Two-factor authentication has invaded nearly every corner of our digital lives — a gradual but relentless escalation over the years. Most consumers are now very familiar with what 2FA means, how to use it, and why it is important. You can be certain any new digital service today comes with two-factor authentication as a standard.
But the need for better authentication over the past two decades has given rise to various implementations. The evolution, in some cases, started with retro-fitting web applications that previously supported passwords only. Fast forward to today: mobile-first applications are now built on sophisticated hardware with secure elements and embedded biometric sensors.
Along with new technology and authentication capabilities, we’ve been hearing more marketing claims around the terms: multi-factor authentication (MFA), strong customer authentication (SCA) and step-up authentication.
What do MFA, SCA and Step Ups mean? Are they really any better than 2FA? Let’s examine where these terms came from and the nuances between them. Later in this blog article, I will also discuss state-of-the-art authentication methods to consider for your next project. But first, let’s take a quick look at the history of authentication.
The invention of online fraud
After the World Wide Web went live with the first web page published at CERN in 1991, it turned very quickly from a document sharing system to the foundation for a full-fledged digital application channel. Businesses everywhere started publishing web apps, from simple retail sites to major high-street banks. It was, as we all now know, a global business revolution.
And yet the only security option available at the time was the humble password! Just one single, solitary factor. A knowledge factor. So easily guessed, keylogged, stolen and “stuffed.” Criminals immediately saw opportunity and began hacking. The most basic security requirements needed to protect consumers shifted markedly overnight, and the pressure was on security developers to combat the massive rise in online fraud.
So if the “something you know” password was no longer good enough, what other authentication factors can we use to build a stronger proof of identity?
What are the three factors of authentication?
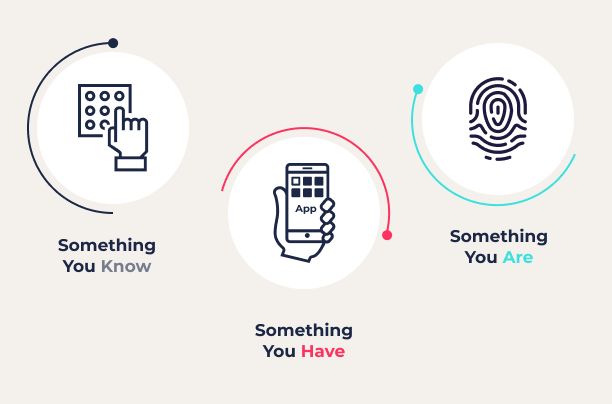
- Knowledge Factor
Something you know: passwords and PINs - Possession Factor
Something you have: physical proof, like a security key or device - Inherence Factor
Something you are: physical attributes like biometric markers
The solution became clear. If you could combine more than one factor at a time, the classic methods of password hacking could be defeated. This was the beginning of 2FA and step ups.
What is 2FA and step-up authentication?

2FA is the addition of a second factor on top of your existing factor, typically a password. If all apps started with a password, then it was simply a matter of adding either a possession or inherence factor to the mix.
If you were seeking to solve this problem 20 years ago, which additional factor would you choose? Well, if we cast our minds back to the turn of the century, you actually didn’t have much of an option. The ability to use biometrics was limited to police fingerprinting with an ink pad and paper. Digital biometric technology like Windows Hello and Apple Touch ID didn’t exist yet. Smartphones weren’t even invented. Biometrics was simply not an option.
At the time, the solution was to focus on the possession factor. For the general public, the invention of one time passcodes (OTPs), delivered primarily through hardware tokens, was our first foray into this secure new world. Small, clock-based devices that could produce mathematically predictable codes enabled a simple proof: if you know the code, you must have the device.
Additional OTP methods such as email and SMS-based OTPs, as well as soft token OTP generators also came to the fore. Hackers have found ways to intercept these codes, but the principles of OTP possession have remained the same. OTPs are still one of the primary 2FA methods in use to this day.
If your password is your first factor, then your OTP is your second factor. You have now achieved what we refer to as 2FA. And it follows that if you log in with a password to start, then the act of performing a second factor OTP is a form of step-up authentication. You “step up” to a higher level of security.
2FA and step ups are the historical foundation for multi-factor authentication. You were one factor, and now you are two. You were at a lower level of security, and now you’re at something higher.
What is multi-factor authentication (MFA)?
Multi-factor authentication (MFA) is effectively any broad mix of more than one factor. And it could be argued that it does not technically vary from the definition of 2FA, which is a numerical subset of MFA.
But here’s the nuance: MFA infers a more evolved and non-constrained approach, with a higher proclivity to leverage biometric capabilities on the smart devices we all own. In doing so, MFA encompasses a broader mix of authentication factors. It is entirely possible to perform authentication using a possession factor (a private key on your device) and an inherence factor (biometric), and to do this with NO knowledge factor (password) at all!
This is the game-changer. MFA does not imply that you begin with a username, password and then add some form of additional factor later. Want to learn more? Visit our dedicated page, what is MFA?
How does FIDO2 strengthen MFA?
If we look to the FIDO2 standard for instance, MFA can be achieved immediately, all with no usernames, no passwords and no OTPs. The possession factor is established through the private key that sits within your device, and the inherence factor is achieved through a biometric, which unlocks this key. There was no “low security” (password), and therefore no need to “step up” to a higher level of security. MFA was immediately attained through one, very simple user action, a fingerprint or facial scan.
What is strong customer authentication (SCA)?
Strong customer authentication (SCA) is a broad MFA requirement established by the EU’s Payment Services Directive 2 (PSD2). SCA is used when describing MFA requirements for payments and broader Open Banking and Open Data initiatives. For all intents and purposes, SCA can be used interchangeably with the more common term MFA.
Key differentiators of 2FA, MFA and SCA
2FA, step ups, MFA and SCA all reach for the same goal. At its core, the veracity of your authentication is premised on supplying more than one factor for identity verification. The key nuances to understand are this: MFA and SCA are inherently more secure than their predecessors, basic 2FA and step ups.
MFA and SCA typically leverage the secure elements of smartphones and biometrics, enabling strong authentication with lower user friction. Supported by a network of risk and trust signals, MFA tends to “just be.” Full trust is determined right from the very beginning, rather than starting from a single factor, and then stepping up into a higher one later.
SCA is a definition by PSD2 that formalizes the definition of MFA, and the requirements set for performing payments and Open Banking and Open Data transfer between entities.
How to Implement MFA and SCA
Modern implementations should seek to establish a high trust, highly authenticated security posture with minimum customer friction across the customer journey. Based on FIDO2, authentication provided by Transmit Security delivers the gold standard of MFA, biometrics, trust and security — for even the most discerning and risk averse industries.
is a straight through MFA process that immediately provides MFA and PSD2 SCA authentication assurance across all channels, with no usernames, no passwords, no OTPs.
By leveraging modern security standards, OpenID Connect and FIDO2, our cloud-native service is purpose built for ultra-rapid, easy-to-implement, limitless scale deployments that can augment or replace your existing customer authentication journeys.



