Virtual machines enabled a revolution in cloud computing by providing a way to deliver more scalable, cost-effective and flexible compute resources. But despite their legitimate uses, they also open the door to fraud by helping fraudsters evade detection, scale attacks or carry out other malicious activities.
To stop fraudsters from exploiting this technology, it’s crucial that businesses understand the fraudulent uses of virtual machines and the techniques for detecting them. This blog post will explain what virtual machines are, how they are used for fraud and how to identify and block their malicious usage.
Fraudulent uses for virtual machines
A virtual machine, or VM, is a virtualized computing system that can simulate different operating systems or run multiple OSes on a single physical machine. VMs are popular among fraudsters since they spend time on the dark web downloading tools and finding ways to exploit vulnerabilities. By using a VM, they can conduct these activities while protecting their physical devices from being traced or harmed.
VMs also pose a threat to businesses, as attackers can use them for a variety of malicious activities, including:
- Device spoofing: VMs allow fraudsters to mimic a different device than what they’re actually using. If a fraudster knows their user’s trusted device, they can use a VM to pose as a similar one.
- Evading detection: Through the use of VMs, attackers can disguise their device and pass reputation checks performed during device fingerprinting to identify and block known malicious devices.
- Scaling attacks: Running multiple virtual environments on a single physical machine helps attackers automate and scale attacks by creating multiple virtual instances with distinct identities.
- Overcoming rate limiting: Attackers can use VMs to avoid controls that limit high-rate and high-velocity requests from a single device, as they are able to emulate multiple machines with different device fingerprints.
As a result, the use of a VM can be an indicator of attempted fraud, especially when its usage is uncommon for a trusted user or accompanied by other risk signals and anomalies.
Research experiments to identify VMs
When detecting VM usage, we can split the data into two categories:
- VMs that declare they are VMs
- VMs that disguise their usage, as in device spoofing
Those in the first category carry distinctive signatures of a VM vendor or VM-related GPU and CPU signatures, as you can see below.
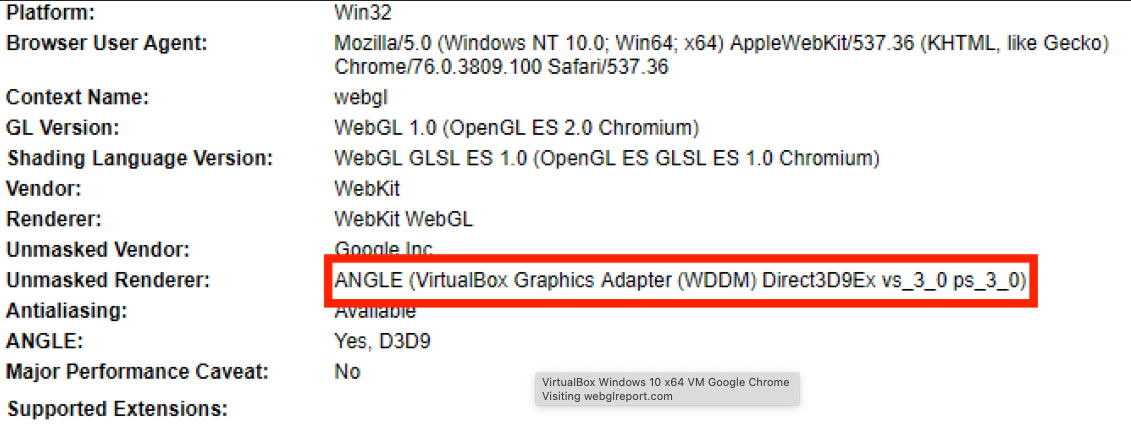
However, VMs that disguise their usage can be tricky to spot at first glance. But if we dive a bit more deeper, we can discover some interesting properties that indicate we’re not facing an innocent machine.
