It’s 2024. Do you know who is redeeming your customers’ loyalty points? Loyalty fraud is on the rise, costing over $1 billion annually for large travel and hospitality companies. One of the many challenges is that 45% of loyalty program accounts are inactive or infrequently used — and this opens the door for fraudsters takeover accounts and redeem points.
Although fraud is often considered a banking problem, the reward and loyalty membership points offered by hospitality and travel businesses provide equally lucrative opportunities for fraudsters. But unlike banking and other financial accounts, loyalty programs are often not closely monitored and protected, with inactive and insecure reward accounts providing an easy target.
For airlines, hotels and others hospitality businesses, this means fewer confirmed fraud cases, lowering the bar for fraudsters to wage successful attacks and enabling multiple attempts or even large-scale campaigns to go unnoticed. So how can hospitality companies prevent this growing threat? This blog will provide background on what’s driving hospitality fraud, the tactics fraudsters use to steal reward points and what businesses can do to protect their customers.
What’s driving the trend in loyalty point fraud?
The rewards points and loyalty program perks associated with hospitality and travel accounts can be redeemed for free hotel stays, discounted flights, upgrades or other valuable services. Additionally, fraudsters can use stolen credit card information linked to these accounts to make fraudulent purchases, often for expensive travel bookings or luxury accommodations.
But although the value of these ill-gotten gains can be substantial, customers may be less likely to tolerate security measures that add friction when accessing hospitality and travel accounts than banking accounts. This in turn causes businesses to prioritize user experience and view security as a compromise.
Examples and statistics for loyalty points fraud
As early as 2017, 60% of airlines reported instances of loyalty program fraud, and the trend has only grown since then. The success of these schemes has caused hospitality fraud to persist even after pandemic-related travel restrictions have lifted, with organized fraud rings and online marketplaces providing easy opportunities for fraudsters to buy and sell reward points online. Recent statistics on airline fraud show it accounts for 46% of fraudulent transactions.
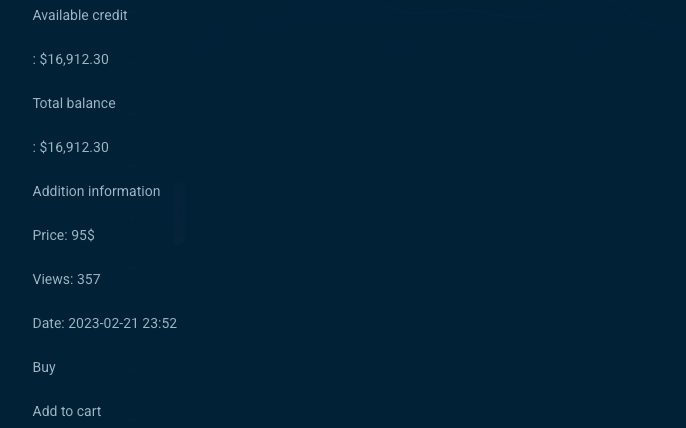
When researching fraud tools and marketplaces on the dark web, the Transmit Security Research Lab found numerous examples of loyalty points fraud on the Internet where miles and points can be sold, as shown below.
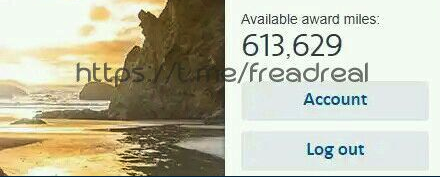
Obtaining these loyalty points may be easier for hackers than you might think. In 2023, hacker Sam Curry discovered massive security flaws in Points.com, a platform that handles points transactions for many major airlines. Among other risks, these vulnerabilities allowed access to 22 million orders containing frequent flyer numbers, credit cards and other customer data, the ability to add, remove or transfer points and permissions to modify customer accounts.
See more of what’s happening by reading our full Dark Web Threat Research Report.
