We are excited to finally announce our extended partnership with Amazon Web Services (AWS)! We’ve teamed together to give you fine-grained, risk-based authorization, combining the capabilities of Amazon Verified Permissions and Transmit Security Detection and Response Services. In this article, we’ll explain what this means for you and why it’s a significant step for enforcing least privilege access — core to the zero trust motto, ‘Never trust. Always verify.’
We’ve been collaborating for months, leading up to the AWS announcement of Amazon Verified Permissions, a prebuilt permissions system that simplifies policy-based access control (PBAC) and is flexible enough to address advanced authorization requirements for custom applications. Verified Permissions enables fine-grained authorization that’s highly effective for determining who has access to what.
Without the right tools, managing and securing account access can feel like navigating a landmine of risk. After all, you have millions of customer accounts, each with its own set of permissions and authorization requirements. Updating these permissions to meet regulations and security requirements is a constant challenge. Hard-coded authorizations are especially difficult to manage.
Amazon Verified Permissions solves these challenges, making it easy to create and manage granular policies. But an access decision is not always a clear ‘Yes’ or ‘No.’ How do you know if an account has been taken over or compromised? Is it really your customer who logged in to begin with?
To answer these questions, you need fine-grained risk-based authorization, and it’s why AWS and Transmit Security are working together to deliver risk-based authorization that’s able to assess the full context of an access request with respect to user activities in the current and previous sessions. In this post, we’ll explain how our solution gives you that context, so you can feel confident in those ‘Yes’ decisions.
Innovative risk-based authorization
Thanks to our collaborative efforts, Transmit Security services now integrate with Amazon Verified Permissions to externalize authorization and monitor risk, triggering the right access decisions in real time. Transmit Security Detection and Response Service collects and analyzes over 100 signals at all times to determine risk and trust across the full identity lifecycle.
The fraud orchestration layer of Detection and Response Services correlates the data and applies machine learning to evaluate telemetry and assess risk and trust access requests. The risk decision requires knowledge of the individual customer’s typical behavior and devices — as a baseline for comparison. If risk appears when a request should otherwise be authorized, the solution conditionally prompts the user to re-authenticate or verify their identity.
How it works
The complexity of accounts today provides bad actors with a larger attack surface, to gain unauthorized access to accounts and resources that are managed by these accounts. In order to close security gaps and verify that the real account owner is the one trying to gain access, you need to apply two methods:
- Deterministic – answers the questions of:
- Who’s the actor?
- Is the actor allowed to do what they are trying to do?
- Dynamic – adds additional user interaction risk and trust context:
- Even if a specific account is eligible to take certain actions, it’s possible for the account to be taken over. At this point, those deterministic checks must be strengthened with additional dynamic risk assessments that weigh the full context and analyze telemetry.
To make the best access decisions in real time, you need both risk-based (dynamic) and fine-grained (deterministic) authorization. By joining forces, Amazon Web Services (AWS) and Transmit Security have created the next generation of risk-based, fine-grained authorization.
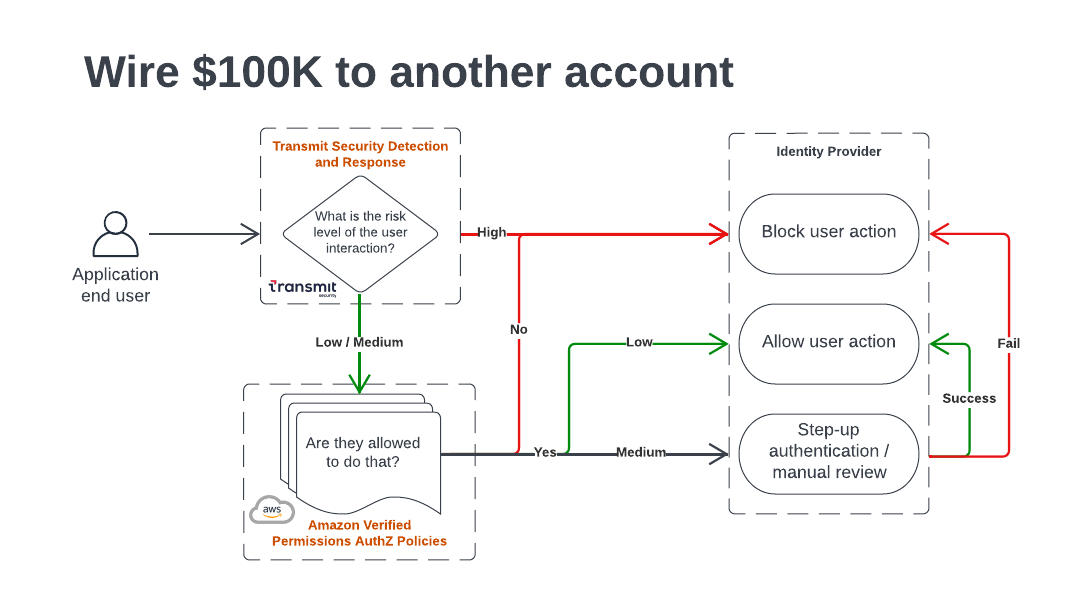
Figure 1: User authorization decisioning
AWS customers can use Amazon Verified Permissions for fine-grained permissions and authorization and leverage Transmit Security to provide risk-based context and recommendations for each authorization request.