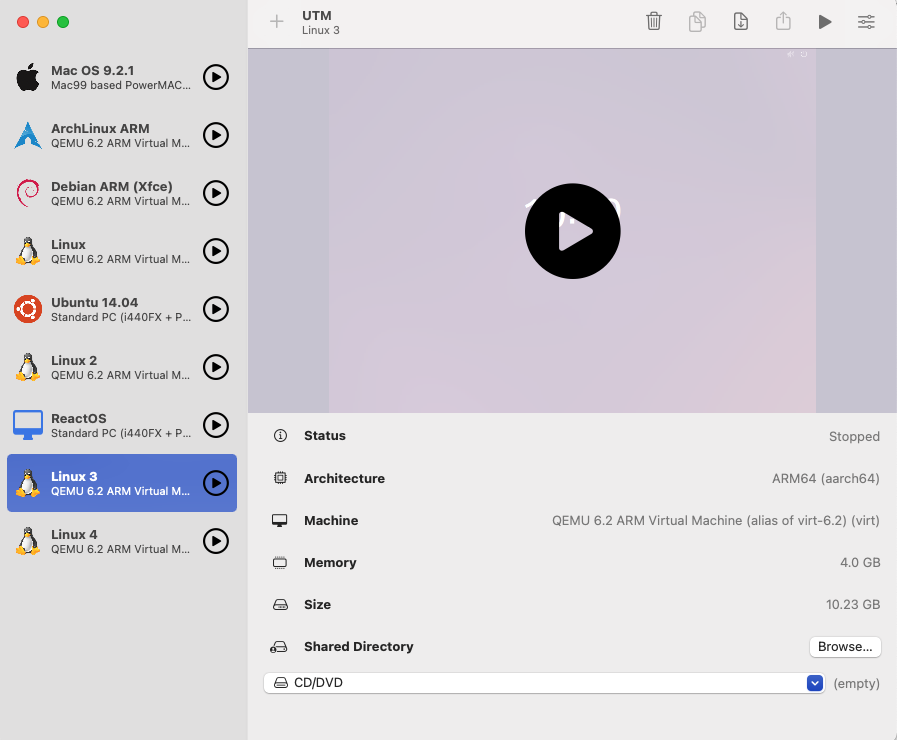
To help detect these properties, our Security Research Labs studied the properties of VMs by creating various virtual machines and observing the output of our SDK. We used a cloud-based windows machine, UTM, for local virtualization on a MacBook with Apple silicon and a VirtualBox from a Windows PC.
Below, you can see an example of a UTM machine and its settings.
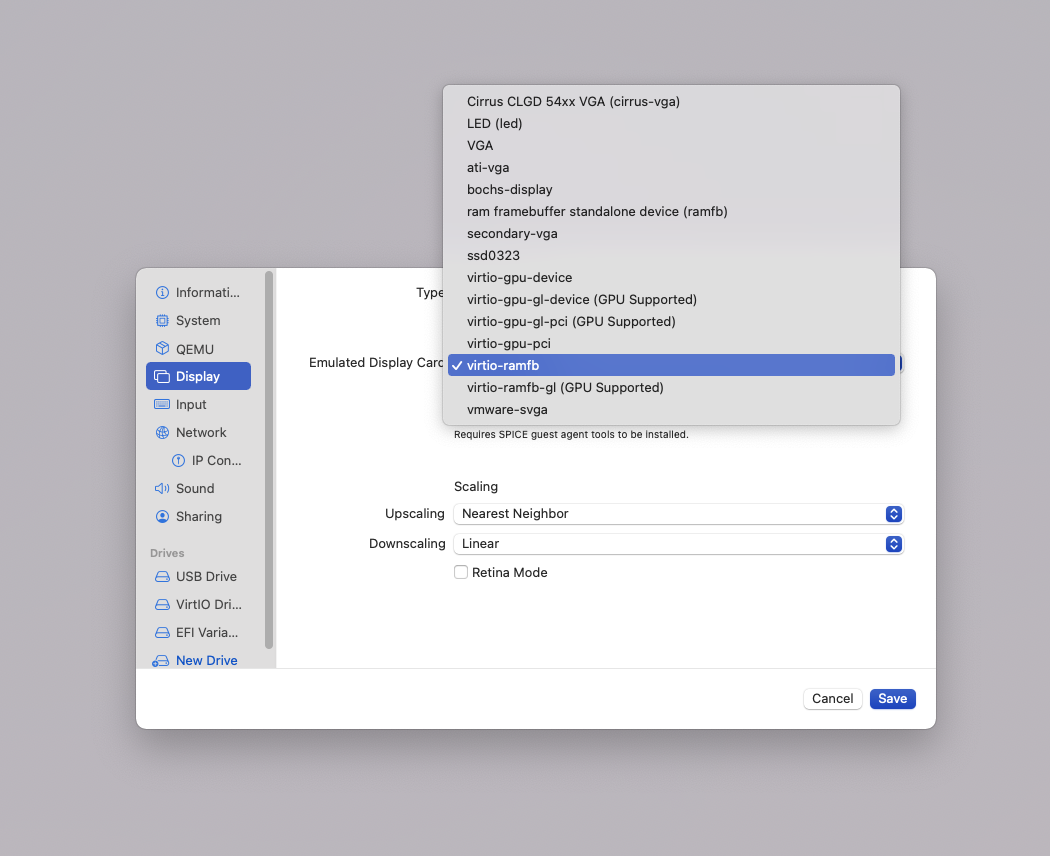
And here is an example of our demo site running on the Linux distribution Kali Linux, an open-source operating system that includes tools that allow users to control and monitor information about running VMs.
