OpenBullet, a legitimate web testing tool for developers, has grown wildly popular among hackers. Weaponizing open-source software is not new, but this one has cybersecurity teams on edge due to its ability to automate highly deceptive threats. The software not only runs credential stuffing attacks on autopilot but also provides a rich feature set that enables attackers to evade detection by most bot and fraud defenses.
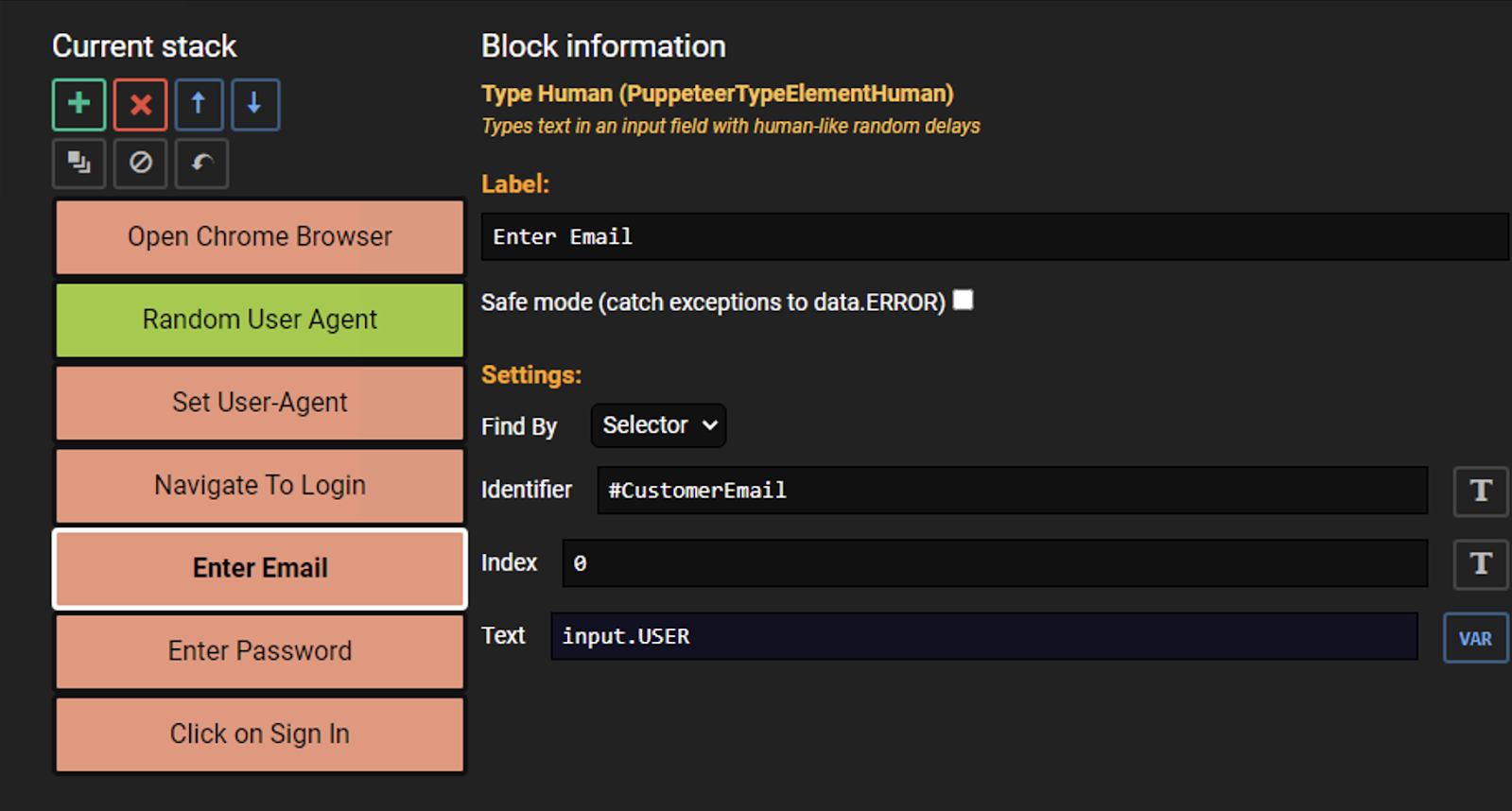
For example, when OpenBullet is paired with Puppeteer, an automation framework, attackers can select, “Type Human,” a feature described in the UI as, “Types text in an input field with human-like random delays.” That’s just one of many obfuscation techniques they have at their fingertips.