Transmit Security is an AWS Partner that provides Fraud Detection and Response and Identity Orchestration Services to the largest enterprises in the world.
Transmit Security Detection and Response
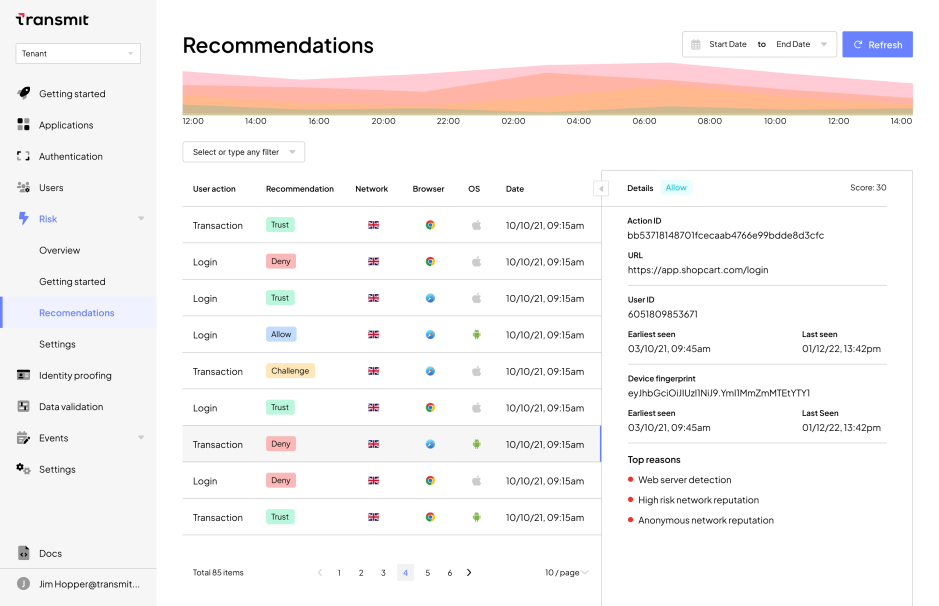
Figure 2: Transmit Security Detection and Response recommendations dashboard
To accurately assess risk, trust, fraud, bot and behavior throughout the identity lifecycle, Detection and Response Services continually analyze:
- Device intelligence – fingerprinting, browser and OS reputation
- Behavioral biometrics – mouse movement speed, typing velocity
- App activity – financial transactions, password resets
- Authentication events – step up, verification
- Global risk signals – activity times and volume
- Network intelligence – IP address reputation, data center activity, residential proxy
At every critical moment in the customer application, the client can fetch a real-time risk score and recommendation (e.g., Allow or Deny) for the specific action (e.g., login, transaction) — empowering you with transparent, out-of-the-box decisioning logic.
“Better together” fine-grained, risk-based authorization
By combining the authorization policies evaluation results by Amazon Verified Permissions and the risk score returned by Transmit Security Detection and Response, security and compliance teams can confidently address the two critical questions to ensure that their application accounts and assets are used in a safe and secure manner:
- Does the current user have the right to do what they want to do?
- Is the context of the user’s interaction with the service legitimate and normal?
Integration snapshot
The following diagram presents an overview of Amazon Verified Permissions + Detection and Response integration flow. View our full article on the AWS Partner Network Blog for a complete step-by-step integration guide.