Armed with a wealth of customer data and access to customer accounts, fraudsters can exploit a range of tactics that allow them to not only launch attacks, but scale them to large numbers. At this scale, fraudsters can profit even when selling the points at a substantial discount of their monetary value, making them even more attractive to the criminals who purchase them.
Fraud tactics targeting hospitality and travel businesses
Since airlines and hospitality businesses provide not only a lucrative target for fraud but less opportunity to be detected, fraudsters can employ a range of tactics to steal customers’ reward points and payment credentials.
Some of the tactics used for hospitality fraud include:
- Account takeover: Fraudsters can target individuals’ accounts by gaining unauthorized access to their login credentials through dark web marketplaces, brute force attacks, session hijacking or other methods. Once they have control, they can steal the users’ credit card information or reward points to use or sell.
- Fake travel websites: Fraudsters create fraudulent websites that imitate legitimate travel platforms with similar domain names and designs to trick users into entering their credentials onto the site’s fake login form, enabling them to access their victims’ accounts, including their rewards points or payment credentials.
- Phony offers: Fraudsters may use ads or phishing emails advertising fake travel deals or exclusive membership perks to entice users into providing payment details or membership information.
- Ticket cancellations to win flight credits: Fraudsters may use synthetic identity fraud or automation frameworks to enact new account fraud, then exploit cancellation policies to manipulate the system and fraudulently obtain flight credits or other perks without actually completing the intended travel.
- Mileage fraud: When legitimate users fail to submit their frequent flyer or rewards number on their trips, fraudsters can capitalize on this unclaimed value using brute force attacks applied to all passengers on a recent flight and retroactively claiming the miles to earn perks through digitals channels.
How to optimize CX while preventing loyalty point fraud
To solve the problem of reward program fraud, hospitality and travel companies need to invest in solutions that leverage fraud detection to deliver better user experiences, rather than viewing customer experience (CX) and security as a tradeoff.
Some of the services that can be used to optimize both CX and security include:
- Strong authentication with non-phishable credentials, including passkeys, which replace cumbersome passwords and OTPs with biometric authentication
- Fraud prevention that applies AI and ML to analyze a broader range of signals throughout the identity lifecycle to mitigate risk or reduce friction for trusted customers in real time
- Identity verification that could be used to validate the customer’s government-issued photo ID and a live selfie during the onboarding or account recovery process
- Identity orchestration that allows for businesses to test and optimize the order in which fraud detection solutions are invoked in order to maximize performance and streamline CX while strengthening security
- Identity management that unifies identities from all channels into one highly-scalable user store for greater visibility and control via a single pane of glass
While all of these solutions play a critical role, new challenges arise when organizations implement disparate anti-fraud and CIAM solutions that are difficult to integrate. You’ll end up with a disjointed CX, security gaps, detection errors and data silos that complicate decisioning and multiply overhead. To solve this challenge, Transmit Security delivers a fusion of customer identity management, identity verification and fraud prevention in a single, modular platform.
Unified identity security & fraud prevention
Mosaic by Transmit Security is the only identity security platform that unifies native fraud prevention, identity verification and customer identity management to effectively eliminate complexity, silos and blind spots — enabling more accurate, context-aware decisioning. With a powerful fraud engine and layers of orchestrated services, this AI-driven platform adapts journeys in real time to mitigate risk or remove friction for trusted customers.
Designed for large enterprises, Mosaic delivers the resilience, agility and scale to ensure business continuity for millions of customers while protecting your rewards program and loyalty points from fraud. It’s purpose-built to simplify fraud analysis, consolidate vendors and strengthen the implementation of passkeys and other security measures. To find out more about how Transmit Security helps hospitality and travel companies from the growing threat of fraud, request a meeting or read our case study on a leading airline that cut fraud by 96%.
Transmit Security provides the only fraud prevention engine that delivers context-aware intelligence and applies it across all identity security capabilities — for automated decisioning that’s laser accurate.



