How to Implement a Passwordless Solution in Hours, Not Years
A common misconception about customer identity projects is that they take years to complete. While this may be true with some solutions, it’s simply not the case for our passwordless authentication service. Unlike many passwordless providers or building your own DIY solution, Transmit Security can have your passwordless solution up and running in as little as a few hours.
This article will show you how Transmit Security can cut your deployment time for passwordless from months or years down to hours. First, let’s discuss why and how Transmit Security saves you so much time.
The passwordless “Build vs. Buy” status quo (or “Why can’t I build it myself?”)
Sometimes organizations look at the fact that Transmit Security is built on open standards like FIDO and OpenID Connect (OIDC) and say, “Why can’t I do this myself?” It’s a valid question if you have vast resources and many dedicated programmers already. So, why would you avoid a DIY solution if the solution is so straightforward? It’s an enormous amount of work, and it will incur far more costs and development time than even the largest organizations are willing to stomach.
Finding identity experts for your DIY project
Think about what it takes to develop your own IAM project — not passwordless, just any IAM project at all. First, you have to find developers that can (and want to) work in the identity space, and very few specialize in that environment. Even fewer are free agents because companies snatch up identity experts the moment they’re available, which is why they command top dollar for their skills.
If you want your own non-specialized teams to start working within the identity space, they’ll quickly find starting from scratch to be a grueling process. Churn will be high, and turnover will become a constant reminder of the enormity of this project.
The never-ending list of tasks and interconnected problems
It’s true that working with WebAuthn, OIDC and FIDO can be relatively easy using off-the-shelf open-source libraries. But this represents a fraction of the problem at hand. Simply because your organization can eventually develop a FIDO login system does not mean you have solved the entire passwordless problem. Here are just a few of the challenges that lie ahead of you:
- Registration flows
- De-registration flows
- Re-registration and recovery flows
- Multiple device support
- Multiple app support and managing separate FIDO credentials
- Multiple channel support for web, iOS and Android
- Non-digital channels (i.e., call centers and kiosks)
- Service or server installation and management
And that’s just the start!
During development, each completed task leads to a daisy-chained series of other issues to resolve. Because identity is so comprehensive and intimately tied to everything else in your cybersecurity stack, there’s an endless list of problems to solve… even long after the platform itself is in production.
The “three screens” problem
It’s easy to forget that in the current status quo of CIAM, you have to handle every project three times over:
- Once for Web applications
- Once for iOS
- And once for Android
That means three times the “screens,” UIs, and platform-specific issues. User interfaces alone can be very expensive to build and roll out, and they require extensive testing, especially for customer-facing authentication flows. Later, this translates into expensive maintenance because each operating system’s release cadence differs.
Servers and infrastructure
While WebAuthn is simply an open standard, FIDO is a complex service you must install and manage. Despite the fact that there are a selection of FIDO server technologies available, they are typically packaged alongside other offerings that incur additional fees — and can’t be separated from the bundle. Even if you have the extra budget to shell out for products you neither need nor can use just to deploy a FIDO server, that server’s effectiveness becomes your responsibility.
If you install and run your own open-source FIDO server, all the costs of maintenance, zero-day exploits and hardware stability fall solely in your lap. These become daily problems that your team must monitor closely to avoid downtime or data breaches. Compare this to Transmit Security, which has a FIDO-certified backend that works automatically and invisibly to you. No additional work on your end is required.
Why DIY when you can buy?
By struggling to create your own passwordless solution, you will incur significantly increased cost, effort and time to build. Your engineering teams won’t realize this until much later in their project cycle because their focus will likely be granular and restricted to the basics. Eventually, it will become apparent that 12-24 months was an optimistic timeline after all.
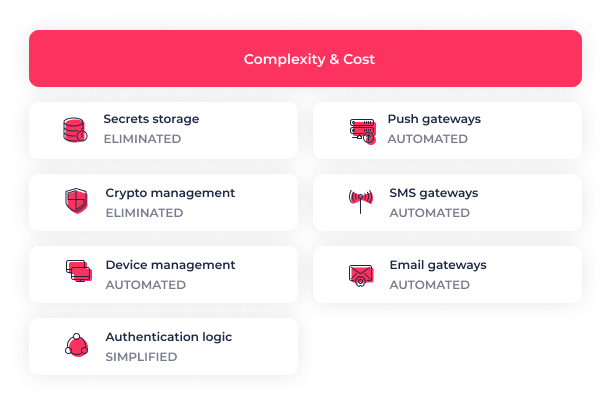
Transmit Security is a list of things you don’t have to do
Based on the previous section, consider the list of things you have to build or configure when you construct your own passwordless solution. Transmit Security is essentially a list of things you don’t have to worry about because they’ve already been created, polished and perfected by identity veterans. Everything we discussed in the previous section? It’s in a mature state of perfection thanks to years of work and the focused expertise of the world’s most accomplished identity specialists.
But Transmit Security isn’t just about passwordless, and it’s not just an authenticator. It’s a complete identity experience scheme backed by seamless authentication that extends beyond both digital and non-digital environments. Transmit Security is built from the ground up to eschew the difficult development of verification flows, management of risk perspectives, pre-emptive multi-device binding and built-in recovery processes.
Most significantly, it accomplishes all of these capabilities in virtually no time at all thanks to modular architecture and easy configuration. Because it is built on open standards and a versatile API, Transmit Security can quickly plug into any existing identity stack — all without replacing your existing identity flows and methods. It’s completely IdP-agnostic, meaning that any incumbent provider can work with Transmit Security’s open architecture. Everything required can be handled by one person with only very basic knowledge of the underlying code. It’s as easy as it can possibly be without sacrificing any security or ease of use for your customers.
Configuring Transmit Security in just a handful of steps
Configuring Transmit Security is as simple as launching a tenant, adding your unique branding (and a new passwordless login button) and integrating a Transmit Security client library. Then, Transmit Security allows for simple binding between user identities and their accounts. It’s fully automated standards-based authentication without the tedious development or snowballing cost.
Because Transmit Security is so streamlined and rapid-fire, proofs of concept can be prepared in a day or less. If you’re ready to see your organization’s authentication pipeline made even easier and safer by plugging in Transmit Security, it’s a simple matter of configuring a handful of variables. But don’t take our word for it — you can easily see it for yourself in 24 hours or less!
Transmit Security makes a passwordless solution an attainable reality now
The tide is turning on existing password and OTP methods. According to Gartner, within the next year, 90% of SMEs and 60% of global enterprises will begin a passwordless initiative in more than 50% of use cases. That effectively moves the competitive curve well within passwordless territory, and companies that lag behind will look less attractive to customers when it comes to convenience and safety.
Even if you began building a solution or working with a legacy solution now, it could take years to reach production — and that’s just for the platform. But it’s not too late. With Transmit Security, you can expect to deploy with minimal development and in record time. Learn more about how we can deliver passwordless for your organization in a few hours or less.