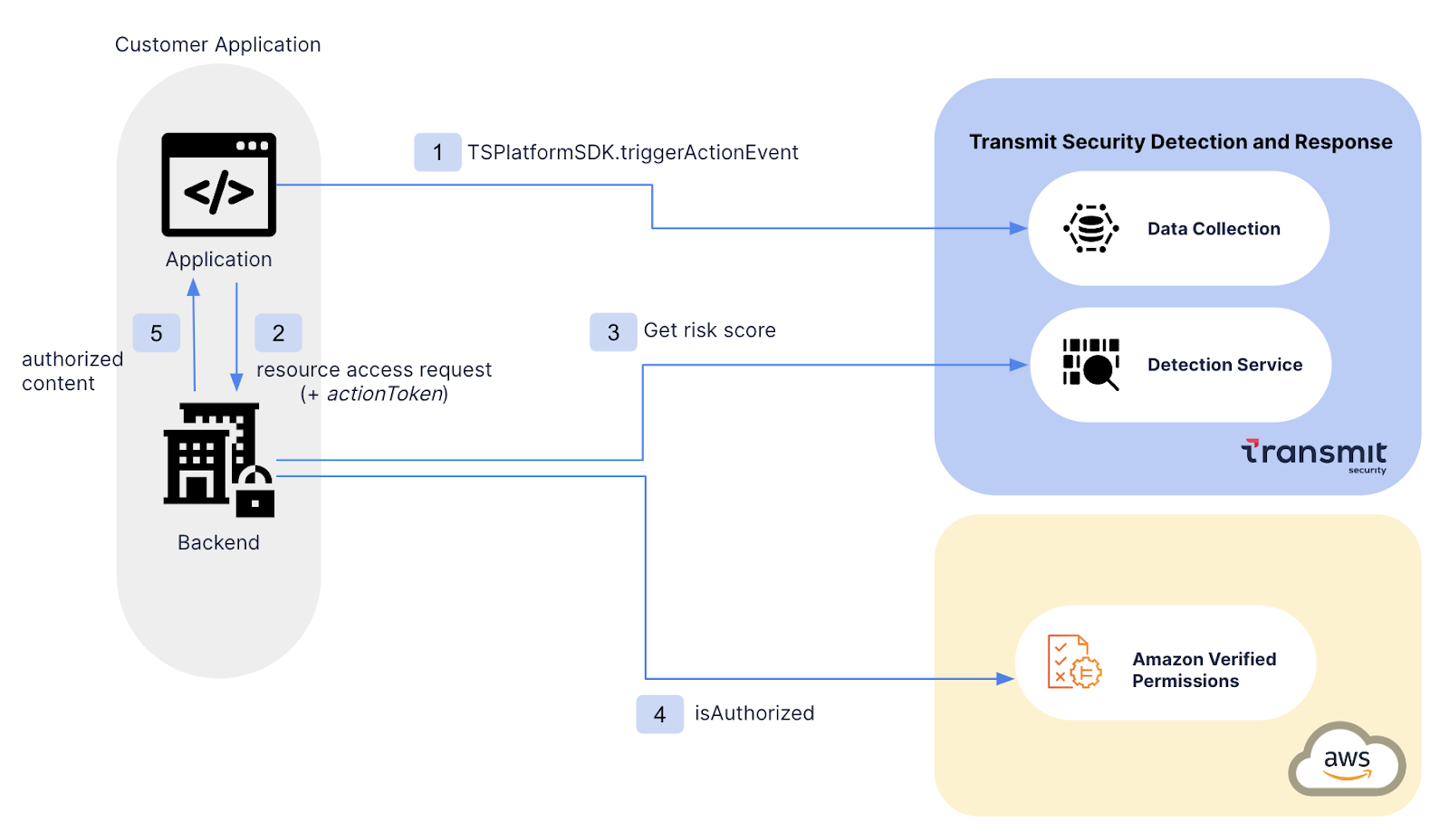
Figure 3: Integration flow
Next-level zero trust
With highly-deceptive account takeover attacks on the rise, risk-based, fine-grained authorization is essential. The combination of Amazon Verified Permissions and Transmit Security Detection and Response empowers developers to:
- Externalize authorizations to:
- Improve security
- Centralize policy administration
- Promote consistency in authorization decisions
- Quickly adapt to changing security requirements or risk
- Provide seamless access by removing friction for trusted customers
- Stop risky requests and affirm zero trust with real-time risk-based authorization
- Arm security teams with the activity logs to investigate risky behavior and anomalies
Security and fraud teams can now extend their safeguards by ensuring not only that the user has the necessary permissions, but that the customer is truly the one who is requesting access.
Learn more about Transmit Security Detection and Response Services and Amazon Verified Permissions to start experimenting with this powerful integration.



