
- Eliminates the problem of passwords
When you consider the downright dangerous password hygiene of most Internet-goers — 51% reuse the same password over and over —, it makes sense to try to eliminate passwords as much as possible. Of course, with many IdPs, there’s a password involved in the process somewhere along the line. But that doesn’t change the fact that the fewer passwords a user has to create and remember, the less likely they are to be affected by a credential stuffing attack.
- Increases authentication security
IdPs make it easier to ensure users are who they say they are without the upfront investment of building and managing identities. Not only do some IdPs provide more stringent security measures to verify users with confidence, they also make it possible to verify the same users across multiple networks, making the likelihood of fraud significantly lower. Combinations of identity providers effectively create third-party-sourced multi-factor authentication with considerably less effort on the service provider’s part.
Any IT department for a large organization would agree that these are tangible benefits that offload extra work and resources that are better spent keeping customers happy and engaged. IdPs are an excellent way to add a strong authentication option and improve the customer experience. That said, it’s not a complete solution — using an IdP is just one part of creating a fantastic and secure experience for your customers.