In this blog, we’ll cover the capabilities of OpenBullet that make it easy for fraudsters to launch stealth account takeover (ATO) attacks at scale. We’ll also explain how to identify OpenBullet attacks with the right detection mechanisms. We’ll tell you exactly what’s needed and how to put it to work.
What is OpenBullet, and what’s new in 2.0?
As a web testing tool, OpenBullet enables developers to perform specific requests on target web pages, as part of automated penetration testing, for example. It can be used to scrape and parse data, make direct API requests and use automation frameworks like Selenium and Puppeteer.
It’s generating excitement in the attacker community for obvious reasons — it’s free, powerful and very user-friendly — especially with the recent release of version 2.0. Attackers take advantage of its up-to-date configurations and dedicated forum, which is highly active and responsive.
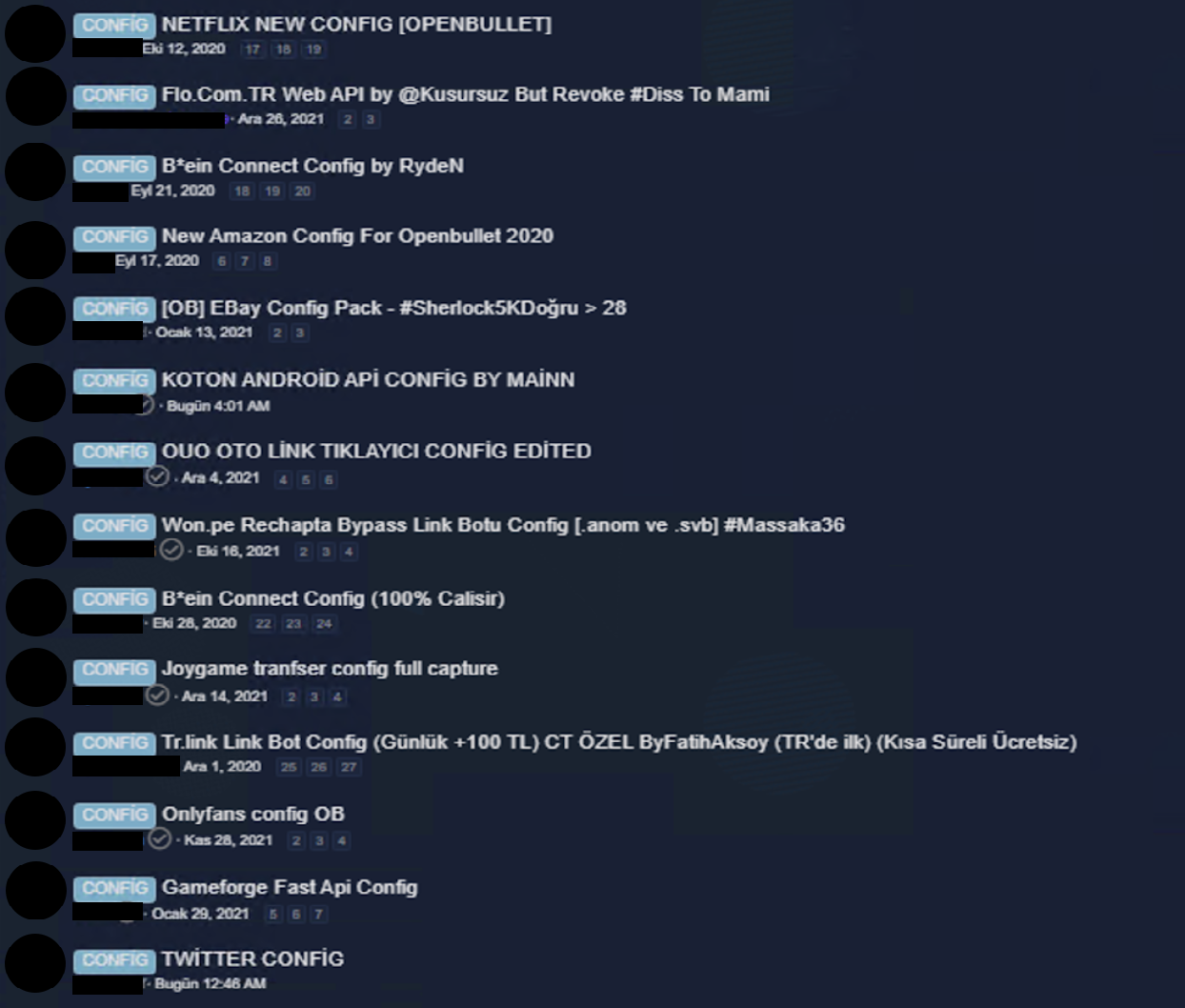
In the screenshot below, you can see a list of configurations available on a dark web forum that is designed to target popular services like Netflix, Amazon, OnlyFans and Twitter.
