In the fight to stop fraud, security teams and analysts must use every tool in their arsenal — including device fingerprinting, a powerful risk and trust signal for detecting known malicious devices and anomalies that can indicate account takeover (ATO) and new account fraud.
However, because device fingerprints are also commonly used for target advertising, personalization, marketing and user tracking, an increasing number of end users have expressed concerns over device fingerprinting, resulting in new regulations, browser changes designed to inhibit fingerprinting and incognito browsing options for enhanced user privacy.
So how can businesses protect user privacy and adhere to regulations while still leveraging device fingerprinting to protect their users? In this blog, we’ll review what device fingerprinting is and how it works, the cybersecurity use cases for device fingerprinting, how user privacy concerns impact device fingerprinting and how device fingerprinting works on the Transmit Security Platform.
What is device fingerprinting and how does it work?
A device fingerprint or machine fingerprint is a calculated identifier used to identify a remote computing device based on collected information about its software and hardware. Robust fingerprints are based on a wide range of telemetry, including data points such as:
- Hardware, including screen properties, graphics card and RAM
- Graphics, including supported video codecs and canvas properties
- Audio properties and codecs
- Environment factors such as OS, connectivity, and storage
Fraud detection use cases for device fingerprinting
With regard to fraud detection, some of the key use cases for device fingerprints include:
- Trusted device: Device fingerprinting identifies a previously known trusted device (inherence) by matching the associated trusted device within the user’s historical profile. Trusted devices can be used to reduce friction and improve UX by extending sessions or silently authenticating users providing an additional authentication factor to reduce the need for context switching in multifactor authentication.
- Session and cookie hijacking: Fingerprint mismatch detection is a signal fed to the risk engine enabling it to detect session and cookie hijacking attacks and adapt the risk level accordingly. By verifying whether a device fingerprint matches the fingerprint associated with a user’s session, security and fraud teams can verify the authenticity of a device throughout the session.
- Device reputation: Global threat intelligence and in-house teams like Transmit Security’s Research Labs maintain lists of device fingerprints previously associated with confirmed fraudulent activity, enabling the detection of known malicious or compromised devices. Transmit Security’s Detection and Response Services gives Risk Administrators added control in this regard by allowing them to manage Allow, Challenge and Deny lists of device fingerprints.
- Device action rate and velocity: By measuring the activity rate from a single fingerprint for multiple time windows, high-speed or high-velocity actions and anomalies in the rate of action from a single fingerprint can be used as a valuable risk indicator. On the Transmit Security Platform, Detection and Response Services monitor user actions and associate them with device fingerprints in real time.
In these use cases, device fingerprints not only protect end users from malicious activity that could compromise their identity data and accounts, but enable a more frictionless user experience that builds — rather than detracts from — the trust they have in the businesses they interact with.
However, in order to gain and maintain this trust, businesses must ensure that fingerprinting is implemented responsibly, taking care to respect users’ privacy and the regulations designed to protect it.
Device fingerprinting and privacy concerns
Although device fingerprinting enables significant security and user experience benefits for end users, it’s crucial that businesses consider how device fingerprinting impacts both regulatory requirements and user privacy. Starting with the passage of the EU’s GDPR in 2018, governments worldwide have been tightening restrictions on how businesses collect and process user data to give end users more control over how their data is used.
The GDPR applies not only to EU businesses, but companies worldwide that process the data of EU citizens. And although the US does not have an equivalent nationwide law to protect user privacy, statewide rules such as California’s CCPA protect data processing for California’s citizens, requiring many businesses to get explicit consent from users before collecting their data or limit data collection to specific use cases, like cybersecurity and fraud detection.
Under the both the GDPR and CCPA’s broad definition of “processing personal data,” businesses may be required to take steps that could impact the use of device fingerprinting:
- Only use collected information to protect the user’s private data
- Get explicit consent from users and explain how the information will be used before collecting their information for marketing or promotional purposes
- Ensure that personal data collected adheres to the local data residency requirements stipulated by the GDPR and other relevant legislation
Device fingerprinting vs. cookies
Although the GDPR and CCPA do not explicitly mention the use of device fingerprinting in their laws, they do provide clear guidelines on the use of cookies, which are attached to user sessions in order to collect data about how users are interacting with applications and websites.
Because session cookies also collect information about users’ browsers, they have some overlap with device fingerprinting, but are distinct in several ways:
- Fingerprints are more robust than cookies, as users can delete cookies by clearing their browser history or avoid cookies through the use of incognito browsers or search engines like DuckDuckGo.
- Whereas cookies only use data on users’ browsers, fingerprints leverage additional device identifiers, such as information about the device’s hardware, OS and connectivity.
- Cookies store browser data locally on user’s machines, whereas device fingerprints are stored in server-side databases.
In addition, increased user privacy restrictions and increased demand for consumer data privacy, some browser providers and device manufacturers are beginning to restrict the use of third-party cookies, as well as the information that’s returned by JavaScript engines, the main interface through which device fingerprinting is done.
