How do you know who is registering an online account with your business? The answer is complicated by the rise of ‘Frankenstein fraud,’ also known as synthetic identity fraud, which combines stolen data belonging to a real person with fake information to create a new, fraudulent identity. For example, the criminal might use a stolen Social Security Number (SSN), the victim’s real name and date of birth (DoB) along with a fake address plus a phone number that’s in their control.
By using some real identity data, they’re more likely to appear legitimate and evade detection by legacy and DIY data validation methods. In some cases, they’ll use their own phone number to receive one-time passcodes during the account creation or authentication process. It’s unlikely this phone is tied to their identity, however. Instead, they use prepaid phones, virtual phone numbers (voice over internet protocol) or spoofed phone numbers so they can’t be linked to the illegal activity.
With high-quality fake IDs (easily purchased online), they present ‘proof’ of their synthetic identities to slip past initial screenings. Once enrolled, bad actors can use fraudulent accounts to make purchases with stolen credit cards, open new lines of credit, launder money or conduct other financial schemes.
So back to the initial question, how do you know the person onboarding with your business is a real, legitimate customer? In a world of Frankensteins, companies need a layered approach to identity verification and data validation, which can be further enhanced by orchestration and fraud detection that continually adapts to today’s complex and evolving tactics. In this article, we’ll explain what’s needed and why.
Secure onboarding with data validation and identity proofing
If you’ve read recent Gartner reports on identity proofing (ID and selfie analysis) and identity affirmation (also called data validation), you already know the importance of a layered approach to properly verify identities during the onboarding process. This combination also ensures the best user experience (UX) possible. So let’s cover the basics of what these solutions do.
Identity verification, aka identity proofing, analyzes the user’s ID document and selfie in order to quickly verify:
- The real-world identity exists
- The user’s government-issued ID is authentic and valid
- The selfie of the individual is a legitimate, live person
- The user is the same person associated with the verified ID
A few of the many challenges when verifying identities:
- High-quality fake IDs are sold online in plain sight, not just the dark web
- New fake ID services offer image editing tools; users add their own photos
- Generative AI can be used to create or edit images that look like genuine IDs
- Document tampering and use of compromised IDs are hard to detect
- Government ID templates (holograms, fonts, formats, etc.) change year to year
- Requiring customers to provide an ID and selfie adds friction to the UX
Data validation, aka identity affirmation, runs in the background to instantly verify:
- The personal data users provide is accurate and authentic
- The data is strongly associated and linked to the claimed identity
- The user’s device and location are associated with the identity
- The individual is not on a global sanctions watch list
A few of the challenges when validating data:
- Synthetic identities with enough ‘real’ data can trick basic validation methods
- DIY integrations with data validation sources are difficult to set up & maintain
- Know-your-customer (KYC) compliance is ever changing and varies by region
- Results from different sources may conflict, so you need a way to reconcile discrepancies
When you understand the capabilities and challenges of identity verification and data validation on top of the complexity of the fraud landscape, it becomes clear why you need both solutions to secure onboarding.
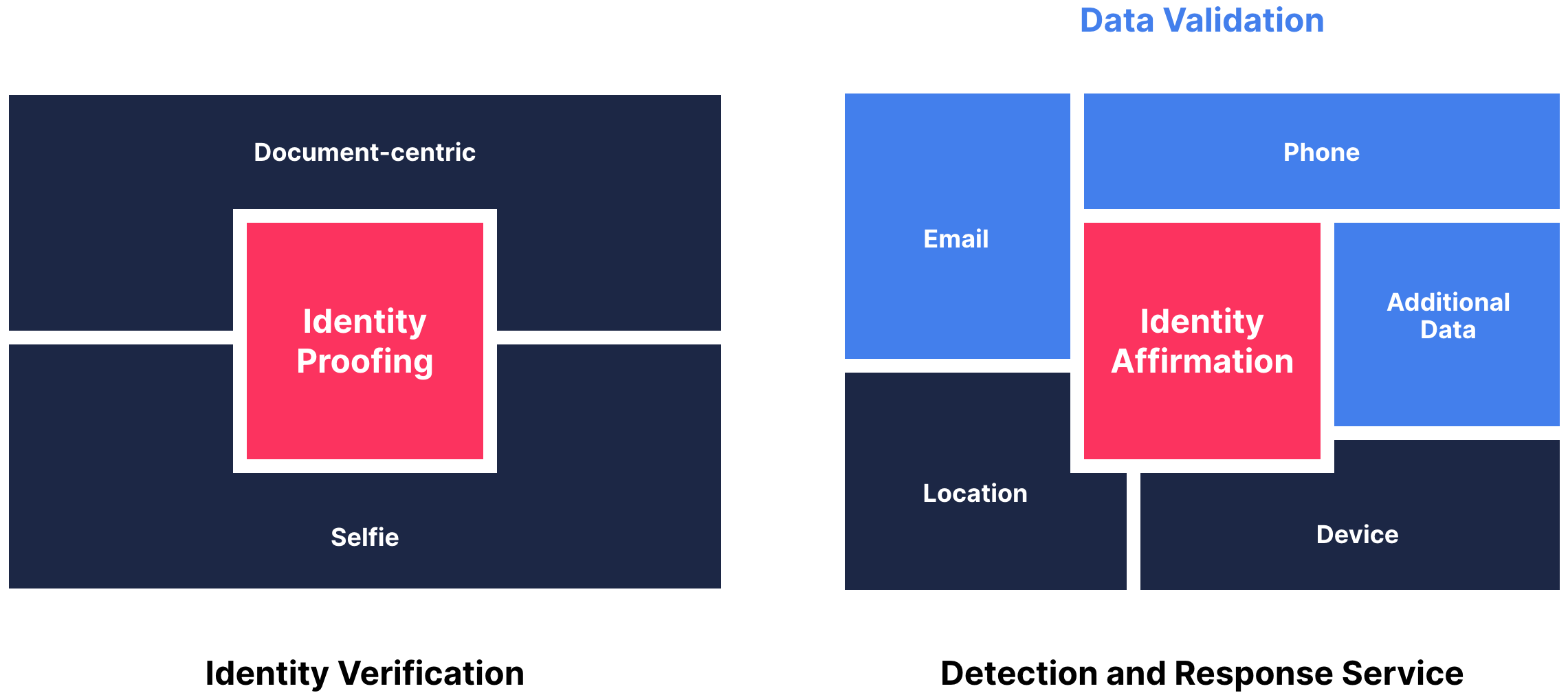
Synergies of ID verification + data validation
The adage ‘better together’ may be trite, but it’s never more true. Identity verification and data validation complement each other and can work seamlessly together if natively built within the same platform.