How OpenBullet is abused
Attackers are most frequently using OpenBullet for credential stuffing — a type of brute force attack that leverages stolen login credentials from other websites in an attempt to take over existing customer accounts. Fraudsters rely on the fact that most of us reuse the same or similar passwords for many accounts, and they use OpenBullet to stuff stolen credentials into login fields, testing them on specific websites.
What’s especially concerning is that this free tool allows the attacker to appear like a real user, making attacks difficult to detect. If malicious actors succeed when logging in, they can access sensitive data, buy goods, transfer funds or redeem rewards points.
OpenBullet enables attackers to:
- Use a combo wordlist (usernames and passwords), which the attacker can find on the dark web
- Make requests using distributed IPs via proxies to hide the attacks
- Manipulate request headers/cookies to avoid being marked by bot mitigation solutions
- Use dedicated OpenBullet services to solve a variety of CAPTCHA challenges
Using proxies enables fraudsters to make multiple login attempts with a different IP address each time. OpenBullet even enables the attackers to pause between login attempts to avoid sounding an alarm generated by a high number of attempted logins in rapid succession.
By executing JavaScript, storing cookies and solving CAPTCHA challenges, OpenBullet login attempts appear much like legitimate customer activity. On top of that, the ability to use combo wordlists, proxies and random user agents creates a formidable foe — automated and hard to detect.
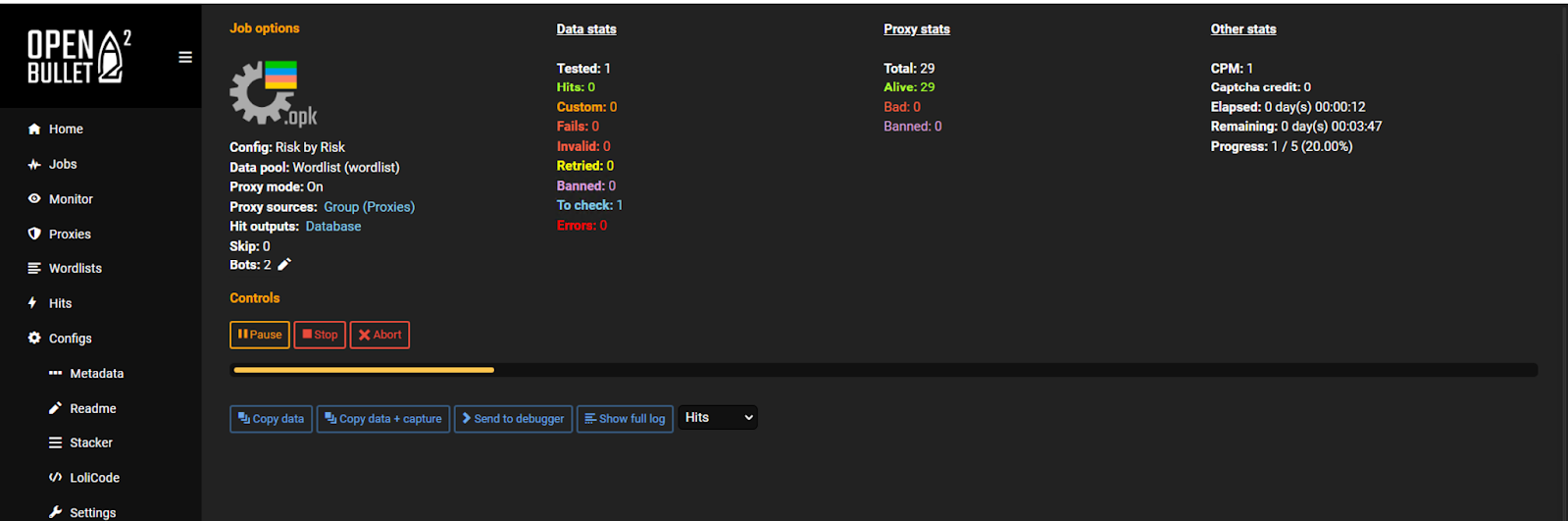
To simulate an attack, Transmit Security Research Lab used the Puppeteer testing method in OpenBullet to run requests.
