Account takeover (ATO) fraud increased 354% in 2023, a harsh reality that’s motivating companies to fortify their defenses. But to prevent fraud losses, many organizations resort to blunt security measures, like asking customers to authenticate again and again. In many cases, consumers must log in with multi-factor authentication (MFA) and later re-authenticate if they want to use a new device, call support, change account details, recover their account, perform large transactions or do anything that poses risk.
The problem with this approach is twofold: 1) it leaves security gaps — a void — between each authentication event; and 2) customers feel like they’re trapped in a labyrinth where they bump into barriers at every turn. Why blindly challenge customers when it does nothing to prevent ATO fraud during active sessions? After all, authenticating the user only establishes trust at a single point in time.
Fraudsters take advantage of this by hijacking active sessions, spoofing user devices, infecting them with malware and playing other tricks. Plus, hackers continually innovate — and sell — new tactics to evade standard defenses.
Adding multiple, disparate anti-fraud tools to close the security gaps creates even more complexity and friction without doing enough to strengthen security. This blog post covers these challenges and explains how a unified risk-based authentication platform prevents ATO fraud and improves the user experience (UX) while significantly reducing complexity and costs.
Why risk-based authentication?
Frequently challenging customers with one-size-fits-all authentication spoils the UX and does nothing to mitigate risk in the span of time between authentication challenges.
Enter: risk-based authentication (RBA). This method of dynamic authentication assesses the level of risk and trust associated with a user’s request and adapts the authentication requirements in real time. A high risk score can trigger stronger authentication methods, while a high level of trust may give customers access without having to reauthenticate.
The effectiveness of RBA relies heavily on the strength of anomaly detection, data analysis and the algorithms used to determine risk scores. For accurate results, RBA must offer a full range of authentication methods and identity orchestration plus real-time fraud prevention that provides continuous monitoring, behavioral biometrics, device fingerprinting and malware detection. Anything less will fall short of optimal outcomes.
Navigating UX and security pitfalls