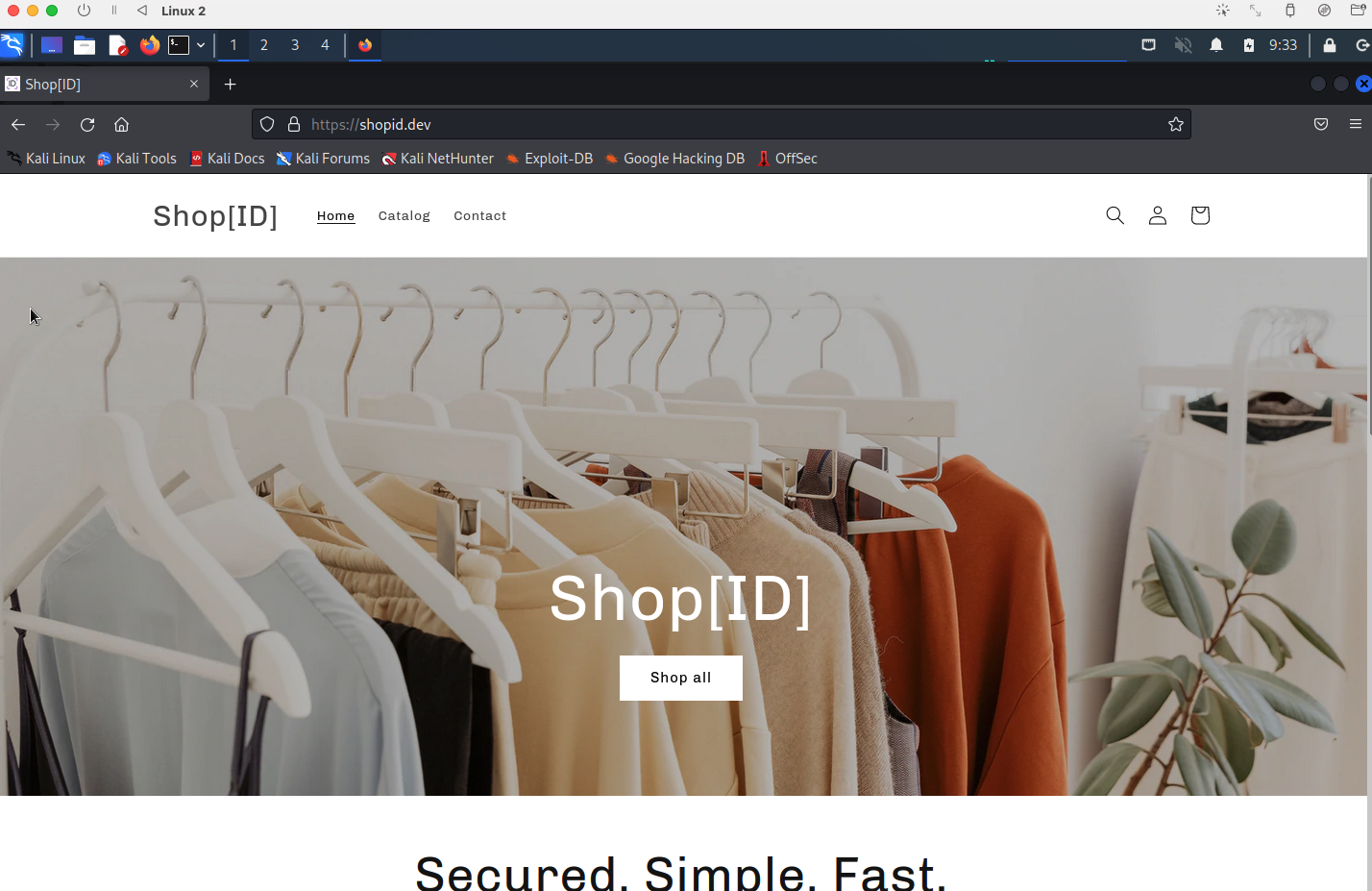
Using these tools, our security researchers performed tests and trials that provided leads for new detection methods of VMs, which we describe in the next section.
Detection methods
GPU and CPU tests
Since most normal user traffic does not come from VMs or spoofed devices, we have a good amount of data that helps us understand each hardware platform’s performance by performing computational and rendering tests. Using this data, we can sample each hardware platform’s performance and compare it to each new instance from the VMs we created in order to determine its standard deviation from the mean of the distribution.
Core number
All modern physical machines these days come with at least two logical cores: one physical and one thread, which is a sequence of instructions within a program that can be executed by a logical core.