After setting the configuration, we created a dedicated job to run requests to the demo site using our fake wordlist and several IPs (from the proxy list in OpenBullet).
How to detect OpenBullet attacks
Looking at the research data, we saw that OpenBullet’s traffic has well-distributed identifiers on each login request (such as IPs, device IDs and user agents), which would make it difficult to detect malicious actors. Other aspects of the traffic, however, can be used to determine if the user is automated or suspicious.
With the right detection mechanisms, it is possible to identify and mitigate credential stuffing attacks that use OpenBullet and similar automation tools. In this section, you’ll learn about the three most effective methods.
1. IP/proxy reputation
OpenBullet enables the use of proxies, which can be used to make attacks appear like normal, distributed traffic. But the use of proxies, or any single indicator of risk, cannot be used alone to identify an attack, since there are legitimate reasons for using a proxy server.
Checking the reputation of IP or proxy can reveal much more about the source. Data collected from customers and IP enrichment services can indicate if the proxies/IPs have been used for malicious activities.
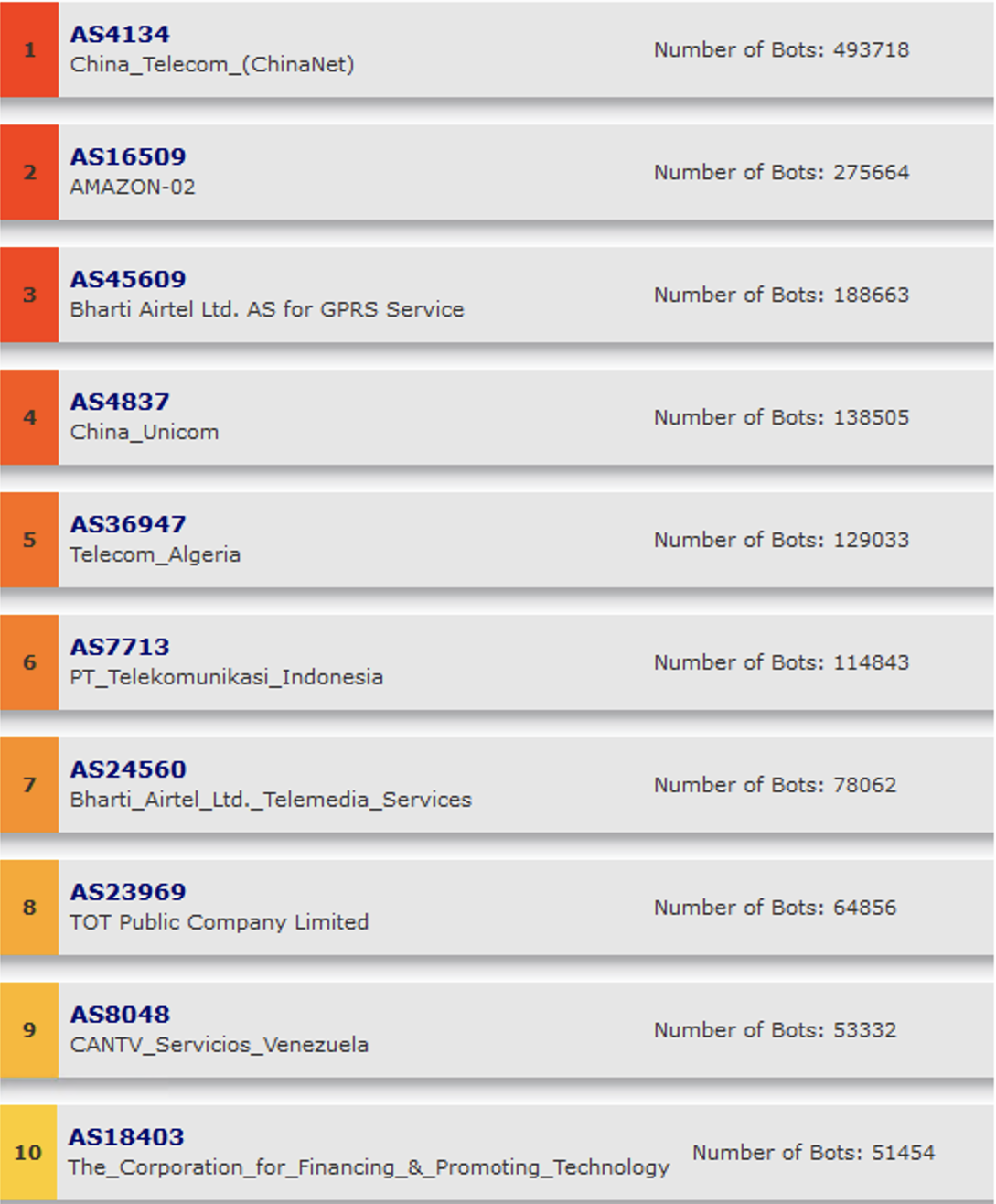
Below you can see the top 10 autonomous system numbers (ASNs or sets of IPs) most often used for bot and fraud attacks. Topping the list is an ASN from China, which has been used in nearly 500,000 bot-powered attacks.
