Increasingly, machines are the dominant force of digital business. And with more machines and machine secrets there are, the bigger the attack surface. And the numbers of machines are only going to increase in the age of generative AI, cloud and automation. So the question is how can you reduce risk in every way possible?
In this post, we are providing expert recommendations for mitigating risk throughout the machine identity (MIM) lifecycle. You’ll learn best practices, including ones that are often overlooked. And finally, we’ll explain why machine identity orchestration, a completely new realm, is essential to handle today’s highly-fragmented MIM solutions across hybrid and multi-cloud environments.
The complexity and risk of machine identity management
In our previous blog post on machine identity management (MIM), we defined the critical MIM identity lifecycle stages and called out the risks associated with each task — from identity creation and provisioning to identity renewal, revocation and incident response.
In hybrid and multi-cloud environments, having disparate, multi-vendor MIM solutions creates challenges for operations, governance and security, but it’s unavoidable due to the wide variety of machine types. MIM requires many, and often complex, backend solutions, including cloud-based key managers, on-premise hardware security modules (HSMs), secret managers, public and private certificate authorities, certificate lifecycle managers, mobile device management and other IAM solutions.
All of this adds complexity, which can largely be resolved with the right orchestration and MIM solutions that manage and secure the full identity lifecycle. Let’s take a look at the critical machine identity lifecycle stages, risks and industry best practices aimed at mitigating risks.
The full machine identity lifecycle risk & mitigation
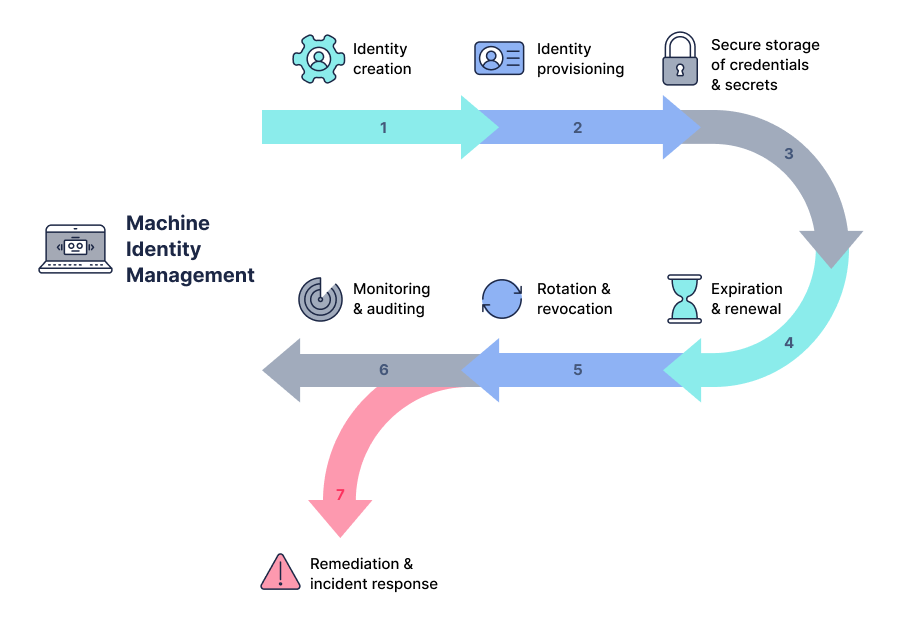
Let’s take a closer look at the 7 machine identity lifecycle stages, risks and industry best practices aimed at mitigating risks:
- Identity creation (aka key generation): This involves generating unique identifiers, such as certificates, credentials or API tokens for each machine. Note that key generation and storage often overlap in functionality.
Risks: Risks can include insecure generation of credentials, for example, if it’s purely software-based methods the keys are more vulnerable. Below (#2 and 3) we cover the risks of credential storage and key sharing, which links together many machines, making them indistinguishable from each other.
Recommendations: Leverage strongly generated unique identifiers, like certificates or other “hard-to-clone” cryptographic-based methods. Generating keys securely is the first step in establishing a robust key management process. It is essential to use a trusted and well-implemented key generation algorithm that ensures the randomness and uniqueness of the keys. Keys should also be generated and stored (see #3) in a secure environment, free from potential threats or compromises to prevent unauthorized access. By introducing governance, policies can be set and maintained, which can help enforce corporate information access and security policies. By having a machine identity policy control, you can manage the challenges associated with duplicate credentials, a problem we covered in our first MIM blog. - Identity provisioning: Provision identities to the machines directly or by using a centralized system that distributes and installs the identities on the machines.
Risks: Insecure distribution methods or unauthorized access to the identity files during provisioning can expose the identities to interception, tampering or theft.
Recommendations: Track and govern the use of secure provisioning methods. Implement policies and controls that take into account usage restrictions, network access, and tracking endpoints to which the machine identity is delivered. In addition, enabling secure communication methods when credentials are provisioned to any machines or workloads. Common best practices leverage protocols such as enrollment over secure transport (EST) standards to ensure mutual authentication and secure transportation of machine identities. Look for MIM solutions that ensure secure communication and control methods across the entire machine identity lifecycle — consistent with zero-trust principals. - Secure storage of credentials and secrets: Proper key management practices include key generation, encryption, secure storage mechanisms and access controls.
Risks: All key generation and storage mechanisms are vulnerable to unauthorized access, data leaks or theft.