To prevent account fraud without frustrating customers, RBA risk ratings must be highly accurate. This is difficult to achieve and requires a full understanding of the broad set of challenges:
- Multi-vendor complexity and cost: Stitching together multiple identity and anti-fraud tools, each with a narrow set of capabilities, results in fragmented experiences and inconsistent risk scoring. Security teams struggle with difficult integrations, data silos and blind spots, further complicated by black box AI models. Complexity and costs continue to rise as you build layers of heuristic rules to detect new fraud MOs.
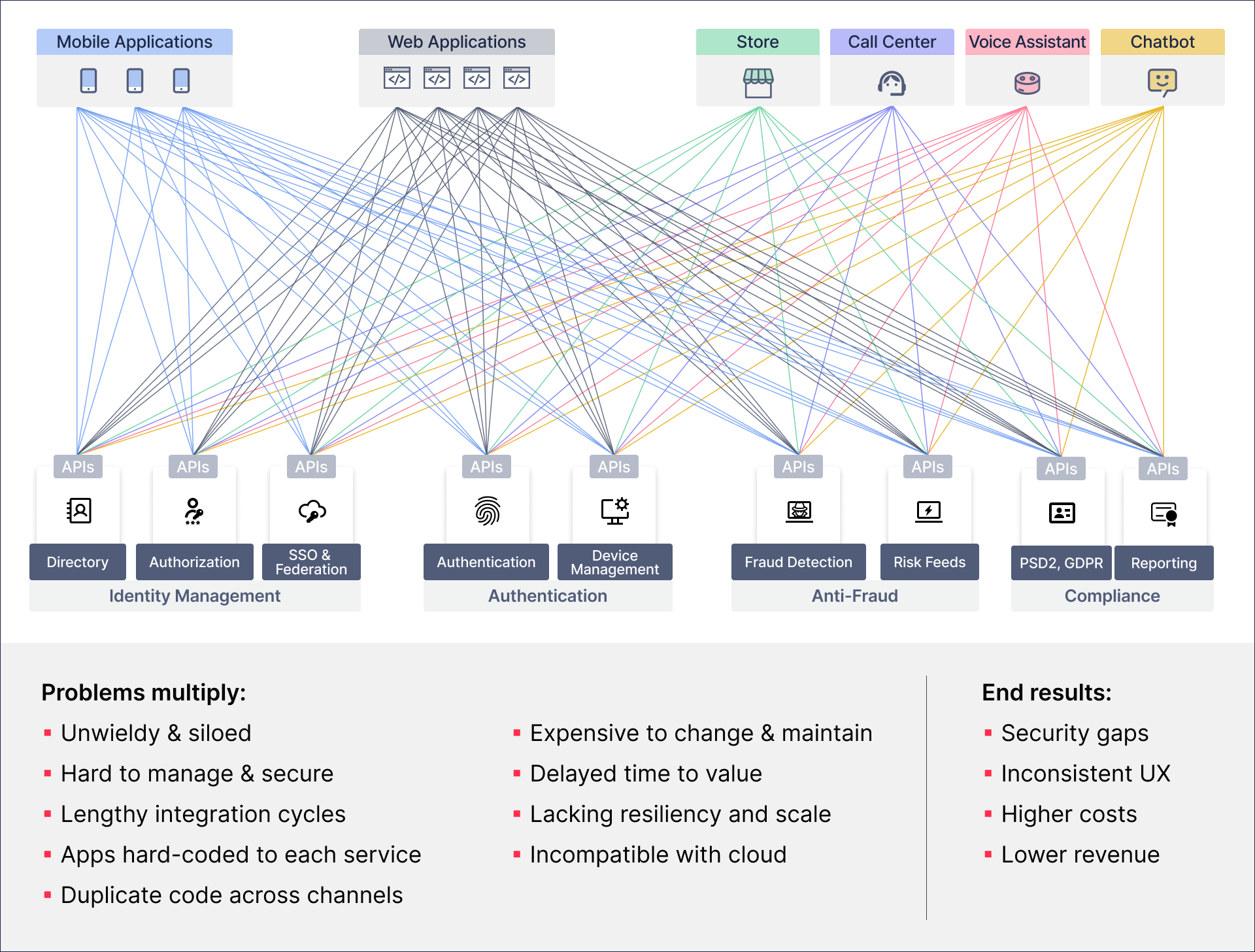
- Detection errors: Disparate anti-fraud tools are incapable of assessing the full context of a user’s access request. Fraudsters know this and continually evolve their tactics, even mimicking user behavior to evade detection. Analyzing a narrow set of signals leads to mistakes. False positives disrupt customers, and false negatives result in fraud.
- Piecemeal authentication: Adding passkeys or passwordless MFA and piecing this together with different solutions for SMS OTPs, email magic links, security questions and/or social logins creates more complexity. For starters, different login methods establish different levels of trust. RBA must be able to adapt step-up challenges based on the strength of the initial login method. Every form of authentication must work in concert to raise the level of assurance as needed.
- Vulnerable credentials: Bad actors use fraud toolkits, malware, bots and social engineering to steal, intercept, crack and phish passwords, security questions, one-time passcodes (OTPs) and email magic links. Even phishing-resistant passkeys need added security to prevent key leakage. There are also cases when passkeys or ‘passwordless’ must fall back on passwords and other methods that pose risk.
- Poor customer experiences: A cumbersome MFA process can create more friction than customers will tolerate. As you invoke more authentication challenges or limit session length, you’re adding barriers and complexity that lead customers to call support or drop off entirely. Detection errors that result in fraud further degrade UX.
Risk-based authentication with Transmit Security
Transmit Security provides the only risk-native authentication solution on the market, giving customers the most secure and seamless RBA experience. With the contextual intelligence to mitigate risk or elevate trust in real time, Transmit Security prevents highly deceptive ATO fraud and removes friction from the trusted customer’s path.