2. Behavior anomalies
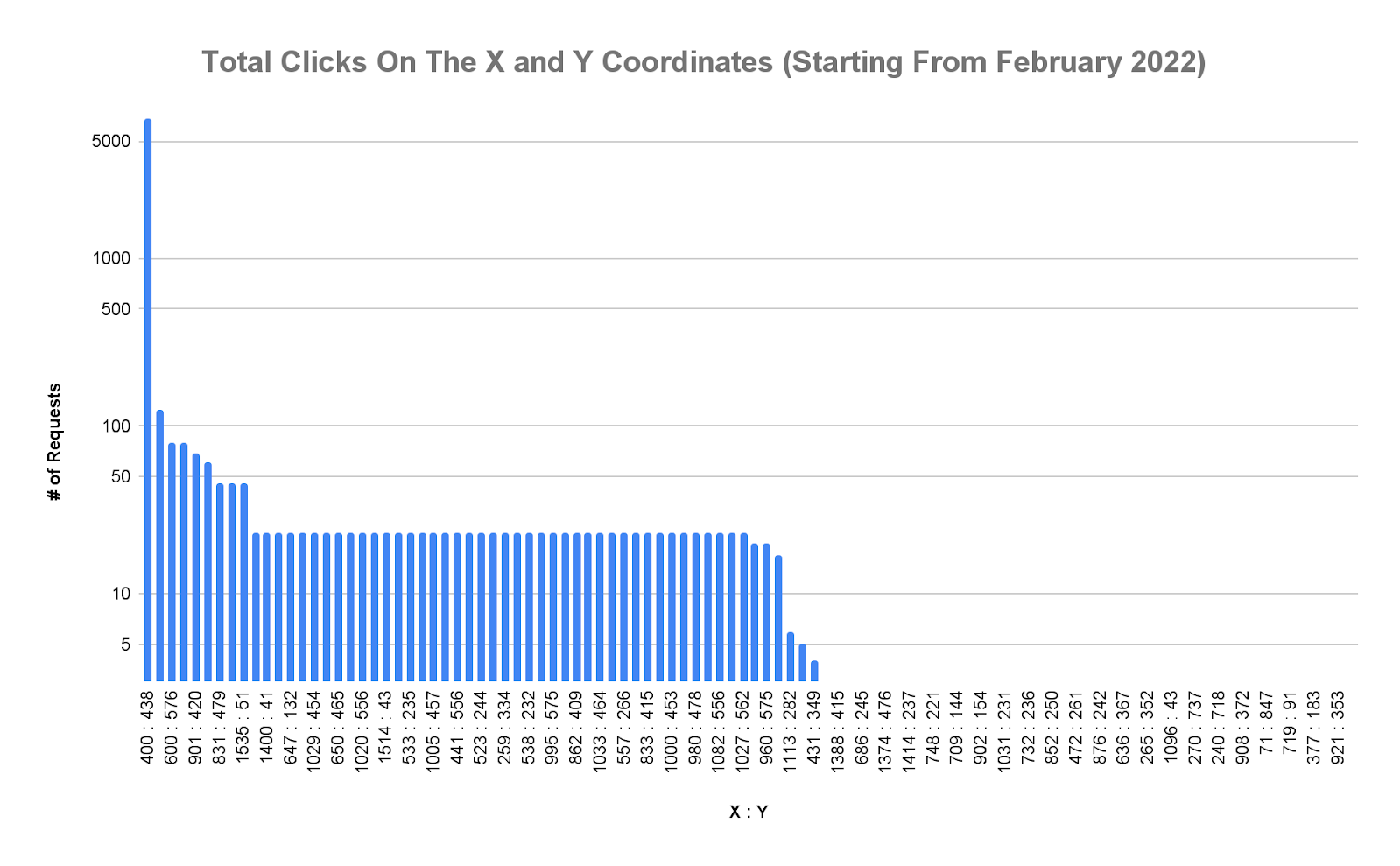
A high concentration of clicks on the same exact coordinates of the login button and the absence of mouse movements are good indicators that an automation tool is being used behind the scenes.