These changes present a challenge for many device fingerprinting providers to create robust fingerprints, which we’ll discuss further in our next blog in the series.
How Transmit Security uses device fingerprints
Transmit Security’s Detection and Response Services provide strong device fingerprints with a 97% true acceptance rate and a 99.7% true rejection rate. This capability is further enhanced by additional methods of detection, including behavioral biometrics, user activities, threat intelligence, bot detection and more, as shown below.
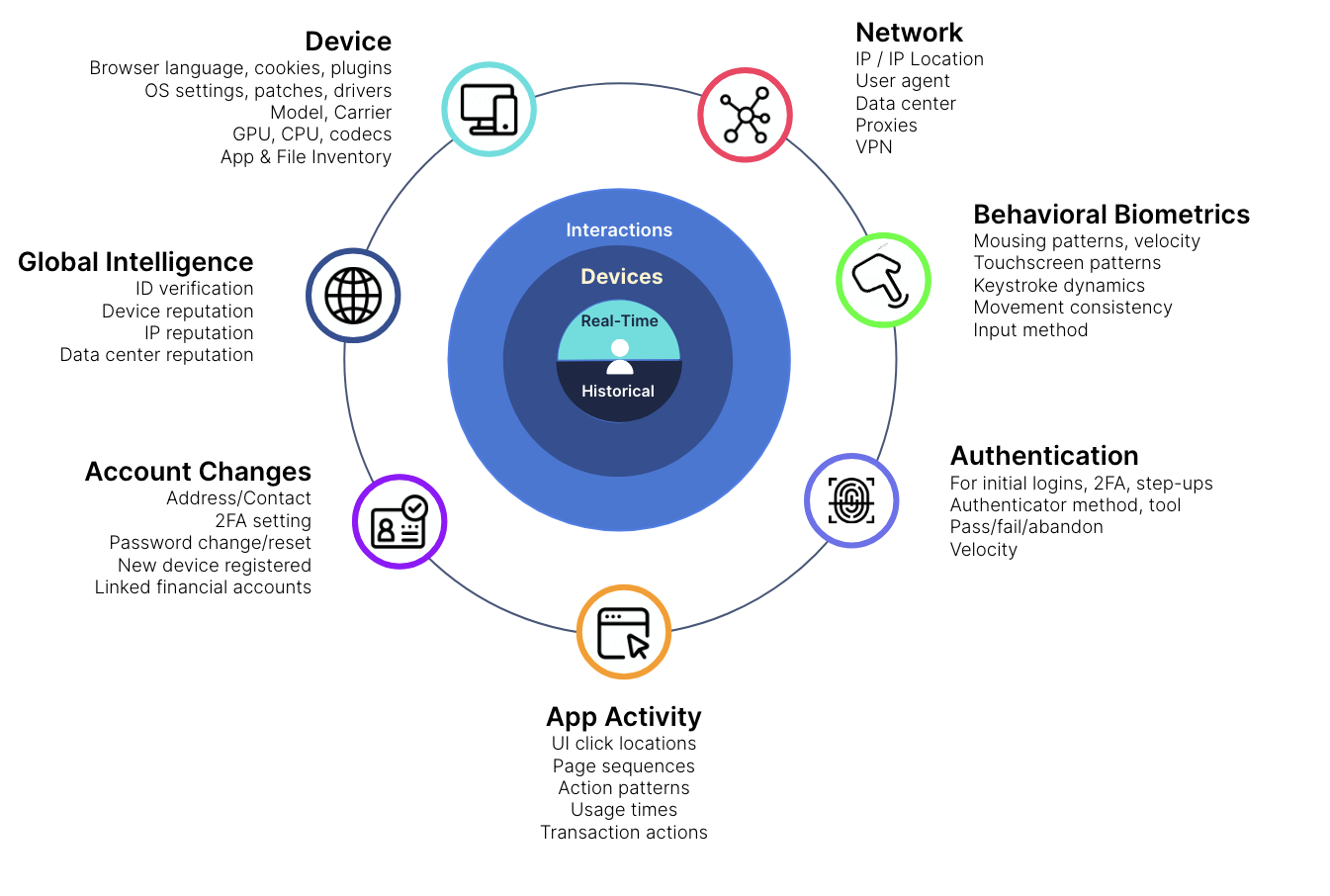
In addition, our platform is fully GDPR compliant to ensure that enterprises worldwide can adhere to local data residency restrictions, and our no-code and low-code orchestration capabilities enable businesses to quickly implement or change rules in accordance with their specific business needs, giving them more control over how users’ personal data is stored and processed.
As a result, businesses can leverage device fingerprints for fraud detection without compromising their regulatory needs or the privacy concerns of their end users. In the next blog in this series, we’ll discuss some of the challenges fraud detection providers face in developing robust fingerprints, the techniques fraudsters use to evade device fingerprints and how combining device fingerprints with other detection methods can be used to provide better protection against these emerging threats.
Stay tuned to find out more about device fingerprinting, and in the meantime, check out our solution brief on how device fingerprinting works on the Transmit Security Platform.