A complete, out-of-the-box RBA platform: Removes IT complexity and costs with a full range of authentication methods (including passkeys and true passwordless MFA), real-time fraud prevention, journey-time orchestration and identity management — in a single, unified solution:
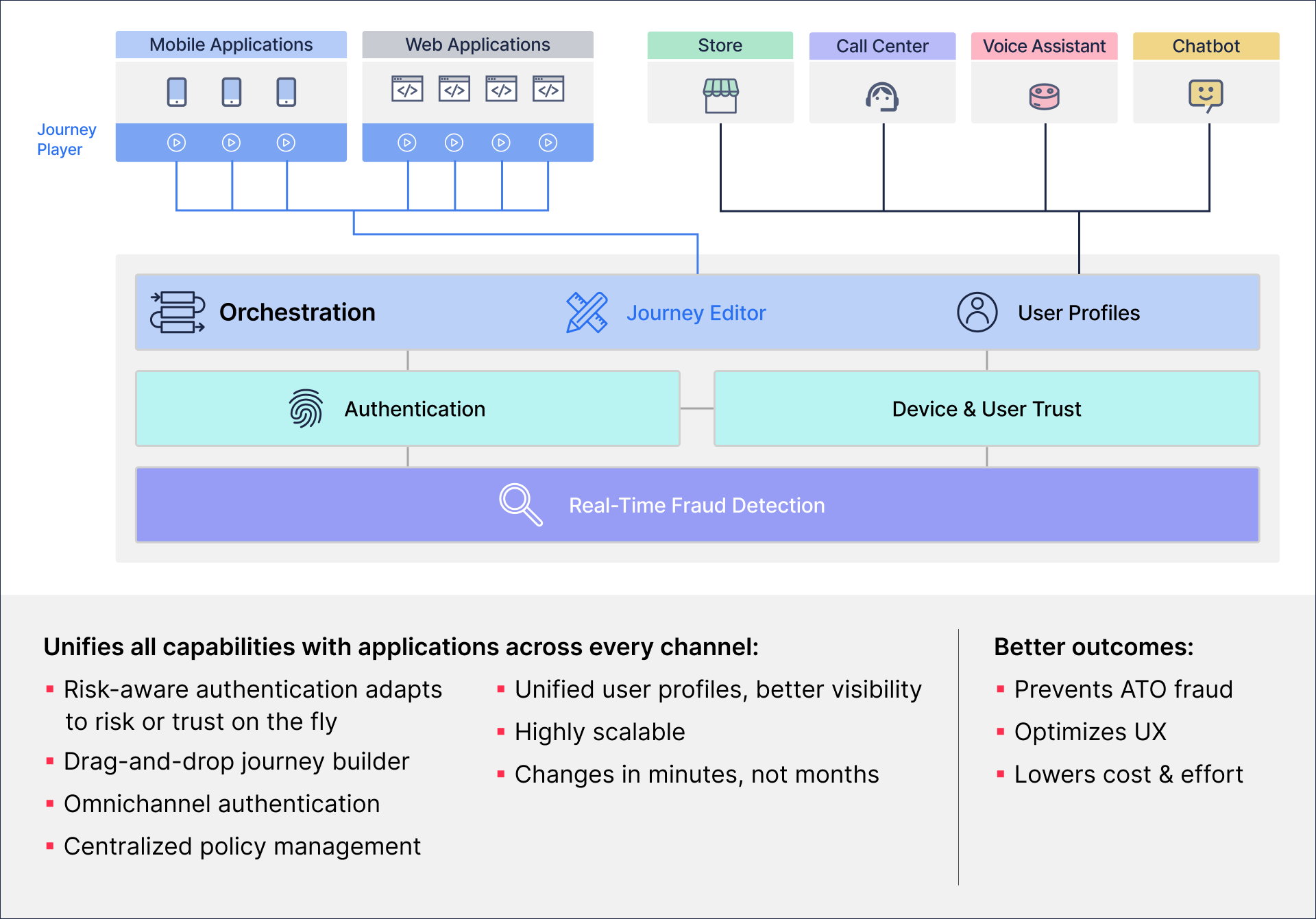
RBA adapts to all scenarios: Together, risk-aware authentication and journey-time orchestration adapt the authentication experience in real time. To achieve this, AI-driven fraud detection runs in the background throughout the login process, examining risk, trust, fraud, bots and behavior to formulate a recommendation: Allow, Challenge or Deny. Orchestration then triggers the appropriate user flow, for example:
- If a user logs in with an OTP or password (a single factor), there’s an elevated risk. But if our fraud detection engine determines there are no signs of aberrant behavior, and it’s the user’s known device, typical network and a trusted IP address, it could meet your risk tolerance and recommend, “Allow,” granting user access while removing friction.
- By contrast, if your company strict security and compliance requirements, and the recommendation in response to an OTP or password is, “Challenge,” the orchestration engine might prompt the user to authenticate again with non-phishable credentials, like passkeys or passwordless MFA, depending on the capabilities of the user’s device and the journeys you’ve chosen to address every variable.
Leading-edge capabilities: Behavioral biometrics, device fingerprinting, bot detection, ML and AI assess hundreds of signals at all times — to distinguish between good and bad activity. A high risk score invokes authentication challenges, and a high trust score adapts by removing and reducing friction — based on the full context of all that’s happening in the moment and across time.
Transmit Security RBA delivers better outcomes while solving the challenges of detection errors, complexity, costs and friction:
- Reduces false positives and false negatives by 90%
- Reduces bots by 98%
- Improves device fingerprinting accuracy to 99.7% or better
- Reduces friction, CAPTCHA and MFA challenges by 80%
- Reduces complexity & costs with a RBA unified solution
Stop fraud and reward customers with Transmit Security Risk-based Authentication.
Book a meeting with our security experts.