Since physical machines typically have a fixed number of logical cores determined by the underlying hardware architecture, discrepancies in the number of cores expected — such as a very high even number of cores or an odd number of cores with signatures of known CPUs — could strongly indicate the use of a VM.
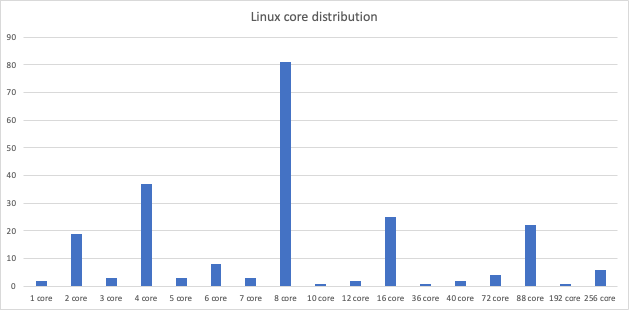
Platform mismatches
In modern computer hardware, there are two main architectures, RISC (reduced instruction set computer) and CISC (complex instruction set computer). RISC CPUs and platforms are primarily known as ARM CPUs, which can be found in almost all mobile devices and some desktop computers, such as Apple M1s. CISC CPUs and platforms are mainly known as x86 and come in 32 or 64-bit configuration (Intel and AMD).
From researching odd-numbered core instances, we noticed that sometimes x86 CPUs came with ARM-related graphics and vice-versa, such as AMD CPUs that came with Intel internal graphics. We can also sample all platform instances and find the most common ones for each platform in order to spot anomalies.
Device characteristics
Device characteristics can also be used as factors to suggest the possible use of VMs. This includes:
- Memory: VMs typically have a pre-allocated amount of memory that is defined during their configuration, so discrepancies in the reported memory amount of the device may suggest VM usage.
- Pixel and screen depth: Virtualized environments might have limited or non-standard display capabilities due to factors like virtualized graphics drivers.
- Battery level and charging: The absence of battery-related information or discrepancies in battery behavior (e.g., charging status without an actual battery present) could suggest virtualization.
- Screen resolution and resolution ratio: Specialized virtualization setups may have limitations on screen resolution or rely on emulated hardware, which could result in non-standard screen ratios.
By sampling the clean data and looking for anomalies, we can gain even more information about the specific patterns in device characteristics that can indicate VM usage, as seen in the graph below showing the distribution of screen resolution.
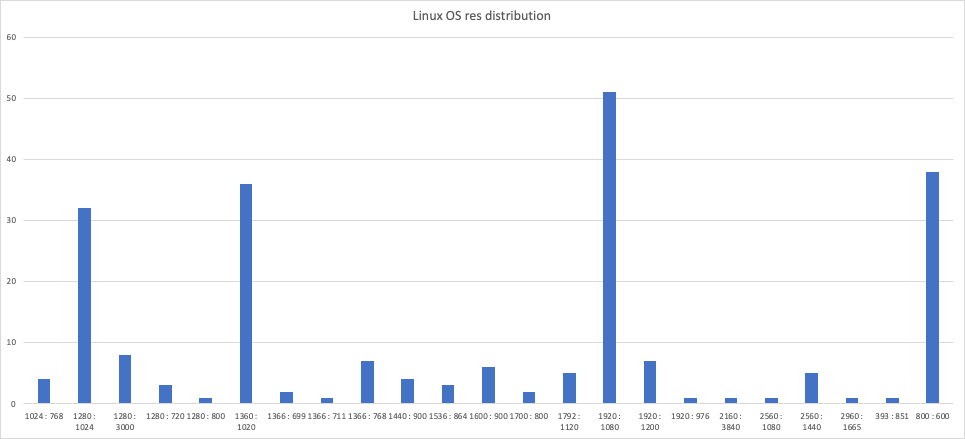
Improving fraud mitigation through VM detection
The new insights and detection methods of VMs and spoofed devices that we learned through our research yielded new features and segmentations of our data that can be used to optimize the detection of fraudulent VM usage. Transmit Security’s Detection and Response Services leverage the information gained from our Security Research Labs to optimize our machine-learning based risk engine to detect emerging threat patterns.
By training our machine-learning models with the data we learned from these experiments, we can not only identify hard-coded features of virtual machines, but generate more labels for our data to use in supervised machine-learning algorithms and leverage it for more advanced machine-learning techniques, such as unsupervised or semi-supervised algorithms.
To find out more, read about how Detection and Response Services use machine-learning based anomaly detection to uncover threat patterns or check out our Attack Simulator to see for yourself how VM-based attacks differ from legitimate traffic.



