Password-based authentication is the most common form of user authentication; however, it is notoriously insecure. Passwords are commonly weak, reused, or exposed in data breaches.
Other forms of authentication provide stronger security. For example, a physical token like a Yubikey or Google Titan is much more difficult to steal or copy.
The main advantage of a password-based authentication scheme is that it is quick and easy to implement. FIDO2, CTAP, and WebAuthn make token-based and biometric authentication more easily accessible to web applications.

What are FIDO2, CTAP, and WebAuthn?
FIDO2 is a collaboration between the FIDO Alliance and the World Wide Web Consortium (W3C) to enable web applications to use strong authentication. The FIDO2 protocol is made up of two components: the Client to Authenticator Protocol (CTAP) and the WC3 Web Authentication (WebAuthn) standard.
What is CTAP?
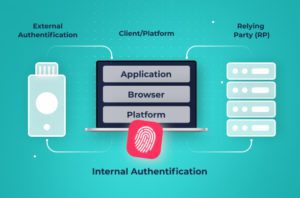
CTAP is a standard that enables communication between a “roaming” hardware authenticator and a client application. For example, CTAP can be used to communicate between a Yubikey and a web application running within the browser on a user’s computer.
Authenticators can also be built into a device, such as fingerprint scanners or facial recognition on a smartphone or computer. These platform authenticators do not require CTAP to secure their communications.
CTAP is designed to ensure that communications with roaming authenticators are performed using a secure authentication channel. CTAP can communicate with roaming authenticators over Bluetooth, Near-Field Communications (NFC), or USB.
What is WebAuthn?
The CTAP standard secures communication between an external authenticator and an application running on a user’s computer or in the browser. However, the browser isn’t the one that needs the authentication information.
WebAuthn provides an interface for communicating between an authenticator and a Relying Party, the service that actually uses this authentication information. WebAuthn abstracts away the details of the authenticator, so a Relying Party doesn’t need to know the details of how a CTAP-compliant roaming authenticator or a platform authenticator works.
WebAuthn eliminates the need for insecure passwords because it uses asymmetric or public key cryptography to set up a public/private keypair or “credential” for a website. The public key is sent to the website and is used in all future communications.
How Does WebAuthn Improve Security?
WebAuthn provides numerous security benefits compared to traditional, password-based authentication, including:
- Eliminating Passwords: WebAuthn is the official standard for passwordless authentication. Instead of passwords, websites use public key cryptography to authenticate and secure communications with users.
- Enables Strong Authentication: WebAuthn is designed to allow the use of stronger forms of authentication such as biometrics or security keys. These provide better security and more robust authentication than passwords.
- Reducing Data Breach Risks: Data breaches are a problem because they expose sensitive data such as password hashes. With WebAuthn, websites only store a user’s public key, which is designed to be public and creates no security risks if leaked or stolen.
- Reduces Phishing Threats: WebAuthn uses a unique public key for each website. The corresponding private key is never sent to the site, making it impossible for phishing sites to steal user credentials.
What is a WebAuthn supported browser?
The WebAuthn standard is designed to enable communicators between an authenticator and a Relying Party. A web browser can implement WebAuthn to allow it to relay authentication information from the authenticator built into or connected to a user’s device to the web application that needs it.
WebAuthn is implemented as an API, so supporting it requires a browser to implement this API. According to the FIDO Alliance, all major browsers implement the WebAuthn API, and most implement support for the CTAP and older U2F standards to varying degrees.
How do I use WebAuthn on my website?
WebAuthn is designed to be an easy method for websites to transition from insecure password-based authentication to using a more secure authentication method. Enabling WebAuthn requires two steps:
- Modify the login and registration pages to use the FIDO protocols for user authentication
- Deploy a passwordless customer authentication service that supports FIDO, such as the Transmit Security CIAM platform, to authenticate requests for FIDO authentication or registration.
These two steps are enough to get started with WebAuthn, but it’s also important to plan for the future. For example, WebAuthn may not be fully supported on all user devices, and it creates unique biometrics for each device. Applications may need to support both FIDO and non-FIDO authentication and have processes designed to ease transitions between devices. Transmit Security can help with designing and implementing these systems to provide a positive user experience while maintaining strong authentication.
Going passwordless with FIDO2
Password-based authentication systems are insecure and offer a poor user experience. With FIDO2, CTAP, and WebAuthn, web applications can painlessly implement strong authentication while also improving the user experience. The fact that it eliminates the risk of password leakage in data breaches and protects against credential theft in phishing attacks is just a bonus. Read more on FIDO2 passwordless authentication.