Recommendations: Ensure that any and all credential storage leverages software and, in some high-assurance cases, hardware. Secure storage mechanisms that should be considered vary in form factor, such as: hardware security modules (HSMs); cloud (dedicated or shared), on-premise database storage and other secure elements for mobile devices, like Apple’s Secure Enclave and Trusted Platform Modules (TPMs) for Windows. Increasingly, secure elements are more widely available on servers, such that they can be leveraged in an on-prem data center and/or hosted by a cloud service provider.
- Expiration and renewal: Machine identities have a specific validity period, after which they expire and may need to be renewed to ensure continued operations.
Risks: Expired certificates, for example, can lead to outages or disruptions in machine-to- machine communications, especially if they aren’t managed properly.
Recommendations: Leverage a unified machine identity system that can determine in-real time if machine credentials are expired and/or compromised. To handle the sheer scale and variety of machine identities, you’ll need machine identity solutions that leverage AI and machine learning to automate and manage renewals. This will remove a heavy burden and risk.
- Rotation and revocation: It’s important to regularly replace (i.e. rotate) or revoke long-lived or compromised machine identities.
Risks: Expired or compromised machine identities are a security risk that can result in unauthorized access or misuse if you allow the identities to remain active.
Recommendations: Periodically assess the validity dates and security of all machine identities. Fraud and cyber incidents could require some machines to be revoked. In addition, crypto-agility incidents, such as vulnerabile hashing algorithms, could require security leaders to revoke and renew machine credentials. For example, in 2017, when Google found security flaws with Symantec, they decided to remove trust for their certificates (aka machine identities). This caused many large and small organizations to have to revoke and reissue their website and application identities, browsers and other applications in order to remove displayed warnings, error messages and remedy outages. And while out of scope for this blog, preparing for a post-quantum computing world, organizations will have to determine how and when they will revoke and reissue credentials that support and can mitigate quantum attacks. More on that in another future blog!
- Monitoring and auditing: For compliance and security analysis purposes, it’s vital to continuously track the usage of machine identities, monitor their validity and access patterns and generate audit logs.
Risks: Full visibility of all machine identities in today’s complex IT environments is essential to detect anomalies, suspicious activities or unauthorized use.
Recommendations: Monitor and audit the security and integrity of machines at all times. This means you’ll need automated machine identity management solutions with the ability to monitor issues that impact, risk, trust, fraud, bad bots and bad behavior in real time.
- Remediation and incident response: You may need to rapidly revoke identities, replace keys, run forensics and implement measures to prevent future incidents.
Risks: Lack of visibility into the usage and behavior of machine identities can hinder incident response efforts and compromise the overall security posture.
Recommendations: Update your incident response playbook to include much of what’s recommended in #6 above, covering any and all related machines and their security posture. Specifically, your incident response plan should cover any and all elements related to machine identities (i.e. certificate authorities, secret managers, key vaults, etc.). Your playbooks should call out the specific solutions, as well as the internal product or service owners and highlight the actions. Unfortunately, this is a tedious task without the use of MIM orchestration. The lack of orchestration creates blindspots for many organizations today (see the section below).
In order to improve your incident response posture, in this increasingly machine-driven world, risk-aware, response and crypto-agile MIM solutions are now necessary.
Machine identity orchestration pulls it all together
Since machines will increasingly leverage cryptographic-based identity and security methods, the notion of crypto-agility needs to be considered with your IR plans and playbooks.
And finally, while not a specific identity lifecycle stage, machine identity orchestration is essential in order to bridge the gaps and correlate data and functions between disparate, multi-vendor (and multi-cloud) solutions. As mentioned earlier, the wide variety of machine types, calls for multiple backend solutions, such as cloud-based key managers, on-premise HSMs, secret managers, public and private certificate authorities, certificate lifecycle managers, mobile device management and other IAM solutions. Ultimately, MIM orchestration can help organizations become more crypto-agile.
Fragmentation in this space is an on-going issue. And while many cyber and identity-security leaders have some machine identity related products and services already deployed, the explosion of machines has now created management complexity and visibility problems. Due to product silos, orchestration is the only way to unify and simplify machine identity management, improve security and gain control of the full machine identity lifecycle.
Risks: Lack of visibility and control across the disparate machine identity solutions leaves security gaps and blind spots that cause you to lose track of workloads entirely. Misconfigured machines or rogue machines can leave exposures that can lead to outages or breaches. In addition, the MTTR (mean time to response) can be negatively impacted since security teams have to traverse multiple machine identity products across their hybrid and multi-cloud environments.
Recommendations: Utilize MIM solutions that leverage already established identity orchestration capabilities and provide an intuitive, easy-to-use visual interface that provides a single pane of glass unifying all of your disparate MIM products. Elements in the interface should include integrations into downstream machine identity products such as HSMs, cloud key vaults, secret managers and other relevant machine identity solutions.
Ultimately, orchestration enables you to manage and unify policies across hybrid, multi-cloud environments. It will simultaneously reduce your incident response time and provide the agility (including crypto-agility) to meet ever-evolving business needs, operations and/or security issues. Lastly, machine identity orchestration can clear the path for security stack consolidation. Gartner has identified that 75% of CISOs and their teams aim to consolidate security stacks. With orchestration, security leaders can coordinate the usage of all downstream products and services. Services that are no-longer used, are outdated or overlap in functionality could be gracefully retired. As an emphatic rallying cry for cyber-identity teams, we are introducing the phrase: “Orchestrate to consolidate!”