The graph below shows the exact coordinates of where the login button was clicked, which is expected to vary for real users. However, when using OpenBullet, all clicks are made in the 400:438 coordinate. A disproportionate number of clicks on the same coordinate may indicate the usage of an automation tool.
As for mouse movement, the left image shows a full interaction with a website — which includes choosing a product, moving to the login page, and pressing the email, password and login buttons. These interactions can be seen in the mouse movements and are a
good indication of legitimate usage.
In the right image, there is only a single click on the login button and no interaction with the site. This behavior can indicate that automated traffic is interacting with the site.
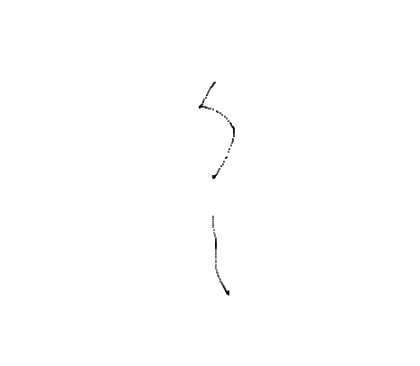
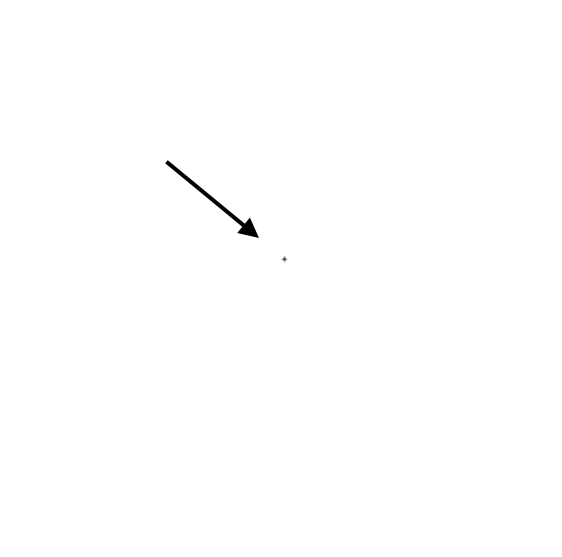
Normal mouse movements A single mouse click on the sign-in button
3. Device reputation
Automation tools, such as OpenBullet, leave some bread crumbs when controlling the browser. On the other hand, if browser requests are made by real users, the attributes, such as cookies or headers, tend to vary between the requests. By contrast, requests made by automation tools all have the same attributes or certain anomalies. As part of our research efforts, we are investigating and mapping these suspicious indicators to enrich our detection capabilities.
Putting your defense into action
With OpenBullet’s powerful capabilities, updated configurations and responsive forum, fraudsters can automate credential stuffing attacks on steroids. It’s easy to see why it’s grown to be one of today’s most popular fraud tools, and we can expect to see more of it.
So let’s get ready. How can you implement and leverage the three detection methods that will empower you to identify and stop OpenBullet and other automated attacks?
Automated account protection – To defeat OpenBullet, you must be able to assess IP/proxy reputation, behavior anomalies and device reputation — plus all that’s happening, all signals, in real time. Continuous assessments should analyze risk, trust, fraud, bots and behavior — throughout the identity journey. With accurate detection and risk/trust recommendations, you can automate an immediate response to stop OpenBullet in its tracks.
Protecting accounts without hurting customer experience (CX) – This requires dynamic fraud detection that leverages advanced machine learning and AI. The solution must be smart enough to distinguish between good and bad activity — even when fraudsters use evasive tactics or when trusted customers switch to a new device or change their behavior.
To minimize false positives and false negatives, you need a context-aware solution that examines a broad range of telemetry and combines multiple detection methods, such as advanced device fingerprinting, bot detection and behavioral analysis. Transmit Security’s Risk, Trust, Fraud, Bots & Behavior Detection, a cloud-native service, delivers actionable recommendations that can be used to trigger the right action, at the right time. You can even automate protection against new threats when they first emerge.
See how our Risk, Trust, Fraud, Bots & Behavior Detection Service can help you rapidly detect and respond to credential stuffing and other ATO attacks powered by OpenBullet.