The majority of legitimate customers will satisfy the risk tolerance or threshold with data validation alone. In these cases, you’ll passively validate the identity without adding friction; customers simply follow a typical enrollment flow, entering their personal information. In the event data validation returns mixed or negative results, you can then invoke identity verification for ID and selfie analysis, giving the user a second chance to prove their identity.
In some industries, however, KYC regulatory compliance requires document-based ID verification as well as background checks and data validation. Financial institutions or any business that conducts high-risk transactions typically need both identity verification and data validation — even if data validation determines the personal information is valid and strongly associated with the identity.
Businesses must assess how much confidence they need in the user’s identity and balance that with the UX they want to provide, which will vary, depending on the industry and use case. Gartner suggests asking yourself what level of assurance you need for your business and the specific context. This will rarely lead you to an either/or answer, but instead, you’ll want to use both identity verification and data validation to secure onboarding without unnecessary friction.
Advanced detection for advanced fraud
Not only do you need both solutions to work in concert, but you need highly advanced identity verification and aggregated data validation services that are smart enough to assess every small but significant detail. That’s exactly what you get with Transmit Security Identity Verification Services and data validation capabilities.
Transmit Security is the only vendor offering platform-native identity proofing and data validation within a complete CIAM platform — delivering full platform synergies.
Transmit Security Identity Verification – AI-driven identity and document verification determine if the individual and their ID are legitimate with a high level of confidence. This automated service is smart enough to catch high-quality fake IDs, leveraging advanced capabilities:
- Deep document inspection – examines every detail to discern if the ID is authentic and unaltered, matching dates with templates, fonts, holograms and dozens of security features. It uses over 150 weighted analyses and machine learning algorithms to detect synthetic or tampered IDs.
- Biometric matching – compares the selfie and ID photo to verify the person in the document is the same individual who is trying to enroll. It’s trained on over 400k faces, analyzing race, gender, age-match and dozens of other details.
- Liveness detection – ensures the person in the selfie is a live person, not a video or photo and is sensitive enough for micro-movements like blinking.
- Global coverage – supports 10,000+ government documents and is kept up to date, a massive undertaking no company wants to do on their own.
- Up-to-date threat detection – Transmit Security researchers analyze new attack methods and apply their findings when they first emerge, immediately updating machine learning and AI algorithms to catch new tactics.
- Native identity decisioning – enables you to create and orchestrate validation flows and rules to automate decisioning — without any coding.
Transmit Security’s data validation capabilities – prevents account opening fraud by assessing the validity of data users submit when they enroll. It’s automated and instant — to stop fraud before it begins. For trusted customers, you’ll secure and expedite onboarding with an easy, welcoming experience.
- All you need in a single API – aggregates the leading data sources to give you global and regional coverage. An easy-to-implement service saves you from having to vet, integrate and maintain hundreds of data sources.
- Pre-built, customizable use cases – allows you to select the sources you want to use in order to check the name, address, email, phone number, DoB and SSN are valid and strongly associated with the identity.
- Passive validation – runs in the background — without asking customers to take extra steps adds friction that may lead to drop-offs.
- Reputation services – check the user’s email and phone number reputation.
- Device intelligence – checks the geo-location of a mobile phone device to ensure it aligns with the user’s claimed address.
- Instant background checks – scans AML and PEP watchlists, credit bureaus and anything needed for KYC
- Simultaneous validation – runs all of these checks and performs knowledge-based authentication simultaneously, so you don’t need to worry about speed and aggregation.
- Native identity decisioning – enables you to create and orchestrate validation flows and rules to automate decisioning — without any coding.
- Data correlation – reconciles discrepancies from different sources. Runtime rules processes the results, delivering decisions directly to your apps.
Start improving your customer’s experience and prevent synthetic fraud that’s designed to circumvent security measures. Leading-edge Identity Verification Services and data validation capabilities deliver a better together defense against today’s most deceptive Frankenstein fraud and fake IDs.



